Aktivity „maliming“
Thanks I will check and find a way.
hi
The returnurl(https://st.localhost) must be exists on RedirectAllowedUrls
And you can override the EmailConfirmationModel modal to debug it
Volo.Abp.Account.Pro.Public.Web/Pages/Account/EmailConfirmation.cshtml
Volo.Abp.Account.Pro.Public.Web/Pages/Account/EmailConfirmation.cshtml.cs
hi
You can try to override it on AuthServer
hi
StatusCode: 500,
Please check the logs from Auth server project
hi
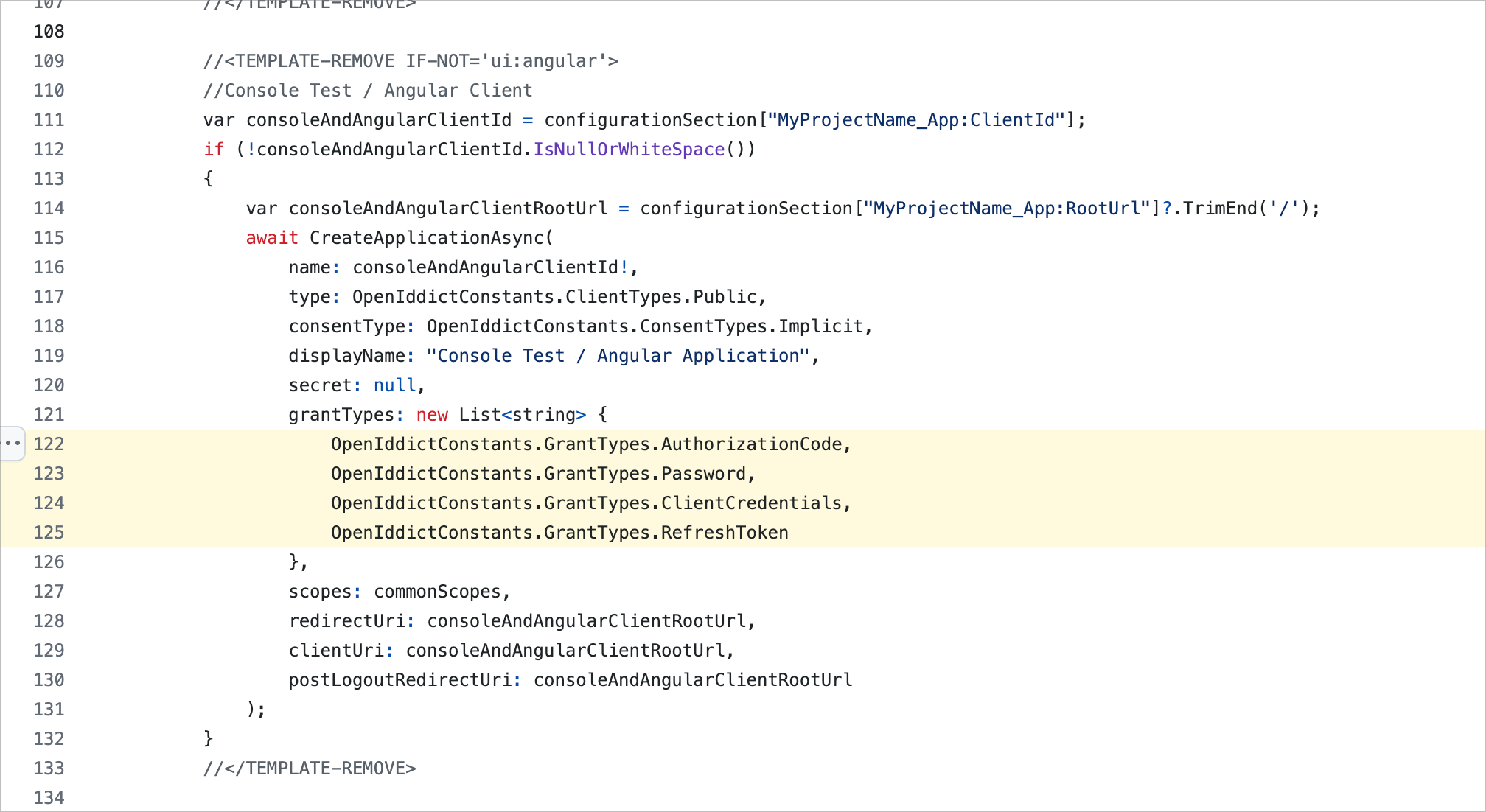
Try to add OpenIddictConstants.GrantTypes.Password to grantTypes
grantTypes: new List<string> //Hybrid flow
{
OpenIddictConstants.GrantTypes.AuthorizationCode,
OpenIddictConstants.GrantTypes.Implicit,
OpenIddictConstants.GrantTypes.Password
},
hi
Can you share full logs of all related requests?
Thanks
liming.ma@volosoft.com
[Dependency(ReplaceServices = true)]
[ExposeServices(typeof(ExternalProviderSettingsHelper))]
public class MyExternalProviderSettingsHelper : ExternalProviderSettingsHelper
{
//...
}
You can check the _currentTenant usage in this class and change it to fit your case.
hi
I don't see why they should match. Please can you explain more?
This is a rule to validate a token, the server will get the issuer from the token and get the host from the HTTP context. eventually try to match them.
1. You can try to set the issuer and reissue a token.
serverBuilder.SetIssuer(new Uri("https://localhost/"));
public override void PreConfigureServices(ServiceConfigurationContext context)
{
var hostingEnvironment = context.Services.GetHostingEnvironment();
var configuration = context.Services.GetConfiguration();
PreConfigure<OpenIddictBuilder>(builder =>
{
builder.AddValidation(options =>
{
options.AddAudiences("MyProjectName");
options.UseLocalServer();
options.UseAspNetCore();
});
});
if (!hostingEnvironment.IsDevelopment())
{
PreConfigure<AbpOpenIddictAspNetCoreOptions>(options =>
{
options.AddDevelopmentEncryptionAndSigningCertificate = false;
});
PreConfigure<OpenIddictServerBuilder>(serverBuilder =>
{
serverBuilder.AddProductionEncryptionAndSigningCertificate("openiddict.pfx", "00000000-0000-0000-0000-000000000000");
serverBuilder.SetIssuer(new Uri(configuration["AuthServer:Authority"]!));
});
}
}
You can configure the TokenValidationParameters to disable to match the issuer and host.
or add https://localhost/ and https://localhost/auth to validissuers
https://learn.microsoft.com/en-us/dotnet/api/microsoft.identitymodel.tokens.tokenvalidationparameters.validissuer?view=msal-web-dotnet-latest#microsoft-identitymodel-tokens-tokenvalidationparameters-validissuer
https://learn.microsoft.com/en-us/dotnet/api/microsoft.identitymodel.tokens.tokenvalidationparameters.validissuers?view=msal-web-dotnet-latest#microsoft-identitymodel-tokens-tokenvalidationparameters-validissuers