- ABP Framework version: v7.0.1
- UI type: Angular
- DB provider: EF Core
- Identity Server Separated (Angular)
We would like to implement the logic which implies assigning permissions to a custom role, while such custom role in turn is assigned to a standard role of the system. Could you please advice how can we fulfil such task by means of ABP framework?
41 Answer(s)
-
0
Hi,
This sounds like another version of the user-role:
customRole-role.You can check the implementation code of module Identity: https://github.com/abpframework/abp/tree/dev/modules/identity
Some point:
- Feature management Ui is reusable, and you can use it directly: https://github.com/abpframework/abp/blob/dev/npm/ng-packs/packages/identity/src/lib/components/roles/roles.component.html#L33
- You need to cover the role permission provider to load the permissions of the custom role under the role: https://github.com/abpframework/abp/blob/dev/modules/identity/src/Volo.Abp.PermissionManagement.Domain.Identity/Volo/Abp/PermissionManagement/Identity/RolePermissionManagementProvider.cs#L40
- You need to delete the permission cache when updating and deleting custom roles. for example: https://github.com/abpframework/abp/blob/dev/modules/identity/src/Volo.Abp.PermissionManagement.Domain.Identity/Volo/Abp/PermissionManagement/Identity/RoleDeletedEventHandler.cs
-
0
the question re-opened due the owner's request.
-
0
Looks like I will need to create another table, similar to ABPUSERROLES - to bind bottom-level roles to a top-level role. What I don't like in this approach - there will be no difference between both types of roles (just role name encoded in a special way) - ABPROLES does not have some suitable fields for this purpose: it needs to be allowed to assign a bottom-level role to a top-level role, but not vice-versa.
-
0
ABPROLES does not have some suitable fields for this purpose
No such fields, you can consider to extending entities: https://docs.abp.io/en/abp/latest/Customizing-Application-Modules-Extending-Entities
-
0
ABPROLES does not have some suitable fields for this purpose
No such fields, you can consider to extending entities: https://docs.abp.io/en/abp/latest/Customizing-Application-Modules-Extending-Entities
Ok, thanks. We will consider it. Please, do not close the ticket though, we might come up with other questions - the implementation is in progress...
-
0
BTW, what the ABP tables with "_SAVE" suffix are for? E.g., I can see ABPUSERROLES and ABPUSERROLES_SAVE... the structure is the same...
-
0
Hi
Sorry,I didn’t quite understand what’s you mean.
As far as I know there is no ABPUSERROLES_SAVE.
Can you explain it in detail?
-
0
-
0
ABP doesn't create tables with a
_SAVEsuffix. I guess your team is creating backups of important tables. -
0
I can see there are
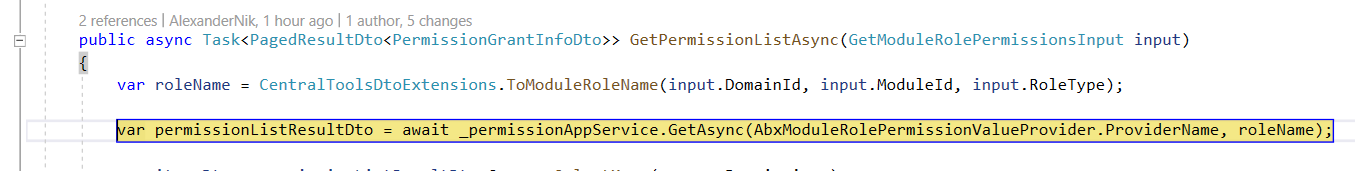
PermissionValueProviderandPermissionManagementProviderABP providers. Do I need to create both? I did it and added them to my domain module like so:public override void ConfigureServices(ServiceConfigurationContext context) { Configure<AbpPermissionOptions>(options => { options.ValueProviders.Add<AbxModuleRolePermissionValueProvider>(); }); Configure<PermissionManagementOptions>(options => { options.ProviderPolicies.Add(AbxModuleRolePermissionValueProvider.ProviderName, AbxModuleRolePermissionValueProvider.ProviderName); // "MR" options.ManagementProviders.Add<AbxModuleRolePermissionManagementProvider>(); }); ... }However, when I reference provider name (AbxModuleRolePermissionValueProvider.ProviderName) via DI-ed ABP
IPermissionAppServicein my configuring page of the projectI am getting the following error:
No policy found: 'MR'
-
0
You need to define permission for AbxModuleRolePermissionValueProvider
- https://github.com/abpframework/abp/blob/dev/modules/identity/src/Volo.Abp.Identity.Application.Contracts/Volo/Abp/Identity/IdentityPermissionDefinitionProvider.cs#L23
- https://github.com/abpframework/abp/blob/dev/modules/identity/src/Volo.Abp.PermissionManagement.Domain.Identity/Volo/Abp/PermissionManagement/Identity/AbpPermissionManagementDomainIdentityModule.cs#L21
-
0
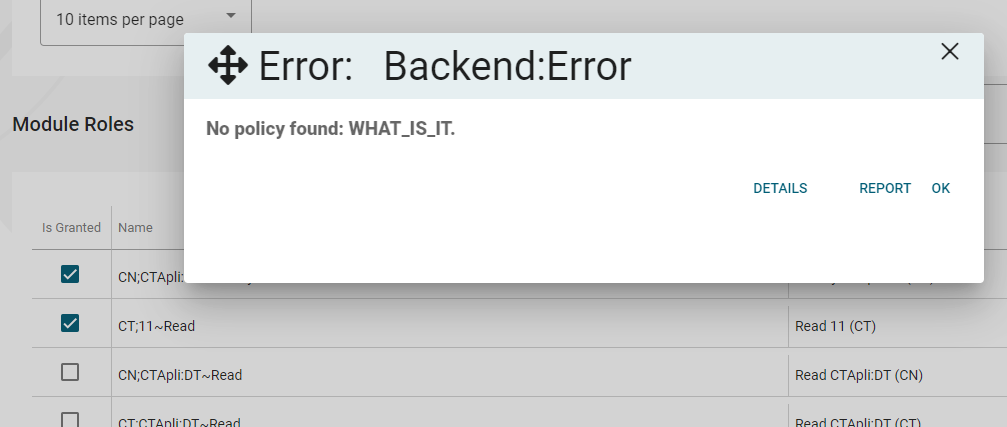
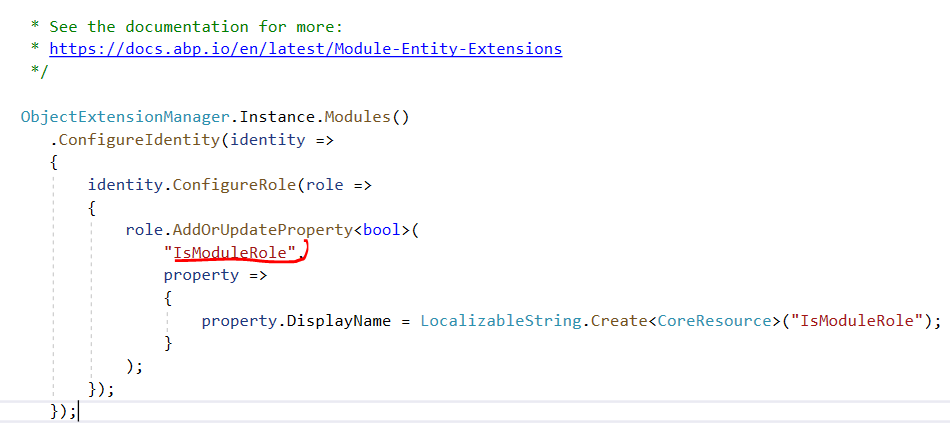
Thank you. OK - on
Application.Contractslayer i've createdAbxModuleRolePermissionDefinitionProviderwhere I defined all "so-called" permissions (according to our requirements - second-level roles):public class AbxModuleRolePermissionDefinitionProvider : PermissionDefinitionProvider { public override void Define(IPermissionDefinitionContext context) { var currentUser = context.ServiceProvider.GetService<ICurrentUser>(); if (currentUser.IsAuthenticated) { var moduleRoleGroup = context.AddGroup(ModuleRolePermissions.GroupName, L("Permission:ModuleRoleManagement")); var moduleRoleAppService = context.ServiceProvider.GetService<IModuleRoleAppService>(); var moduleRoles = moduleRoleAppService.GetModuleRolesAsync(new GetModuleRolesInput()).Result; for (var i = 0; i < moduleRoles.Items.Count; i++) { moduleRoleGroup.AddPermission(moduleRoles.Items[i].Name).WithProviders("MR"); } } } private static LocalizableString L(string name) { return LocalizableString.Create<CoreResource>(name); }I also put the line related to policies into Module:
Configure<AbpPermissionOptions>(options => { options.ValueProviders.Add<AbxModuleRolePermissionValueProvider>(); }); Configure<PermissionManagementOptions>(options => { options.ProviderPolicies[AbxModuleRolePermissionValueProvider.ProviderName] = "WHAT_IS_IT"; options.ManagementProviders.Add<AbxModuleRolePermissionManagementProvider>(); });And this list is successfully loaded on my page (see the grid below). But nevertheless, when I try to update the permissions with the code in the first post, I'm getting the same error.
-
0
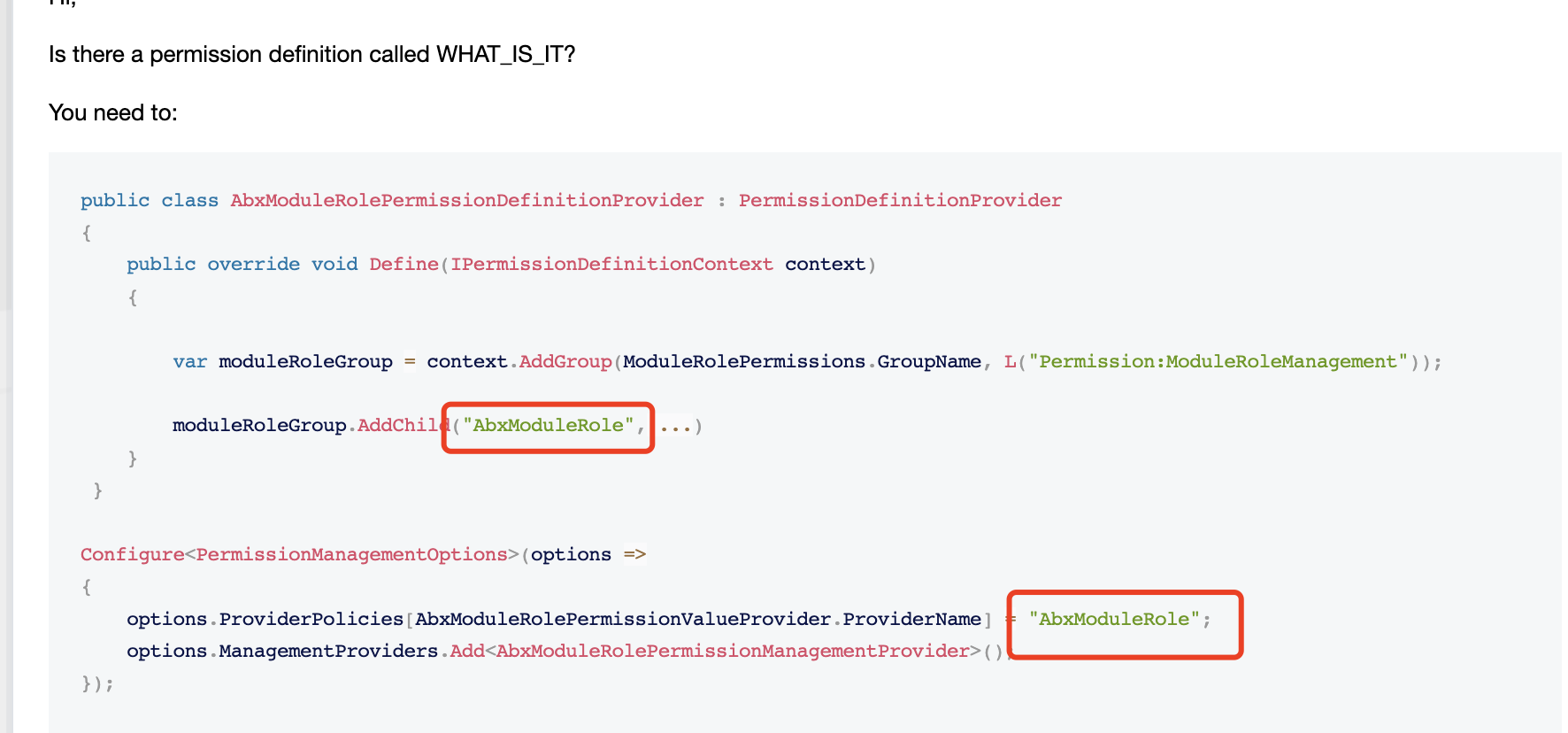
Hi,
Is there a permission definition called WHAT_IS_IT?
You need to:
public class AbxModuleRolePermissionDefinitionProvider : PermissionDefinitionProvider { public override void Define(IPermissionDefinitionContext context) { var moduleRoleGroup = context.AddGroup(ModuleRolePermissions.GroupName, L("Permission:ModuleRoleManagement")); moduleRoleGroup.AddChild("AbxModuleRole",....) } } Configure<PermissionManagementOptions>(options => { options.ProviderPolicies[AbxModuleRolePermissionValueProvider.ProviderName] = "AbxModuleRole"; options.ManagementProviders.Add<AbxModuleRolePermissionManagementProvider>(); }); -
0
Oh, was a bit unexpected, but now I understand. I need a "root" permission definition - I cannot assign my permissions straight to the group:
{ ... var rolesPermission = moduleRoleGroup.AddPermission(ModuleRolePermissions.SubGroupName, L("Permission:ModuleRoles")).WithProviders("MR"); ... } { ... options.ProviderPolicies[AbxModuleRolePermissionValueProvider.ProviderName] = "ModuleRoles"; //TODO: Replace with constant ModuleRolePermissions.SubGroupName ... }Regarding what you have said in the very beginning:
You need to cover the role permission provider to load the permissions of the custom role under the role
do I need to REPLACE some ABP providers (instead of adding my own ones)? What I'm going to do eventually is to replace ABP "Permissions" dialog completely. At the same time, I want to retain as much existing code as possible. I.e. I'm extending Role Management with my two-level role system, but I don't want to break anything which already is functioning at ABP side (if ABP needs traditional approach at some page, it needs to keep functioning).
-
0
Hi,
Ok, you can add your own to do it.
-
0
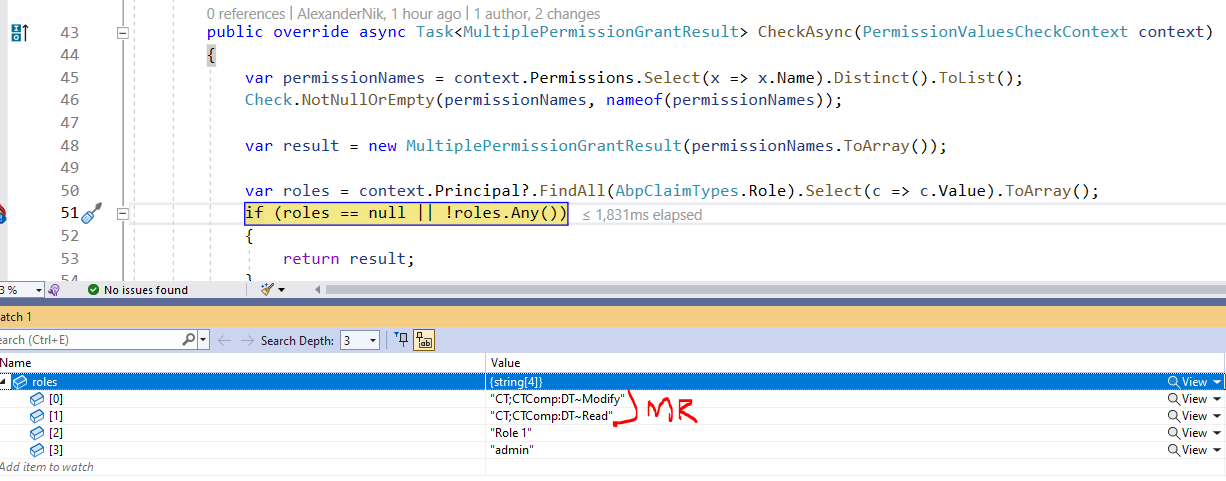
I need to filter out only "MR" roles here:
For this purpose I'm going to use
IsModuleRoleproperty:Since I want to have it accessible in my claims by the time
CheckAsyncis called - I need to add this property there somehow. I've found out there are two ways to do that. I've tried both and in both cases the property is successfully added. But later it disappears and the only property I see inPropertiesishttp://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/ShortTypeName=role(I don't have idea who adds this, but looks like a default property). So my attempts are below:Using Contributor:
public Task ContributeAsync(AbpClaimsPrincipalContributorContext context) { var claimsIdentity = context.ClaimsPrincipal.Identities.First(x => x.AuthenticationType == IdentityAuthenticationType); var roleClaims = claimsIdentity.FindAll(x => x.Type == AbpClaimTypes.Role).ToArray(); if (roleClaims.Length > 0) { var moduleRoles = _identityRoleRepository.GetListAsync().Result.Where(x => x.GetProperty("IsModuleRole", false)).Select(x => x.Name); if (moduleRoles.Any()) { for (var i = 0; i < roleClaims.Length; i++) { if (moduleRoles.Contains(roleClaims[i].Value)) { roleClaims[i].Properties.AddIfNotContains(new System.Collections.Generic.KeyValuePair<string, string>("IsModuleRole", "true")); // I can see the property is present in the claimsIdentity, but in the CheckAsync method - no more... } } } } return Task.CompletedTask; }Using Factory:
public class AbxUserClaimsPrincipalFactory : AbpUserClaimsPrincipalFactory { private static string IdentityAuthenticationType => "Identity.Application"; private readonly IIdentityRoleRepository _identityRoleRepository; public AbxUserClaimsPrincipalFactory ( UserManager<Volo.Abp.Identity.IdentityUser> userManager, RoleManager<Volo.Abp.Identity.IdentityRole> roleManager, IOptions<IdentityOptions> options, ICurrentPrincipalAccessor currentPrincipalAccessor, IAbpClaimsPrincipalFactory abpClaimsPrincipalFactory, IIdentityRoleRepository identityRoleRepository ) : base(userManager, roleManager, options, currentPrincipalAccessor, abpClaimsPrincipalFactory) { _identityRoleRepository = identityRoleRepository; } [UnitOfWork] public async override Task<ClaimsPrincipal> CreateAsync(Volo.Abp.Identity.IdentityUser user) { var principal = await base.CreateAsync(user); var identity = principal.Identities.First(x => x.AuthenticationType == IdentityAuthenticationType); var roleClaims = identity.FindAll(x => x.Type == AbpClaimTypes.Role).ToArray(); var moduleRoles = (await _identityRoleRepository.GetListAsync()).Where(x => x.GetProperty("IsModuleRole", false)).Select(x => x.Name); if (moduleRoles.Any()) { for (var i = 0; i < roleClaims.Length; i++) { if (moduleRoles.Contains(roleClaims[i].Value)) { roleClaims[i].Properties.AddIfNotContains(new System.Collections.Generic.KeyValuePair<string, string>("IsModuleRole", "true")); // I can see the property is present in the claimsIdentity, but in the CheckAsync method - no more... } } } return principal; } }
Probably here the
Propertiesis occasionally replaced with a new collection?public class AbpClaimsMapMiddleware : IMiddleware, ITransientDependency { public async Task InvokeAsync(HttpContext context, RequestDelegate next) { var currentPrincipalAccessor = context.RequestServices .GetRequiredService<ICurrentPrincipalAccessor>(); var mapOptions = context.RequestServices .GetRequiredService<IOptions<AbpClaimsMapOptions>>().Value; var mapClaims = currentPrincipalAccessor .Principal .Claims .Where(claim => mapOptions.Maps.Keys.Contains(claim.Type)); currentPrincipalAccessor .Principal .AddIdentity( new ClaimsIdentity( mapClaims .Select( claim => new Claim( mapOptions.Maps[claim.Type](), claim.Value, claim.ValueType, claim.Issuer ) ) ) ); await next(context); } } -
0
Hi,
The claim Properties not working with JWT.
You can try to add new claims:
foreach(var moduleRole in ModuleRoles) { identity.AddClaim(new Claim("ModuleRole", moduleRole.Name)); } -
0
Thank you. It works.
I now have the following questions:
a) After I create "MR" roles on one page - I navigate to the other page, where I am going to assign "MR" roles (= permission definitions with "MR" provider, as we discussed above) to an ordinary role. Alas, I cannot do that until I relogin the user. Do I need to manually add the created role:
var moduleRole = new IdentityRole(GuidGenerator.Create(), roleName, CurrentTenant.Id) { IsDefault = false, IsPublic = false }; moduleRole.ExtraProperties.Add("IsModuleRole", true); var newModuleRole = await _identityRoleRepository.InsertAsync(moduleRole, true);to Definition Store before trying to bind it to an ordinary role (
roleName):await _permissionAppService.UpdateAsync("MR", roleName, new UpdatePermissionsDto { Permissions = input.Permissions });?
The above is happening because the following method returns null for
moduleRole.Nameuntil relogin:var permission = await PermissionDefinitionManager.GetOrNullAsync(permissionName);b) I'd like to clarify: in which cases do I need to implement own
PermissionManagementProvider? It has the same methods as ValueProviders,CheckAsync...c) If I modify the module roles assigned to an ordinary role - I want to modify the corresponding "moduleRole" claims. How and where to do that efficiently (possibly caching instead of pulling from DB each time) without user relogin? I think you might have used similar mechanism already for your data. I'd prefer to update the accessible pages (and APIs) even if the page in the Angular app is reloaded; Please keep in mind, that on one hand - we are talking about ABP roles (which differ from ordinary roles only by extra field), on other hand they are permission definitions for "MR" provider;
d) will
permissionServive.getGrantedPolicyor*abpPermissiondirective in Angular work for my "MR" permissions in the same way as it work for ordinary "R" permissions?Sorry for long posts - I'm trying to find the answers myself, but it's just too much coming up during this development.
-
0
a) The above is happening because the following method returns null for moduleRole.Name until relogin: If I modify the module roles assigned to an ordinary role - I want to modify the corresponding "moduleRole" claims. How and where to do that efficiently (possibly caching instead of pulling from DB each time) without user relogin? I think you might have used similar mechanism already for your data. I'd prefer to update the accessible pages (and APIs) even if the page in the Angular app is reloaded; Please keep in mind, that on one hand - we are talking about ABP roles (which differ from ordinary roles only by extra field), on other hand they are permission definitions for "MR" provider;
Because JWT is immutable, you need to re-login to load the roles. You also can reload the current character for each request via Middleware, for example https://support.abp.io/QA/Questions/2090/How-to-clear-cache-for-features
b)
https://docs.abp.io/en/abp/latest/Modules/Permission-Management#permission-management-providers
IPermissionManager uses these providers when you get/set permissions. You can define your own provider by implementing the IPermissionManagementProvider or inheriting from the PermissionManagementProvider base class.
IPermissionManager uses permission value providers when you check if permission is granted.
d) will permissionServive.getGrantedPolicy or *abpPermission directive in Angular work for my "MR" permissions in the same way as it work for ordinary "R" permissions?
I guess it's ok, the Front-end loads permission grant datas from backend
-
0
Thank you for the response. We are moving on.
I'm replacing "Roles" page completely. And here is a strange error. Suddenly I'm getting error on this line:
await _permissionAppService.UpdateAsync(AbxModuleRolePermissionValueProvider.ProviderName, moduleRole.Name, new UpdatePermissionsDto { Permissions = input.Permissions });Volo.Abp.Authorization.AbpAuthorizationException: Exception of type 'Volo.Abp.Authorization.AbpAuthorizationException' was thrown. at Microsoft.AspNetCore.Authorization.AbpAuthorizationServiceExtensions.CheckAsync(IAuthorizationService authorizationService, String policyName) at Volo.Abp.PermissionManagement.PermissionAppService.CheckProviderPolicy(String providerName) at Volo.Abp.PermissionManagement.PermissionAppService.UpdateAsync(String providerName, String providerKey, UpdatePermissionsDto input)
The same code for
RolePermissionValueProvider.ProviderNameworks fine.I'm having all "MR" providers defined: Definition, Management, Value. I had experimental page which used the faulty line and it DID work. Now I can't find anything what could make it stop working and I'm stuck. Do you have suggestions where and what I could check? It looks weird, because permission list is returned properly which means Definition Provider data is OK:
public class AbxModuleRolePermissionDefinitionProvider : PermissionDefinitionProvider { public override void Define(IPermissionDefinitionContext context) { var currentUser = context.ServiceProvider.GetService<ICurrentUser>(); if (currentUser.IsAuthenticated) { var moduleRoleGroup = context.AddGroup(ModuleRolePermissions.GroupName, L("Permission:ModuleRoleManagement")); var roleAppService = context.ServiceProvider.GetService<IRoleAppService>(); var moduleRoles = roleAppService.GetModuleRolesAsync(new GetModuleRolesInput()).Result; var rolesPermission = moduleRoleGroup.AddPermission(ModuleRolePermissions.SubGroupName, L("Permission:ModuleRoles")).WithProviders("MR"); for (var i = 0; i < moduleRoles.Items.Count; i++) { rolesPermission.AddChild(moduleRoles.Items[i].Name).WithProviders("MR"); } } } } -
0
-
0
Does the currently logged-in user have the permission?
Well.. I understand now. No, he does not. But since "MR" are not only permissions for ordinary roles, but also they are ABP roles themselves (just having a special extra properties) - I want them to be always available, like any role (not like permission which must be granted). They are never supposed to be checked as permissions (their permissions are). So how to make them always available?
-
0
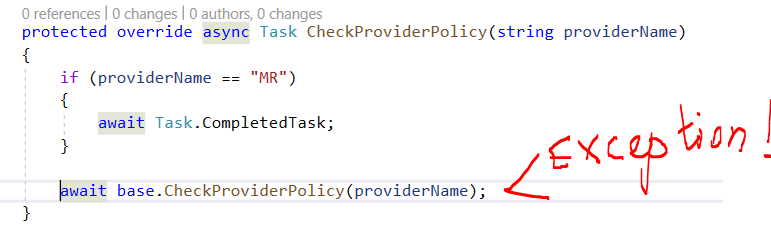
You can ovveride the PermissionAppService:
https://docs.abp.io/en/abp/latest/Customizing-Application-Modules-Overriding-Services#replacing-an-interface
public class MyPermissionAppService: PermissionAppService { ..... CheckProviderPolicy(string providerName) { if(providerName == xxxx) { return; } await base.CheckProviderPolicy(providerName); } } -
0
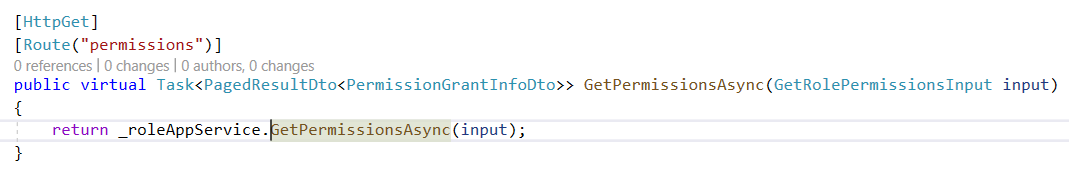
I'm completely lost. I've overridden
PermissionAppService, but it does not resolve the issue - I'm getting this kind of exception even on "R" provider - now I'm trying to READ permissions of an ordinary role:- there is only
Authorizeattribute decorating this method, no permission at all!
The exception happens on
GetAsync:public async Task<PagedResultDto<PermissionGrantInfoDto>> GetPermissionsAsync(GetRolePermissionsInput input) { var role = await _identityRoleRepository.FindAsync(input.Id, false); if (role == null) { throw new BusinessException(DomainErrorCodes.NotFound, _stringLocalizer.GetString("Roles:RoleNotFound")); } var permissionListResultDto = await _permissionAppService.GetAsync(RolePermissionValueProvider.ProviderName, role.Name); !!!EXCEPTION var itemsDto = permissionListResultDto.Groups.SelectMany(x => x.Permissions) .WhereIf(input.IsGranted.HasValue, x => x.IsGranted == input.IsGranted.Value) .WhereIf(!string.IsNullOrWhiteSpace(input.Permission), x => x.Name.IndexOf(input.Permission, StringComparison.OrdinalIgnoreCase) != -1 || x.DisplayName.IndexOf(input.Permission, StringComparison.OrdinalIgnoreCase) != -1); return new PagedResultDto<PermissionGrantInfoDto> { TotalCount = itemsDto.Count(), Items = itemsDto.ComplexOrderBy(input.Sorting).Skip(input.SkipCount).Take(input.MaxResultCount).ToList() }; }Volo.Abp.Authorization.AbpAuthorizationException: Exception of type 'Volo.Abp.Authorization.AbpAuthorizationException' was thrown. at Microsoft.AspNetCore.Authorization.AbpAuthorizationServiceExtensions.CheckAsync(IAuthorizationService authorizationService, String policyName) at Volo.Abp.PermissionManagement.PermissionAppService.CheckProviderPolicy(String providerName) at AbxEps.CentralTools.Permissions.CentralToolsPermissionAppService.CheckProviderPolicy(String providerName) in C:\CT\AbxEps.CentralTools\aspnet-core\src\AbxEps.CentralTools.Application\Permissions\CentralToolsPermissionAppService.cs:line 49 at Volo.Abp.PermissionManagement.PermissionAppService.GetAsync(String providerName, String providerKey)
Probably it is somehow related to my new custom "Roles" page. When I navigate to it, unlike to other pages,
AbxModuleRolePermissionValueProvider=>CheckAsyncis not triggered. I relogged in, but it did not help. ThePermissionProviderseems to be OK, it does contain the required permissions: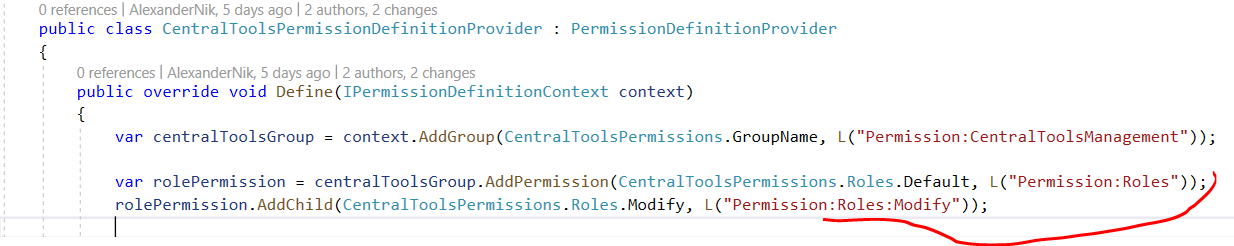 And the user does contain these permissions:
And the user does contain these permissions:
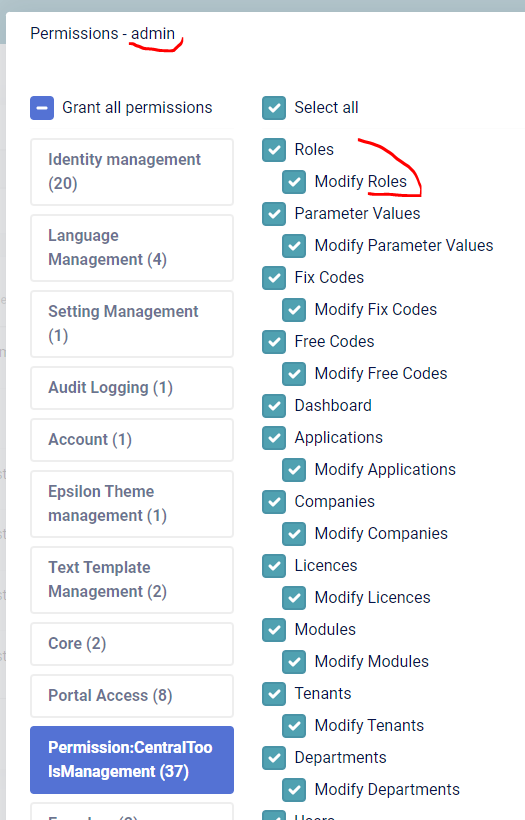
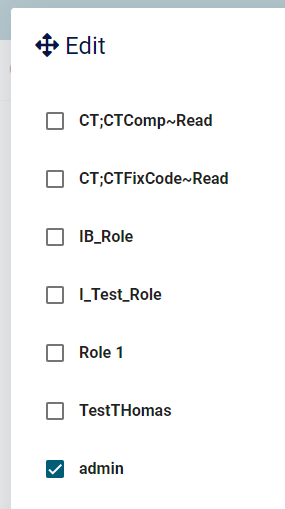
BTW, "admin" is a public role from user's department, not a manually assigned. But it should not be difference, right?
- there is only
-
0
I don't know the code details, can you use a new project to reproduce the problem and share it with me? I will check it shiwei.liang@volosoft.com