- ABP Framework version: v4.2.2
- UI type: MVC
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): Yes
- Exception message and stack trace:
- Steps to reproduce the issue:"
We are currently developing a solution to integrate with Microsoft Graph API. We have challenges on retrieving the Azure AD Token.
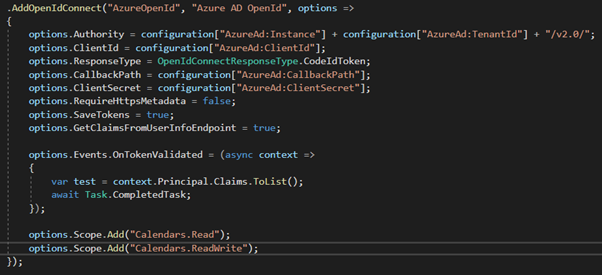
We have configured the Azure AD OpenIdConnect as mentioned in the ABP documentation - https://docs.abp.io/en/abp/2.8/How-To/Azure-Active-Directory-Authentication-MVC#2-alternative-approach-addopenidconnect. We are able to login using Azure AD OpenId but we are stuck on the part to retrieve the Azure AD access token.
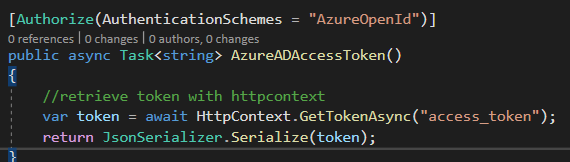
We are able to retrieve the token through the controller method with Authorize Attribute by defining the AuthenticationSchemes. However the token retrieve through this method will replace the bearer token for application and results in the current user to be logged off.
Please advise.
4 Answer(s)
-
0
see https://docs.microsoft.com/en-us/azure/storage/common/storage-auth-aad-app?tabs=dotnet#get-an-access-token-from-azure-ad
-
0
We had tried implementing the provided solution, but we are getting activator chain error when trying to call the controller.
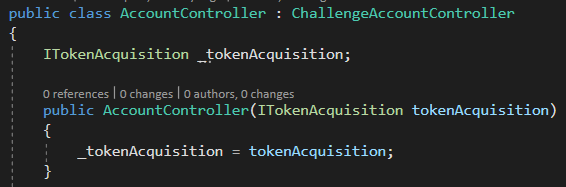
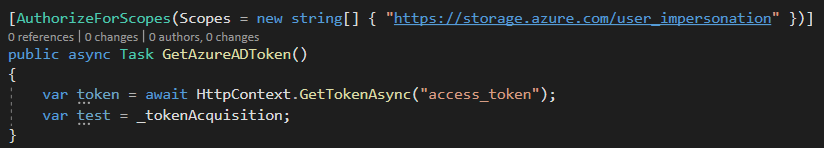
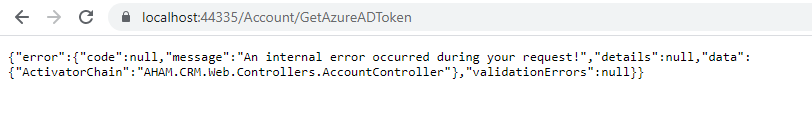 Additionally, is there any way for us to retrieve the token at the Pages or AppServices? Given that the ABP MVC solution is design for the request to be access through Pages instead of Controller.
Additionally, is there any way for us to retrieve the token at the Pages or AppServices? Given that the ABP MVC solution is design for the request to be access through Pages instead of Controller. -
0
Hi,
Is there a solution for this issue?
-
0
Getting access-token from azure-ad is related with Microsoft and completely out of our scope.
However i will try to help you;
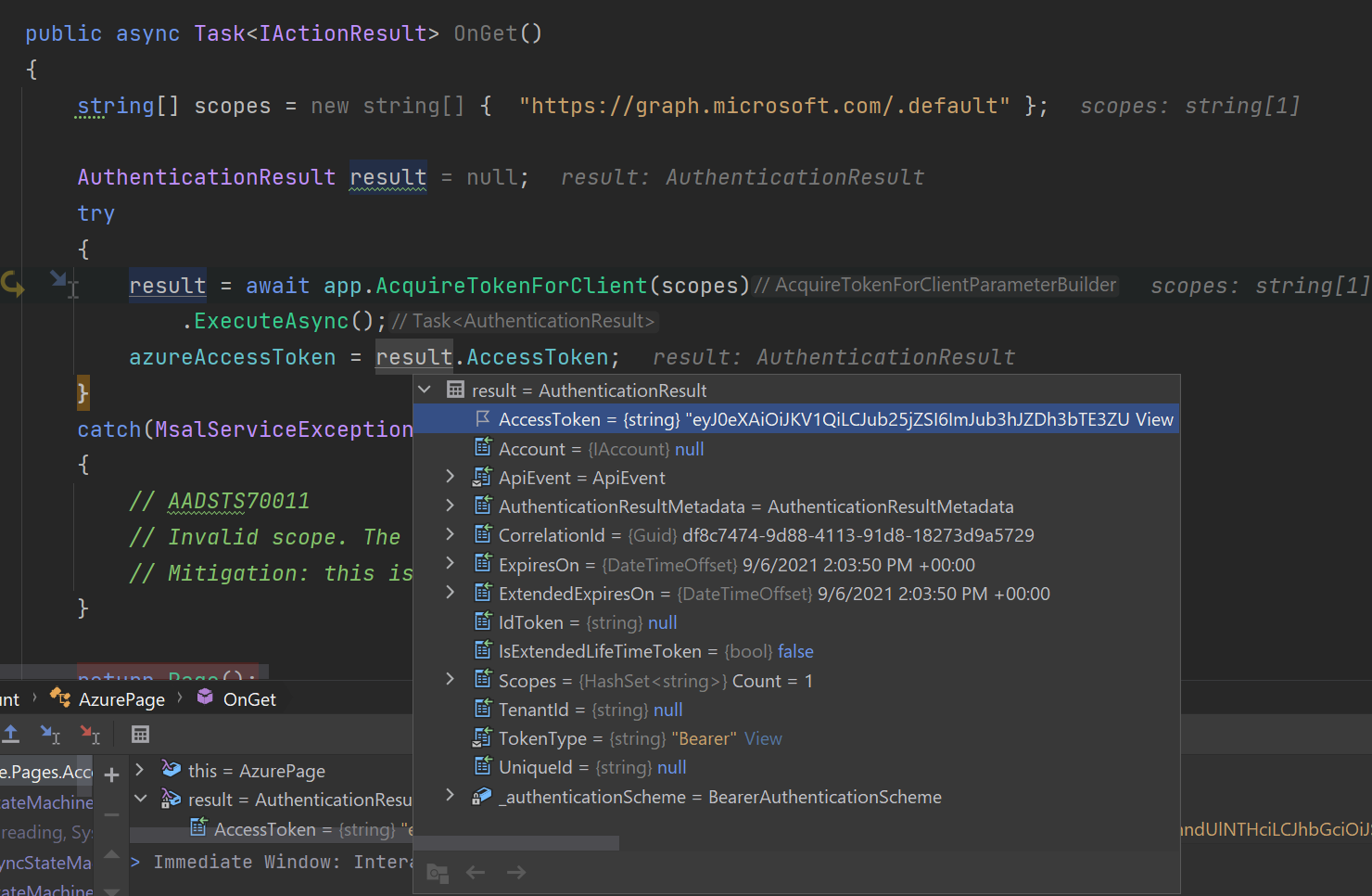
I willl use client credential flow using
ConfidentialClientApplicationBuilderof Microsoft.Identity.Client package.Create a Page something like: <br>
public class AzurePage : PageModel { IConfidentialClientApplication app; private const string clientId = "my-client-id-in-appsettings"; private const string tenantId = "my-tenant-id-in-appsettings"; private const string clientSecret = "my-client-secret-in-appsettings"; public string azureAccessToken = string.Empty; public AzurePage() { string authority = $"https://login.microsoftonline.com/{tenantId}/v2.0/"; app = ConfidentialClientApplicationBuilder.Create(clientId) .WithClientSecret(clientSecret) .WithAuthority(new Uri(authority)) .Build(); } public async Task<IActionResult> OnGet() { string[] scopes = new string[] { "https://graph.microsoft.com/.default" }; AuthenticationResult result = null; try { result = await app.AcquireTokenForClient(scopes) .ExecuteAsync(); azureAccessToken = result.AccessToken; } catch(MsalServiceException ex) { // AADSTS70011 // Invalid scope. The scope has to be of the form "https://resourceurl/.default" // Mitigation: this is a dev issue. Change the scope to be as expected } return Page(); }Result:
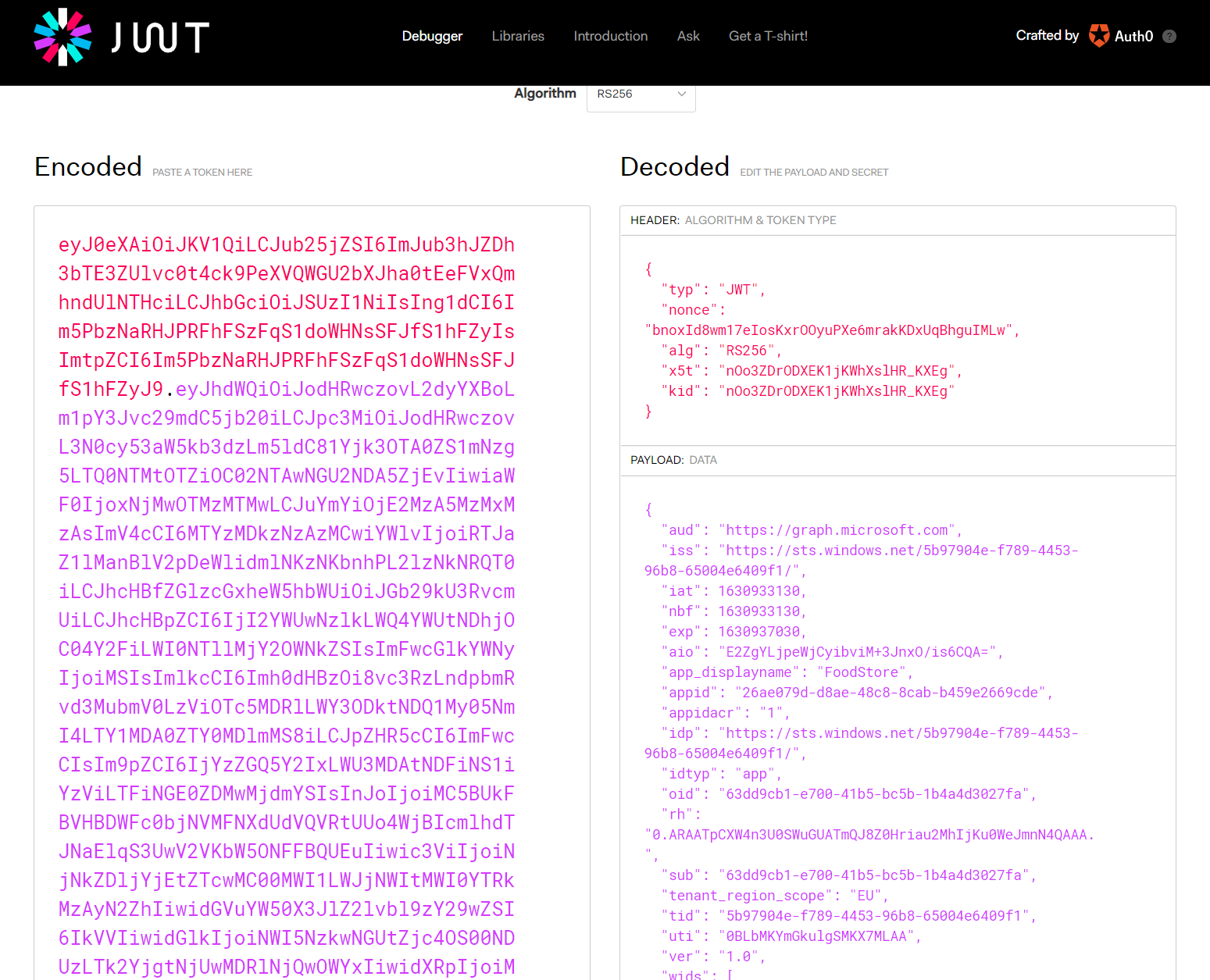
and Jwt.io:
Use
IConfidentialClientApplicationwherever you need.