أنشطة "jeffbuot"
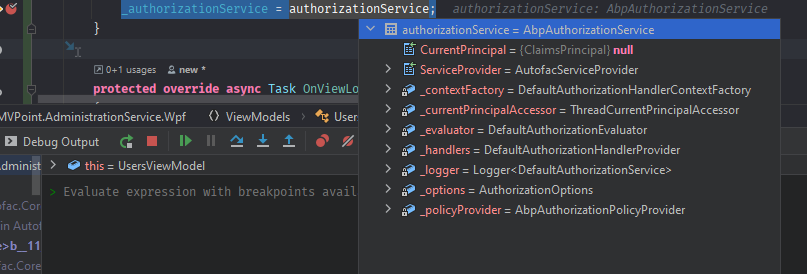
In our case we need to check the permission because we are hiding some controls/navigations if the current user is not granted from a specific policy.
Can you try to depends on the AbpAspNetCoreMvcClientModule?
Gave me exception:
Autofac.Core.DependencyResolutionException: An exception was thrown while activating CMVPoint.AdministrationService.Wpf.ViewModels.UsersViewModel -> Volo.Abp.Authorization.AbpAuthorizationService -> Microsoft.AspNetCore.Authorization.DefaultAuthorizationHandlerProvider -> λ:Microsoft.AspNetCore.Authorization.IAuthorizationHandler[] -> Volo.Abp.Authorization.PermissionRequirementHandler -> Volo.Abp.AspNetCore.Mvc.Client.RemotePermissionChecker -> Volo.Abp.AspNetCore.Mvc.Client.MvcCachedApplicationConfigurationClient.
---> Autofac.Core.DependencyResolutionException: None of the constructors found with 'Autofac.Core.Activators.Reflection.DefaultConstructorFinder' on type 'Volo.Abp.AspNetCore.Mvc.Client.MvcCachedApplicationConfigurationClient' can be invoked with the available services and parameters:
Cannot resolve parameter 'Microsoft.AspNetCore.Http.IHttpContextAccessor httpContextAccessor' of constructor 'Void .ctor(Volo.Abp.Caching.IDistributedCache`1[Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto], Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ClientProxies.AbpApplicationConfigurationClientProxy, Volo.Abp.Users.ICurrentUser, Microsoft.AspNetCore.Http.IHttpContextAccessor)'.
at Autofac.Core.Activators.Reflection.ReflectionActivator.GetAllBindings(ConstructorBinder[] availableConstructors, IComponentContext context, IEnumerable`1 parameters)
at Autofac.Core.Activators.Reflection.ReflectionActivator.ActivateInstance(IComponentContext context, IEnumerable`1 parameters)
at Autofac.Core.Activators.Reflection.ReflectionActivator.<ConfigurePipeline>b__11_0(ResolveRequestContext ctxt, Action`1 next)
at Autofac.Core.Resolving.Middleware.DelegateMiddleware.Execute(ResolveRequestContext context, Action`1 next)
at Autofac.Core.Resolving.Pipeline.ResolvePipelineBuilder.<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
at Autofac.Core.Resolving.Middleware.DisposalTrackingMiddleware.Execute(ResolveRequestContext context, Action`1 next)
at Autofac.Core.Resolving.Pipeline.ResolvePipelineBuilder.<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
at Autofac.Builder.RegistrationBuilder`3.<>c__DisplayClass41_0.<PropertiesAutowired>b__0(ResolveRequestContext ctxt, Action`1 next)
at Autofac.Core.Resolving.Middleware.DelegateMiddleware.Execute(ResolveRequestContext context, Action`1 next)
at Autofac.Core.Resolving.Pipeline.ResolvePipelineBuilder.<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
at Autofac.Core.Resolving.Middleware.ActivatorErrorHandlingMiddleware.Execute(ResolveRequestContext context, Action`1 next)
--- End of inner exception stack trace ---
It's dynamic since I'm using administration, identity http client modules that is using AddHttpClientProxies.
Hi,
It's been more than 24 hours. I also haven't resolve the issue yet. Is there anyone available to assist?
https://support.abp.io/QA/Questions/3192/Does-ABP-support-multi-factor-authentication-eg-Duo-Google-Authenticator-OTP-etc
Grateful if you can assist as commercial we need to implement support with the identify provider to use SMAL2 functionality for the likes of Cisco Duo & Azure etc if this not in scope for the old framework are we missing something? (Seeking your guidance) or is this something we can purchase as an enhancement with Abp for openiddict?
Hi,
It think it's not yet but trying to find way if we can use the SAML2P IdP of DUO SSO as external or other identity source. It's like users have to choose either they want to be authenticated from abp's default auth or authenticate externally to DUO SSO. Set openiddict as the main authentication, so I believe we need the openiddict to communicate with DUO saml assertions and trust the source for the client to access the api resource.
Hi,
Thank you, I haven't noticed that!