- ABP Framework version: v6.0&&.7.0
- UI type: Blazor
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes / no
- Exception message and stack trace:
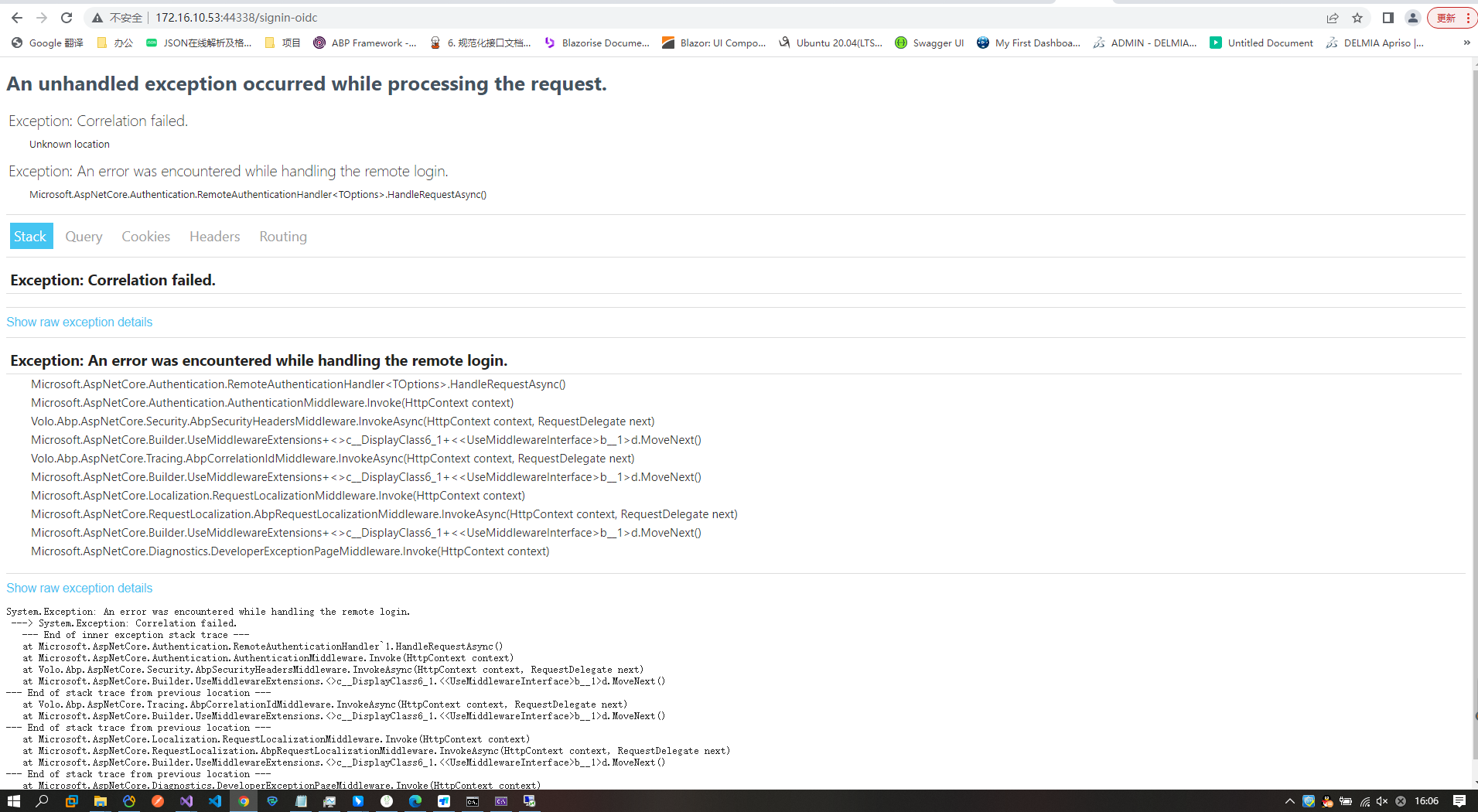
- Steps to reproduce the issue:"An error occurred in the single point single login project. The login jump cannot be directly adjusted to the authorization center, and the OpenId authorization error occurred An unhandled exception occurred while processing the request. Exception: Correlation failed. Unknown location
Exception: An error was encountered while handling the remote login. Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler<TOptions>.HandleRequestAsync()
Stack Query Cookies Headers Routing Exception: Correlation failed.
Show raw exception details Exception: An error was encountered while handling the remote login. Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler<TOptions>.HandleRequestAsync() Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context) Volo.Abp.AspNetCore.Security.AbpSecurityHeadersMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) Microsoft.AspNetCore.Builder.UseMiddlewareExtensions+<>c__DisplayClass6_1+<<UseMiddlewareInterface>b__1>d.MoveNext() Volo.Abp.AspNetCore.Tracing.AbpCorrelationIdMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) Microsoft.AspNetCore.Builder.UseMiddlewareExtensions+<>c__DisplayClass6_1+<<UseMiddlewareInterface>b__1>d.MoveNext() Microsoft.AspNetCore.Localization.RequestLocalizationMiddleware.Invoke(HttpContext context) Microsoft.AspNetCore.RequestLocalization.AbpRequestLocalizationMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) Microsoft.AspNetCore.Builder.UseMiddlewareExtensions+<>c__DisplayClass6_1+<<UseMiddlewareInterface>b__1>d.MoveNext() Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddleware.Invoke(HttpContext context)
Show raw exception details System.Exception: An error was encountered while handling the remote login. ---> System.Exception: Correlation failed. --- End of inner exception stack trace --- at Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler`1.HandleRequestAsync() at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context) at Volo.Abp.AspNetCore.Security.AbpSecurityHeadersMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<
Auth Log Success:
2023-04-17 16:02:48.867 +08:00 [INF] Request starting HTTP/1.1 GET http://172.16.10.210:44322/connect/authorize?client_id=ReportDemo&redirect_uri=http%3A%2F%2F172.16.10.53%3A44338%2Fsignin-oidc&response_type=code%20id_token&scope=openid%20profile%20roles%20email%20phone%20AccountService%20IdentityService%20AdministrationService%20SaasService&response_mode=form_post&nonce=638173153688190603.ZmY0MDU5MGEtMTI1MC00ZDQxLTg0MzctN2QzMDAwOWQwMzk1NmQ5Zjk3NjgtMzVlNy00ZDI1LWFiMWYtNGJkNDFhNTM5OGZm&state=CfDJ8CGkFfOcMF9BqQuVqGjsPmkIO_RJaHC3UPXRnuqggiA0xSjcl6AeQE5aDLZPmdewUxtyNgutcksCgl1Gvq-lgEkfahB5TAU2OUSGpUIJWHQ71PUq6rBHTEhw3NQps8D7RsZbAqFqEcZdK-k9ySY6fExuAPSw9ue3kMst_yuCZdOiyfdg0rTN--S6IIdXcI01jOII6bUeCVbDOD8Nuv-0ouDYsMHTcuk470TDpTLAfoqXOuWwcN5iB8u97tsXfJ0wxjIkC8I1DOScaoK75qf1IgSvjjx_Qw4iSSyucInqJKyDsy4-PmU7WTCZvR5_zJVmaX5VBVAG7Ma1HFLC6vpfhCWXGg_fwLvLFpy4c6Eir-2Xveb7O-lzbXKQLnYiDA2B2P1nuxdMzUIm89oSOyBXJJM&x-client-SKU=ID_NETSTANDARD2_0&x-client-ver=6.11.1.0 - -
2023-04-17 16:02:48.868 +08:00 [INF] The request address matched a server endpoint: "Authorization".
2023-04-17 16:02:48.868 +08:00 [INF] The authorization request was successfully extracted: {
"client_id": "ReportDemo",
"redirect_uri": "http://172.16.10.53:44338/signin-oidc",
"response_type": "code id_token",
"scope": "openid profile roles email phone AccountService IdentityService AdministrationService SaasService",
"response_mode": "form_post",
"nonce": "638173153688190603.ZmY0MDU5MGEtMTI1MC00ZDQxLTg0MzctN2QzMDAwOWQwMzk1NmQ5Zjk3NjgtMzVlNy00ZDI1LWFiMWYtNGJkNDFhNTM5OGZm",
"state": "CfDJ8CGkFfOcMF9BqQuVqGjsPmkIO_RJaHC3UPXRnuqggiA0xSjcl6AeQE5aDLZPmdewUxtyNgutcksCgl1Gvq-lgEkfahB5TAU2OUSGpUIJWHQ71PUq6rBHTEhw3NQps8D7RsZbAqFqEcZdK-k9ySY6fExuAPSw9ue3kMst_yuCZdOiyfdg0rTN--S6IIdXcI01jOII6bUeCVbDOD8Nuv-0ouDYsMHTcuk470TDpTLAfoqXOuWwcN5iB8u97tsXfJ0wxjIkC8I1DOScaoK75qf1IgSvjjx_Qw4iSSyucInqJKyDsy4-PmU7WTCZvR5_zJVmaX5VBVAG7Ma1HFLC6vpfhCWXGg_fwLvLFpy4c6Eir-2Xveb7O-lzbXKQLnYiDA2B2P1nuxdMzUIm89oSOyBXJJM",
"x-client-SKU": "ID_NETSTANDARD2_0",
"x-client-ver": "6.11.1.0"
}.
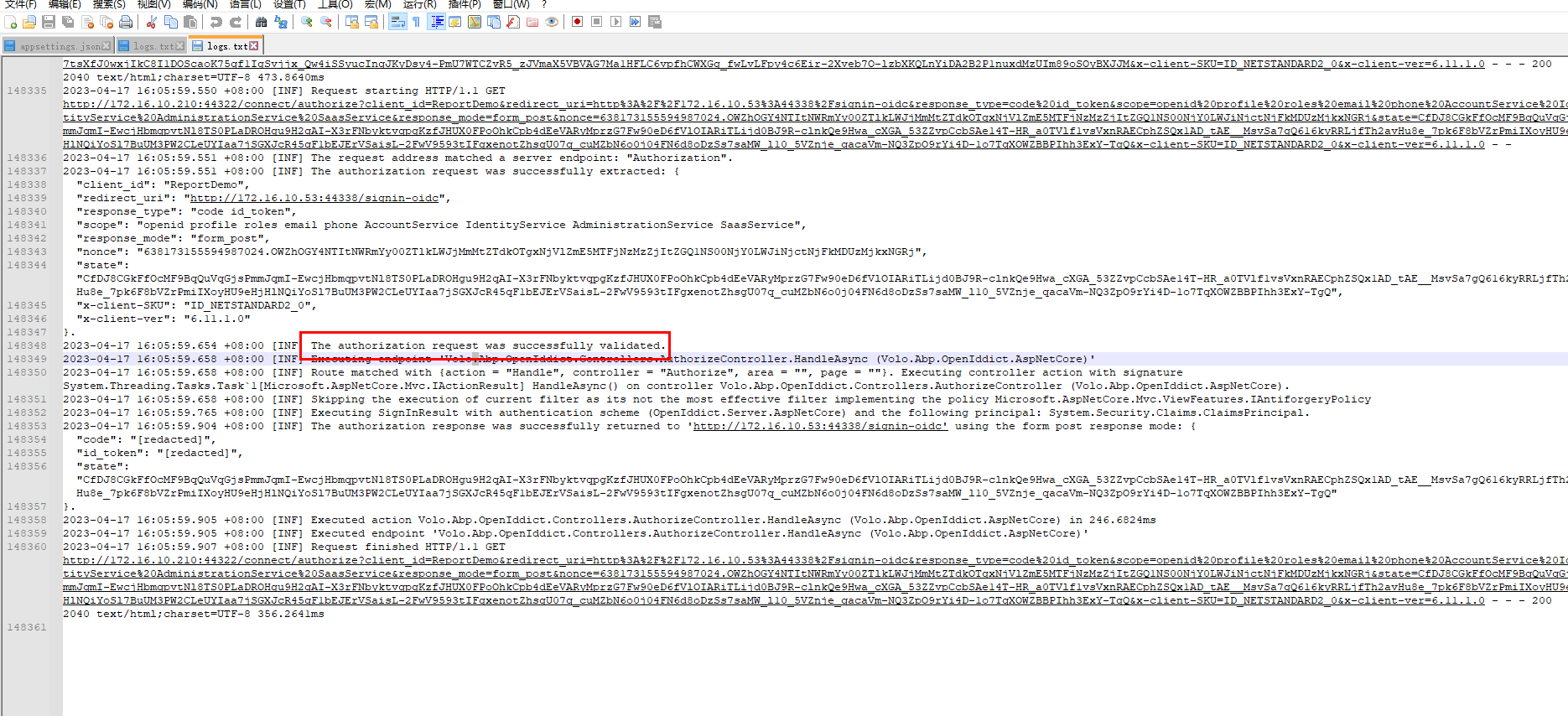
2023-04-17 16:02:48.993 +08:00 [INF] The authorization request was successfully validated.
2023-04-17 16:02:48.999 +08:00 [INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)'
2023-04-17 16:02:48.999 +08:00 [INF] Route matched with {action = "Handle", controller = "Authorize", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task1[Microsoft.AspNetCore.Mvc.IActionResult] HandleAsync() on controller Volo.Abp.OpenIddict.Controllers.AuthorizeController (Volo.Abp.OpenIddict.AspNetCore). 2023-04-17 16:02:48.999 +08:00 [INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy 2023-04-17 16:02:49.115 +08:00 [INF] Executing SignInResult with authentication scheme (OpenIddict.Server.AspNetCore) and the following principal: System.Security.Claims.ClaimsPrincipal. 2023-04-17 16:02:49.338 +08:00 [INF] The authorization response was successfully returned to 'http://172.16.10.53:44338/signin-oidc' using the form post response mode: { "code": "[redacted]", "id_token": "[redacted]", "state": "CfDJ8CGkFfOcMF9BqQuVqGjsPmkIO_RJaHC3UPXRnuqggiA0xSjcl6AeQE5aDLZPmdewUxtyNgutcksCgl1Gvq-lgEkfahB5TAU2OUSGpUIJWHQ71PUq6rBHTEhw3NQps8D7RsZbAqFqEcZdK-k9ySY6fExuAPSw9ue3kMst_yuCZdOiyfdg0rTN--S6IIdXcI01jOII6bUeCVbDOD8Nuv-0ouDYsMHTcuk470TDpTLAfoqXOuWwcN5iB8u97tsXfJ0wxjIkC8I1DOScaoK75qf1IgSvjjx_Qw4iSSyucInqJKyDsy4-PmU7WTCZvR5_zJVmaX5VBVAG7Ma1HFLC6vpfhCWXGg_fwLvLFpy4c6Eir-2Xveb7O-lzbXKQLnYiDA2B2P1nuxdMzUIm89oSOyBXJJM" }. 2023-04-17 16:02:49.339 +08:00 [INF] Executed action Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore) in 339.6067ms 2023-04-17 16:02:49.339 +08:00 [INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' 2023-04-17 16:02:49.341 +08:00 [INF] Request finished HTTP/1.1 GET http://172.16.10.210:44322/connect/authorize?client_id=ReportDemo&redirect_uri=http%3A%2F%2F172.16.10.53%3A44338%2Fsignin-oidc&response_type=code%20id_token&scope=openid%20profile%20roles%20email%20phone%20AccountService%20IdentityService%20AdministrationService%20SaasService&response_mode=form_post&nonce=638173153688190603.ZmY0MDU5MGEtMTI1MC00ZDQxLTg0MzctN2QzMDAwOWQwMzk1NmQ5Zjk3NjgtMzVlNy00ZDI1LWFiMWYtNGJkNDFhNTM5OGZm&state=CfDJ8CGkFfOcMF9BqQuVqGjsPmkIO_RJaHC3UPXRnuqggiA0xSjcl6AeQE5aDLZPmdewUxtyNgutcksCgl1Gvq-lgEkfahB5TAU2OUSGpUIJWHQ71PUq6rBHTEhw3NQps8D7RsZbAqFqEcZdK-k9ySY6fExuAPSw9ue3kMst_yuCZdOiyfdg0rTN--S6IIdXcI01jOII6bUeCVbDOD8Nuv-0ouDYsMHTcuk470TDpTLAfoqXOuWwcN5iB8u97tsXfJ0wxjIkC8I1DOScaoK75qf1IgSvjjx_Qw4iSSyucInqJKyDsy4-PmU7WTCZvR5_zJVmaX5VBVAG7Ma1HFLC6vpfhCWXGg_fwLvLFpy4c6Eir-2Xveb7O-lzbXKQLnYiDA2B2P1nuxdMzUIm89oSOyBXJJM&x-client-SKU=ID_NETSTANDARD2_0&x-client-ver=6.11.1.0 - - - 200 2040 text/html;charset=UTF-8 473.8640ms 2023-04-17 16:05:59.550 +08:00 [INF] Request starting HTTP/1.1 GET http://172.16.10.210:44322/connect/authorize?client_id=ReportDemo&redirect_uri=http%3A%2F%2F172.16.10.53%3A44338%2Fsignin-oidc&response_type=code%20id_token&scope=openid%20profile%20roles%20email%20phone%20AccountService%20IdentityService%20AdministrationService%20SaasService&response_mode=form_post&nonce=638173155594987024.OWZhOGY4NTItNWRmYy00ZTlkLWJjMmMtZTdkOTgxNjVlZmE5MTFjNzMzZjItZGQ1NS00NjY0LWJiNjctNjFkMDUzMjkxNGRj&state=CfDJ8CGkFfOcMF9BqQuVqGjsPmmJqmI-EwcjHbmqpvtNl8TS0PLaDROHgu9H2qAI-X3rFNbyktvqpgKzfJHUX0FPoOhkCpb4dEeVARyMprzG7Fw90eD6fVlOIARiTLijd0BJ9R-clnkQe9Hwa_cXGA_53ZZvpCcbSAe14T-HR_a0TVlf1vsVxnRAECphZSQx1AD_tAE__MsvSa7gQ616kyRRLjfTh2avHu8e_7pk6F8bVZrPmiIXoyHU9eHjHlNQiYoSl7BuUM3PW2CLeUYIaa7jSGXJcR45qF1bEJErVSaisL-2FwV9593tIFgxenotZhsgU07q_cuMZbN6o0j04FN6d8oDzSs7saMW_l10_5VZnje_qacaVm-NQ3ZpO9rYi4D-1o7TqXOWZBBPIhh3ExY-TgQ&x-client-SKU=ID_NETSTANDARD2_0&x-client-ver=6.11.1.0 - - 2023-04-17 16:05:59.551 +08:00 [INF] The request address matched a server endpoint: "Authorization". 2023-04-17 16:05:59.551 +08:00 [INF] The authorization request was successfully extracted: { "client_id": "ReportDemo", "redirect_uri": "http://172.16.10.53:44338/signin-oidc", "response_type": "code id_token", "scope": "openid profile roles email phone AccountService IdentityService AdministrationService SaasService", "response_mode": "form_post", "nonce": "638173155594987024.OWZhOGY4NTItNWRmYy00ZTlkLWJjMmMtZTdkOTgxNjVlZmE5MTFjNzMzZjItZGQ1NS00NjY0LWJiNjctNjFkMDUzMjkxNGRj", "state": "CfDJ8CGkFfOcMF9BqQuVqGjsPmmJqmI-EwcjHbmqpvtNl8TS0PLaDROHgu9H2qAI-X3rFNbyktvqpgKzfJHUX0FPoOhkCpb4dEeVARyMprzG7Fw90eD6fVlOIARiTLijd0BJ9R-clnkQe9Hwa_cXGA_53ZZvpCcbSAe14T-HR_a0TVlf1vsVxnRAECphZSQx1AD_tAE__MsvSa7gQ616kyRRLjfTh2avHu8e_7pk6F8bVZrPmiIXoyHU9eHjHlNQiYoSl7BuUM3PW2CLeUYIaa7jSGXJcR45qF1bEJErVSaisL-2FwV9593tIFgxenotZhsgU07q_cuMZbN6o0j04FN6d8oDzSs7saMW_l10_5VZnje_qacaVm-NQ3ZpO9rYi4D-1o7TqXOWZBBPIhh3ExY-TgQ", "x-client-SKU": "ID_NETSTANDARD2_0", "x-client-ver": "6.11.1.0" }. 2023-04-17 16:05:59.654 +08:00 [INF] The authorization request was successfully validated. 2023-04-17 16:05:59.658 +08:00 [INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' 2023-04-17 16:05:59.658 +08:00 [INF] Route matched with {action = "Handle", controller = "Authorize", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task1[Microsoft.AspNetCore.Mvc.IActionResult] HandleAsync() on controller Volo.Abp.OpenIddict.Controllers.AuthorizeController (Volo.Abp.OpenIddict.AspNetCore).
2023-04-17 16:05:59.658 +08:00 [INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy
2023-04-17 16:05:59.765 +08:00 [INF] Executing SignInResult with authentication scheme (OpenIddict.Server.AspNetCore) and the following principal: System.Security.Claims.ClaimsPrincipal.
2023-04-17 16:05:59.904 +08:00 [INF] The authorization response was successfully returned to 'http://172.16.10.53:44338/signin-oidc' using the form post response mode: {
"code": "[redacted]",
"id_token": "[redacted]",
"state": "CfDJ8CGkFfOcMF9BqQuVqGjsPmmJqmI-EwcjHbmqpvtNl8TS0PLaDROHgu9H2qAI-X3rFNbyktvqpgKzfJHUX0FPoOhkCpb4dEeVARyMprzG7Fw90eD6fVlOIARiTLijd0BJ9R-clnkQe9Hwa_cXGA_53ZZvpCcbSAe14T-HR_a0TVlf1vsVxnRAECphZSQx1AD_tAE__MsvSa7gQ616kyRRLjfTh2avHu8e_7pk6F8bVZrPmiIXoyHU9eHjHlNQiYoSl7BuUM3PW2CLeUYIaa7jSGXJcR45qF1bEJErVSaisL-2FwV9593tIFgxenotZhsgU07q_cuMZbN6o0j04FN6d8oDzSs7saMW_l10_5VZnje_qacaVm-NQ3ZpO9rYi4D-1o7TqXOWZBBPIhh3ExY-TgQ"
}.
2023-04-17 16:05:59.905 +08:00 [INF] Executed action Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore) in 246.6824ms
2023-04-17 16:05:59.905 +08:00 [INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)'
2023-04-17 16:05:59.907 +08:00 [INF] Request finished HTTP/1.1 GET http://172.16.10.210:44322/connect/authorize?client_id=ReportDemo&redirect_uri=http%3A%2F%2F172.16.10.53%3A44338%2Fsignin-oidc&response_type=code%20id_token&scope=openid%20profile%20roles%20email%20phone%20AccountService%20IdentityService%20AdministrationService%20SaasService&response_mode=form_post&nonce=638173155594987024.OWZhOGY4NTItNWRmYy00ZTlkLWJjMmMtZTdkOTgxNjVlZmE5MTFjNzMzZjItZGQ1NS00NjY0LWJiNjctNjFkMDUzMjkxNGRj&state=CfDJ8CGkFfOcMF9BqQuVqGjsPmmJqmI-EwcjHbmqpvtNl8TS0PLaDROHgu9H2qAI-X3rFNbyktvqpgKzfJHUX0FPoOhkCpb4dEeVARyMprzG7Fw90eD6fVlOIARiTLijd0BJ9R-clnkQe9Hwa_cXGA_53ZZvpCcbSAe14T-HR_a0TVlf1vsVxnRAECphZSQx1AD_tAE__MsvSa7gQ616kyRRLjfTh2avHu8e_7pk6F8bVZrPmiIXoyHU9eHjHlNQiYoSl7BuUM3PW2CLeUYIaa7jSGXJcR45qF1bEJErVSaisL-2FwV9593tIFgxenotZhsgU07q_cuMZbN6o0j04FN6d8oDzSs7saMW_l10_5VZnje_qacaVm-NQ3ZpO9rYi4D-1o7TqXOWZBBPIhh3ExY-TgQ&x-client-SKU=ID_NETSTANDARD2_0&x-client-ver=6.11.1.0 - - - 200 2040 text/html;charset=UTF-8 356.2641ms
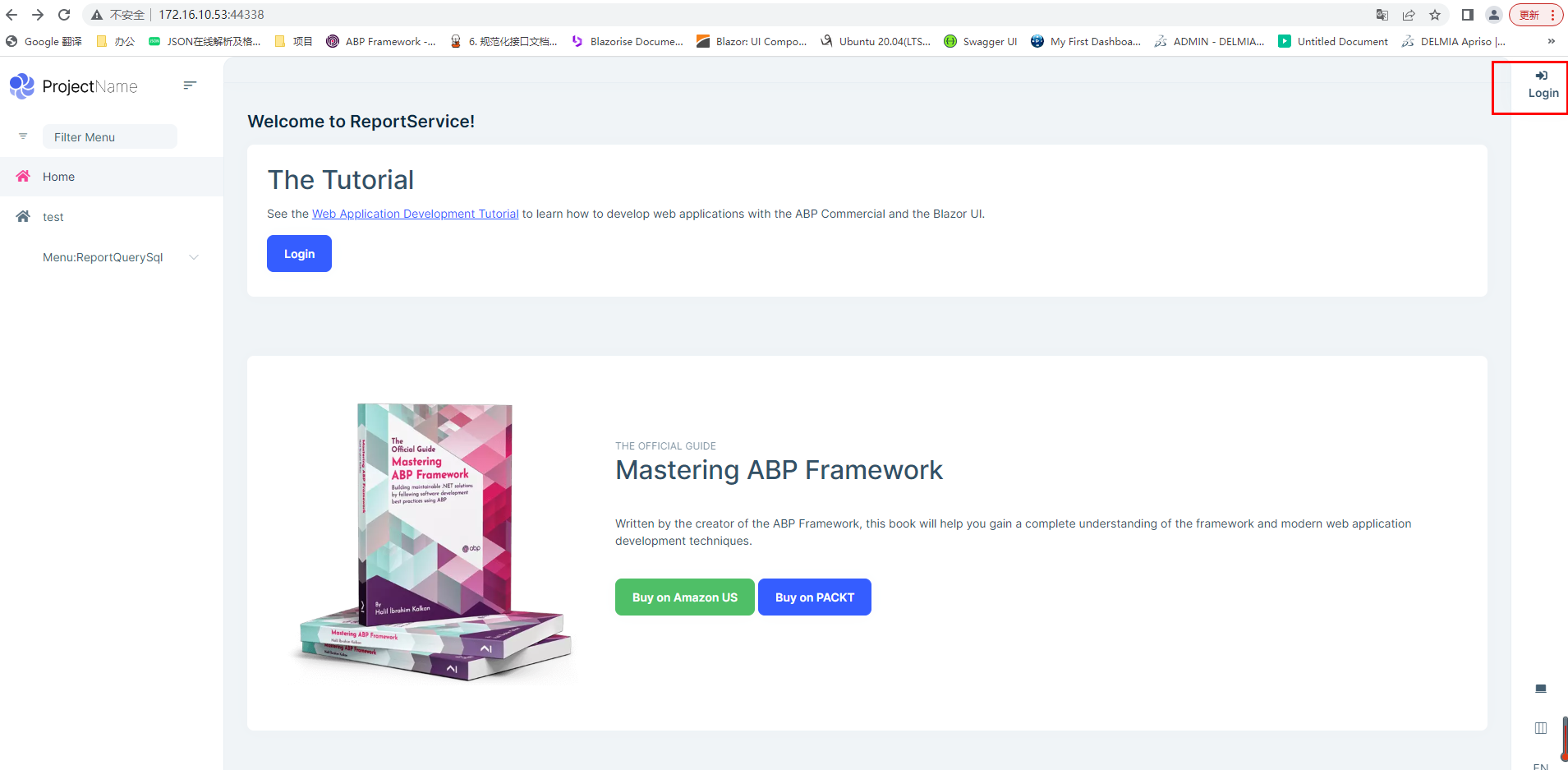
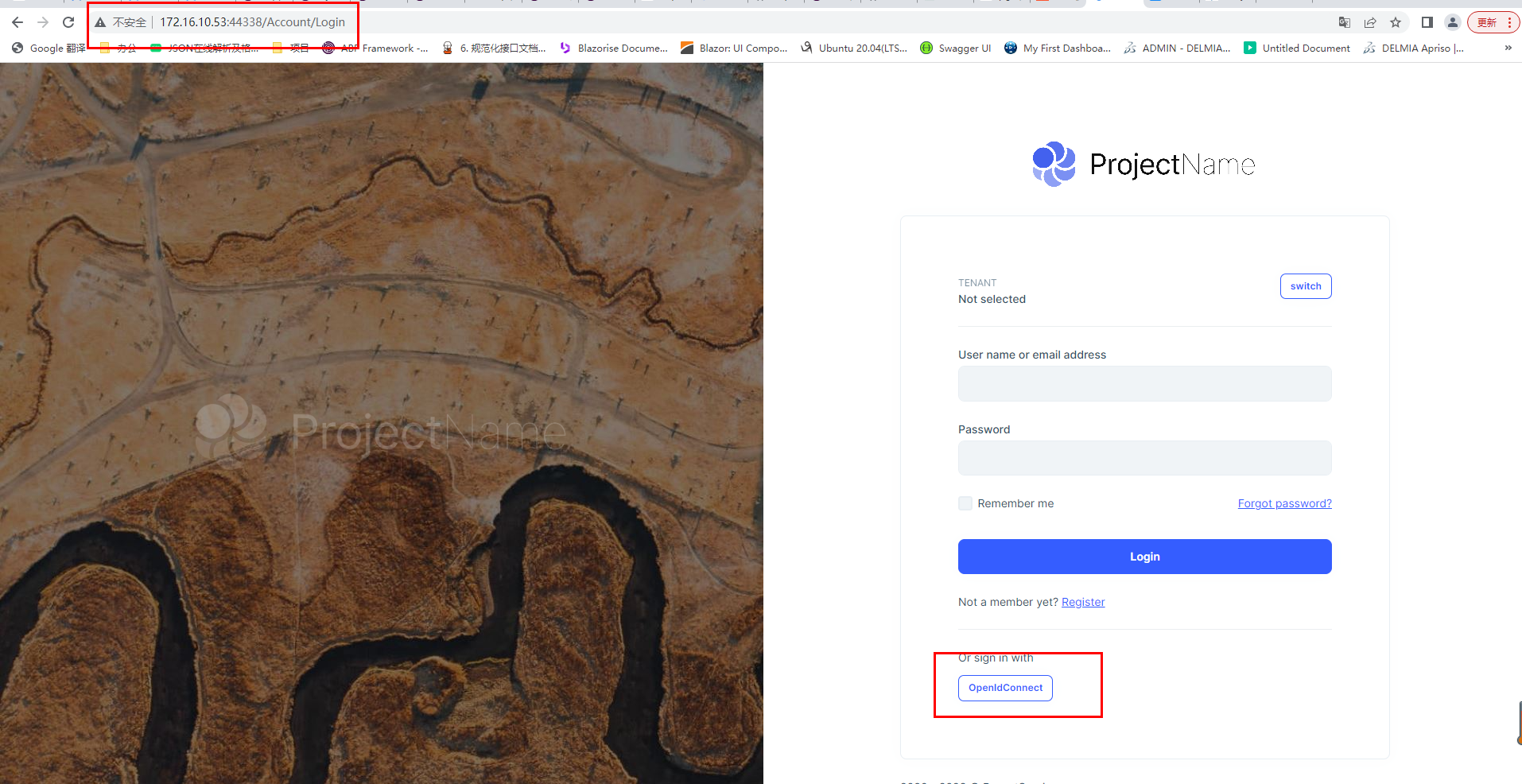
The operation steps are shown in the following figure:
13 Answer(s)
-
0
Hi,
Can you check those?
https://www.cnblogs.com/stulzq/p/13954245.html https://stackoverflow.com/questions/50262561/correlation-failed-in-net-core-asp-net-identity-openid-connect
-
0
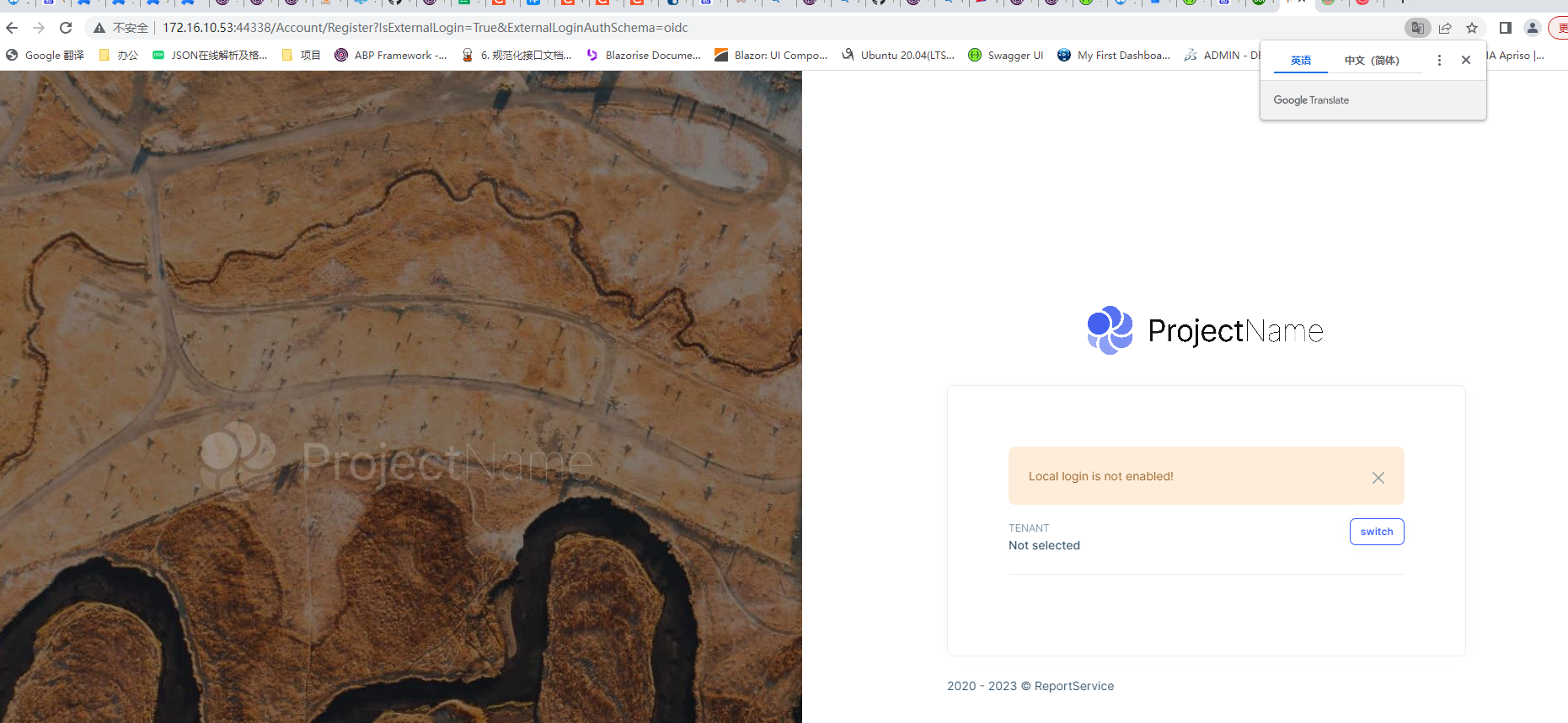
Hi Why is external authorization login? The page will be called back to the registration page, not the login page of the authorization center
Modified local configuration appsettings.json
"Settings": { "Abp.Account.IsSelfRegistrationEnabled": false, "Abp.Account.EnableLocalLogin": false }
Click the login button to adjust to the authorization center page
http://172.16.10.210:44322/connect/authorize?client_id=ReportDemo&redirect_uri=http://172.16.10.53:44338/signin-oidc&response_type=code id_token&scope=openid profile roles email phone AccountService IdentityService AdministrationService SaasService&response_mode=form_post&nonce=638175511421012693.MjllNTM0MjItM2I4OC00YTQxLTkxMjYtZjA3OGJkMTZiYzVkMzMzMTJjZDAtZWI5YS00NWU1LTgwYzEtNDUyYzEzMzJjNDk5&state=CfDJ8CGkFfOcMF9BqQuVqGjsPmkUiAQ-qr26COAb3ZpYXfIqrhRENdHI3s0mNNF3oYFM42Fx-QSyj0E0E-3ksNYFFMna34WePuihsjAsn-CXAj4iuwH9sMHf6_QWZXtN5WRX8FYwUF3KYavo0ScSRcg9Za0MafqLM53zJbQndSBzbJd-MMNyIfGq1aRiy3mOPQ6XtdDeE1gvz1FFzlVO7k-sl0J2uI-hBaLBYE26eEy9KwjI6bFXjsM_Y7WhbcdAZRYCPMQ27hi1HBafp9EAZLiPFpiLnrUFxGe4lH2VKUTABD0ipzw_rdYEYlmNL61nYIUH_uCFaxj3aIZGQzoWIqCGPf9K6arD7oekcZaBPEqZQE8rFyMOo-Oe486hWjQx83cylEwldG-cE25zdx47SBct5Mg&x-client-SKU=ID_NETSTANDARD2_0&x-client-ver=6.11.1.0
And immediately adjust tohttp://172.16.10.53:44338/Account/Register?IsExternalLogin=True&ExternalLoginAuthSchema=oidc
-
0
Hi,
Because there is no local account here, you can try this:
.AddOpenIdConnect(Azure...,options => { var tokenValidated = options.Events.OnTokenValidated; options.Events.OnTokenValidated = validatedContext => { tokenValidated.Invoke(validatedContext); validatedContext.Principal.AddClaim(AbpClaimTypes.Email, validatedContext.Principal.FindFirstValue(ClaimTypes.Email)); return Task.CompletedTask; }; }) -
0
Hi, Following your instructions, the same error occurred. The page that was redirected back is/Account/Register http://172.16.10.53:44338/Account/Register?IsExternalLogin=True&ExternalLoginAuthSchema=oidc
the configuration as follow:
.AddAbpOpenIdConnect("oidc", options =>{ options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]); ; options.ResponseType = OpenIdConnectResponseType.CodeIdToken; options.ClientId = configuration["AuthServer:ClientId"]; options.ClientSecret = configuration["AuthServer:ClientSecret"]; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.Scope.Add("roles"); options.Scope.Add("email"); options.Scope.Add("phone"); options.Scope.Add("AccountService"); options.Scope.Add("IdentityService"); options.Scope.Add("AdministrationService"); options.Scope.Add("SaasService"); //options.Scope.Add("ProductService"); //options.Scope.Add("ElsaService"); var tokenValidated = options.Events.OnTokenValidated; options.Events.OnTokenValidated = validatedContext => { tokenValidated.Invoke(validatedContext); validatedContext.Principal.AddClaim(AbpClaimTypes.Email, validatedContext.Principal.FindFirstValue(ClaimTypes.Email)); return Task.CompletedTask; }; });.AddOpenIdConnect(Azure...,options => { var tokenValidated = options.Events.OnTokenValidated; options.Events.OnTokenValidated = validatedContext => { tokenValidated.Invoke(validatedContext); validatedContext.Principal.AddClaim(AbpClaimTypes.Email, validatedContext.Principal.FindFirstValue(ClaimTypes.Email)); return Task.CompletedTask; }; }) -
0
Hi,
I can't reproduce the problem
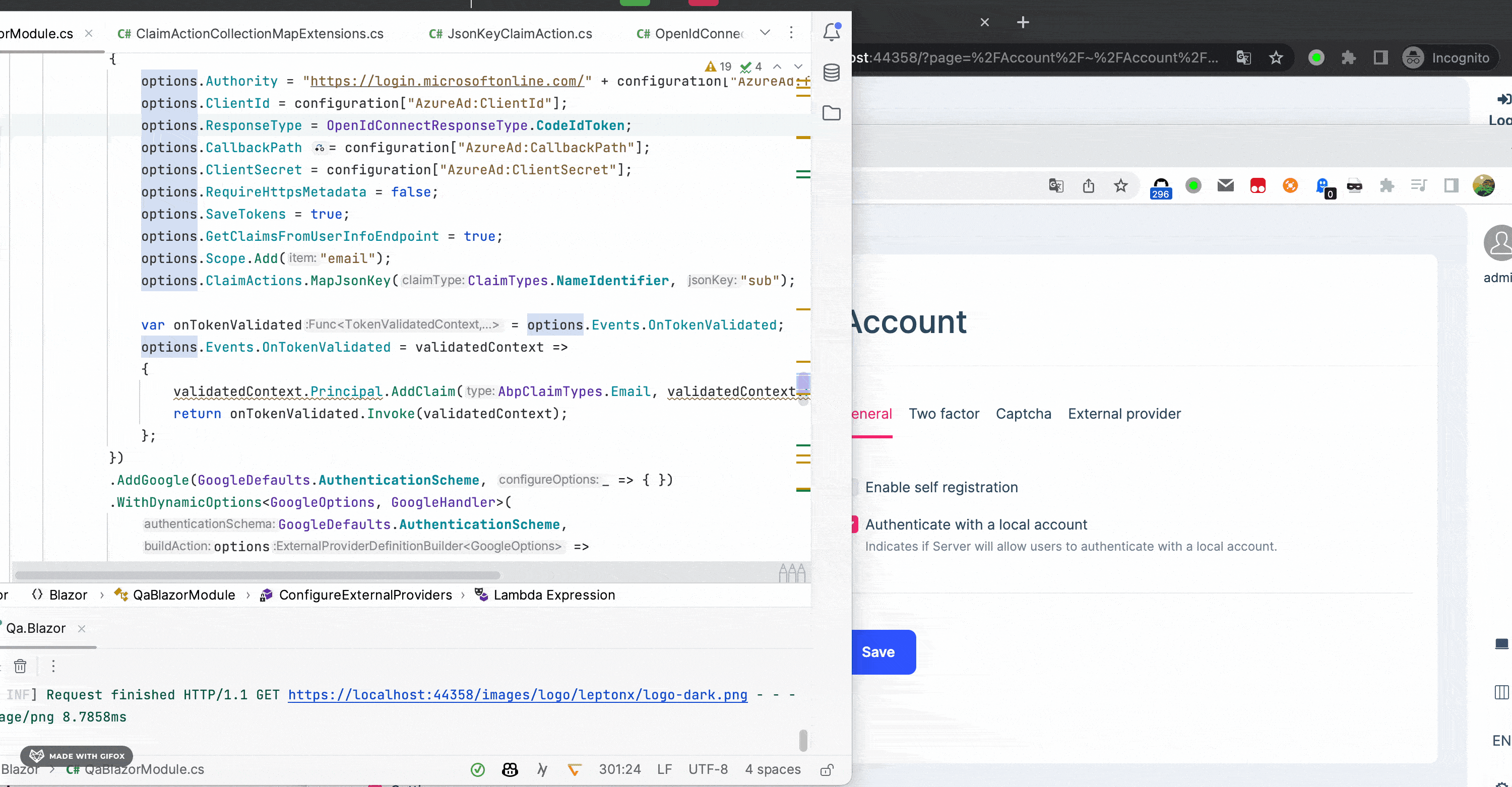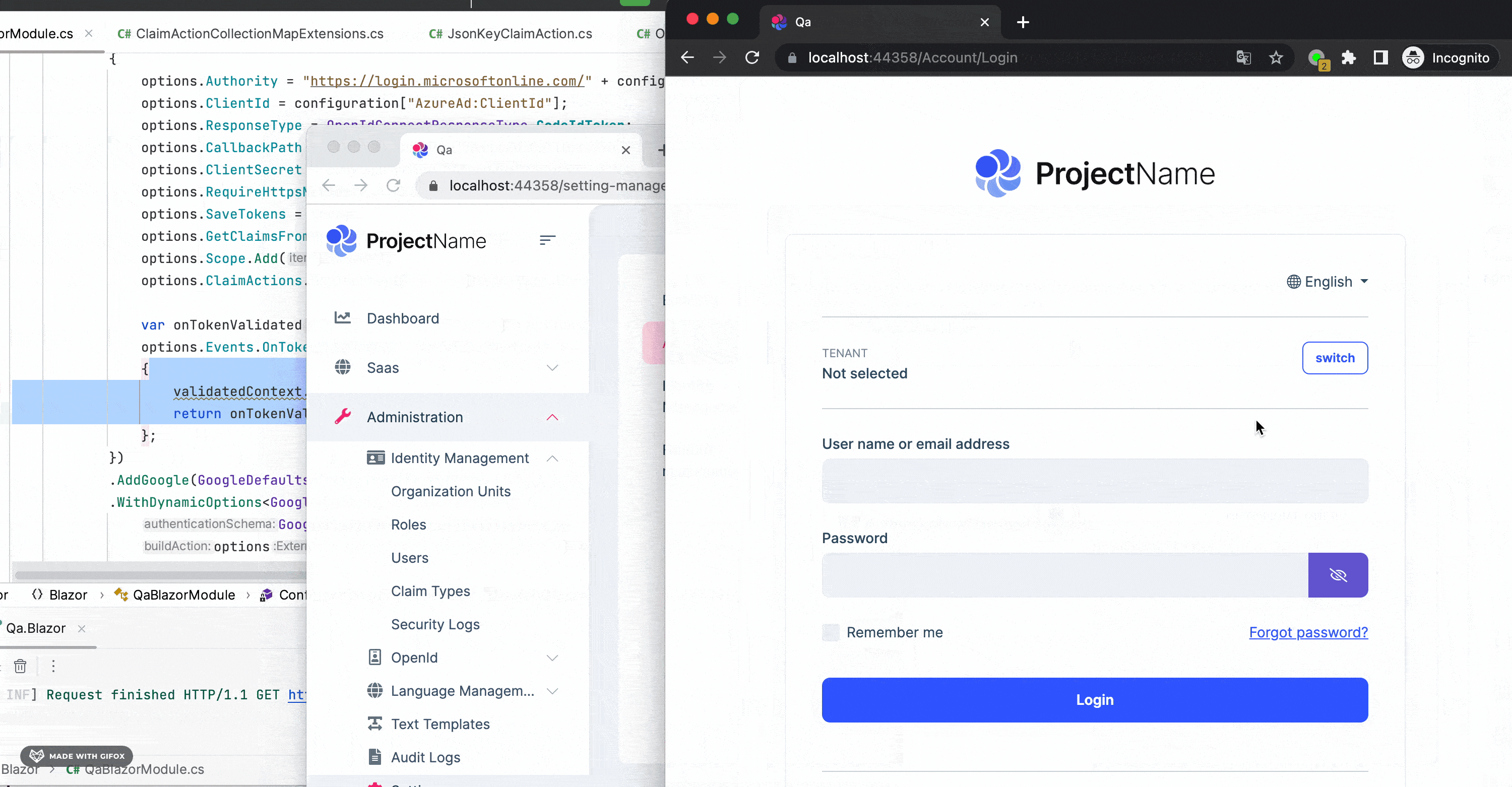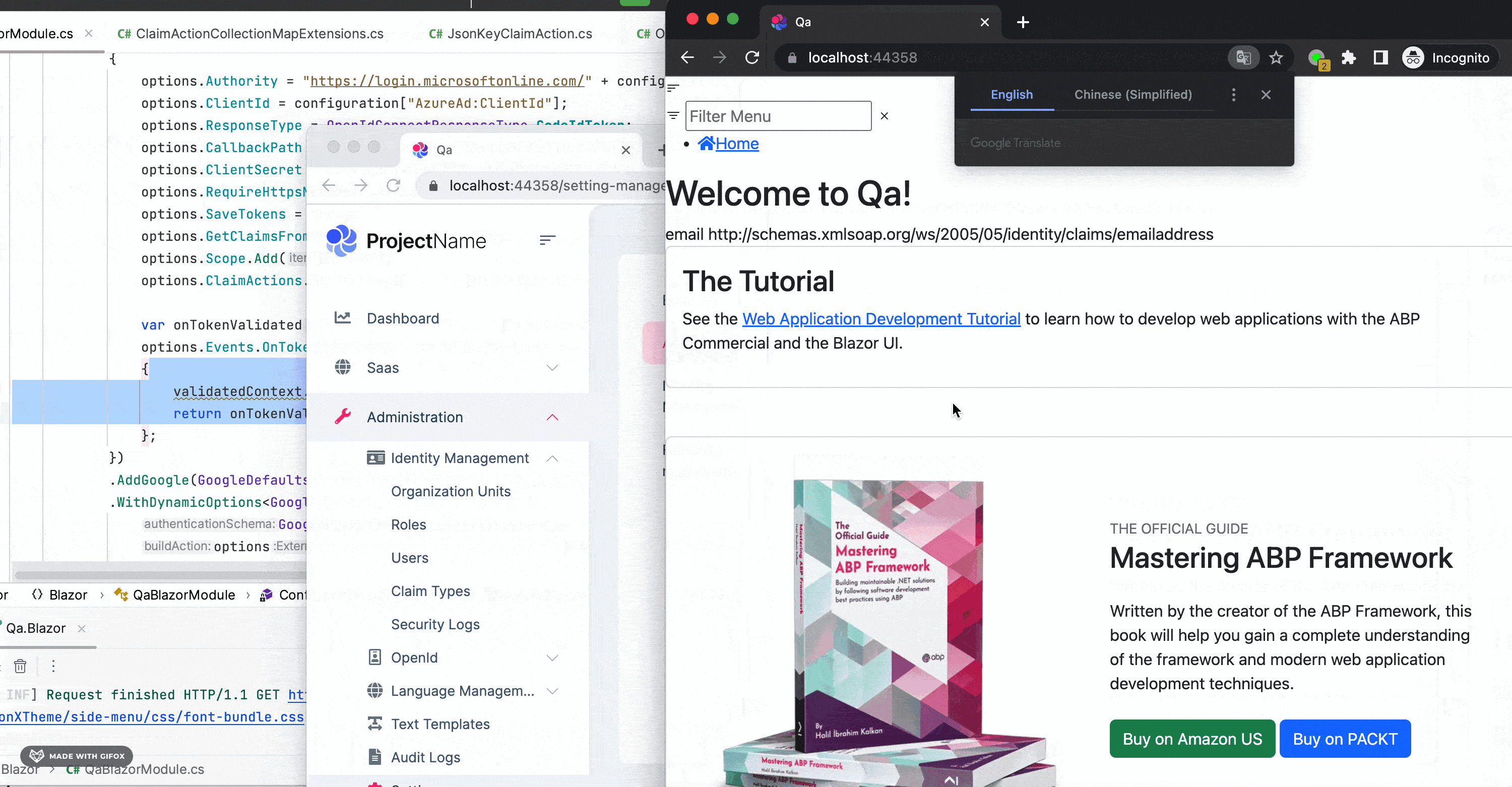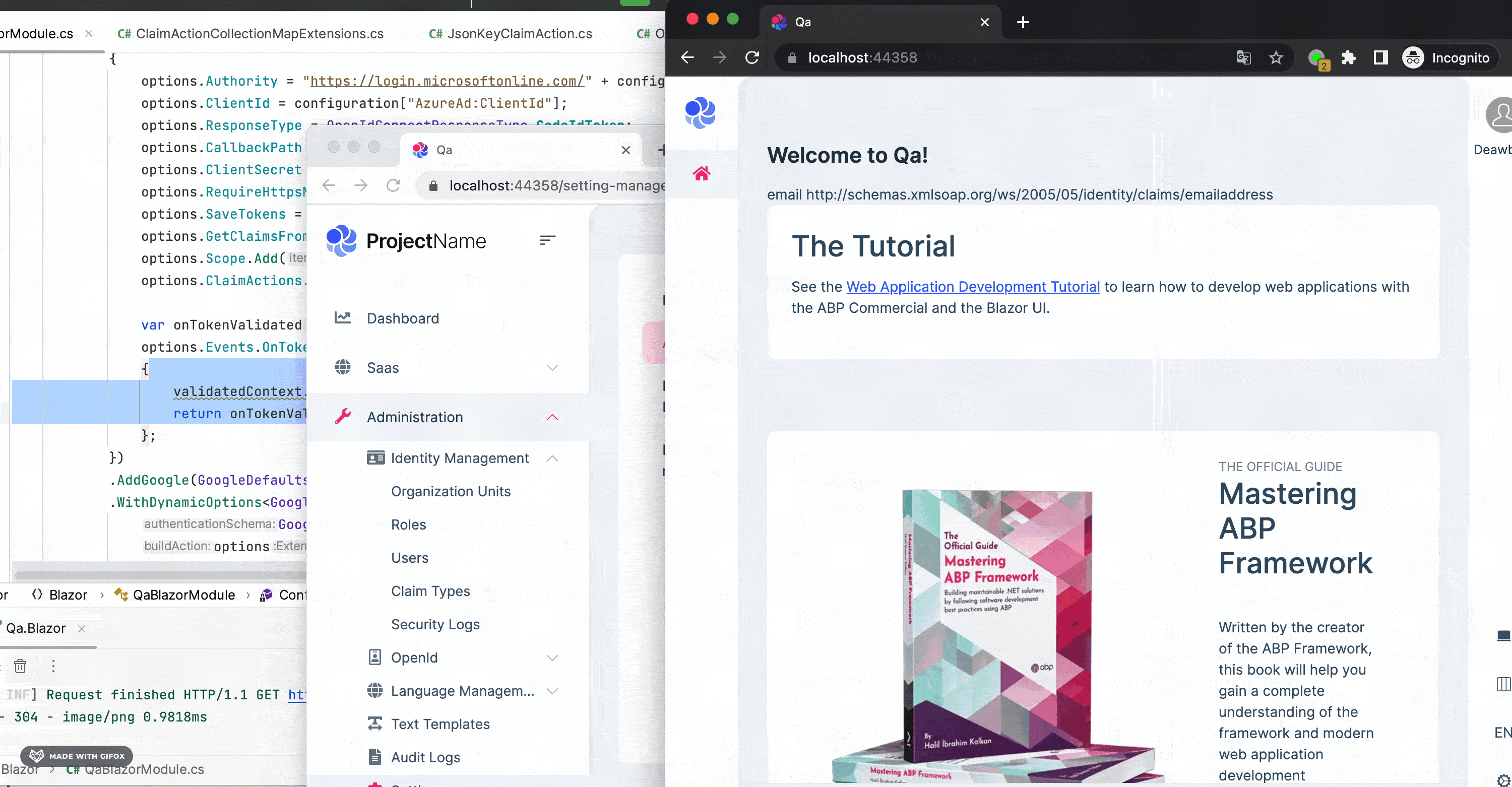
.AddOpenIdConnect("AzureOpenId", "Azure AD OpenId", options => { options.Authority = "https://login.microsoftonline.com/" + configuration["AzureAd:TenantId"] + "/v2.0/"; options.ClientId = configuration["AzureAd:ClientId"]; options.ResponseType = OpenIdConnectResponseType.CodeIdToken; options.CallbackPath = configuration["AzureAd:CallbackPath"]; options.ClientSecret = configuration["AzureAd:ClientSecret"]; options.RequireHttpsMetadata = false; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.Scope.Add("email"); options.ClaimActions.MapJsonKey(ClaimTypes.NameIdentifier, "sub"); var onTokenValidated = options.Events.OnTokenValidated; options.Events.OnTokenValidated = validatedContext => { validatedContext.Principal.AddClaim(AbpClaimTypes.Email, validatedContext.Principal.FindFirstValue(ClaimTypes.Email)); return onTokenValidated.Invoke(validatedContext); }; }) -
0
hi Can you send me your demo? I'll compare it
-
0
ok. What's your email?
-
0
hi
My email: 276389409@qq.com, thank you -
0
Hi,
I shared the project with you, please check it
-
0
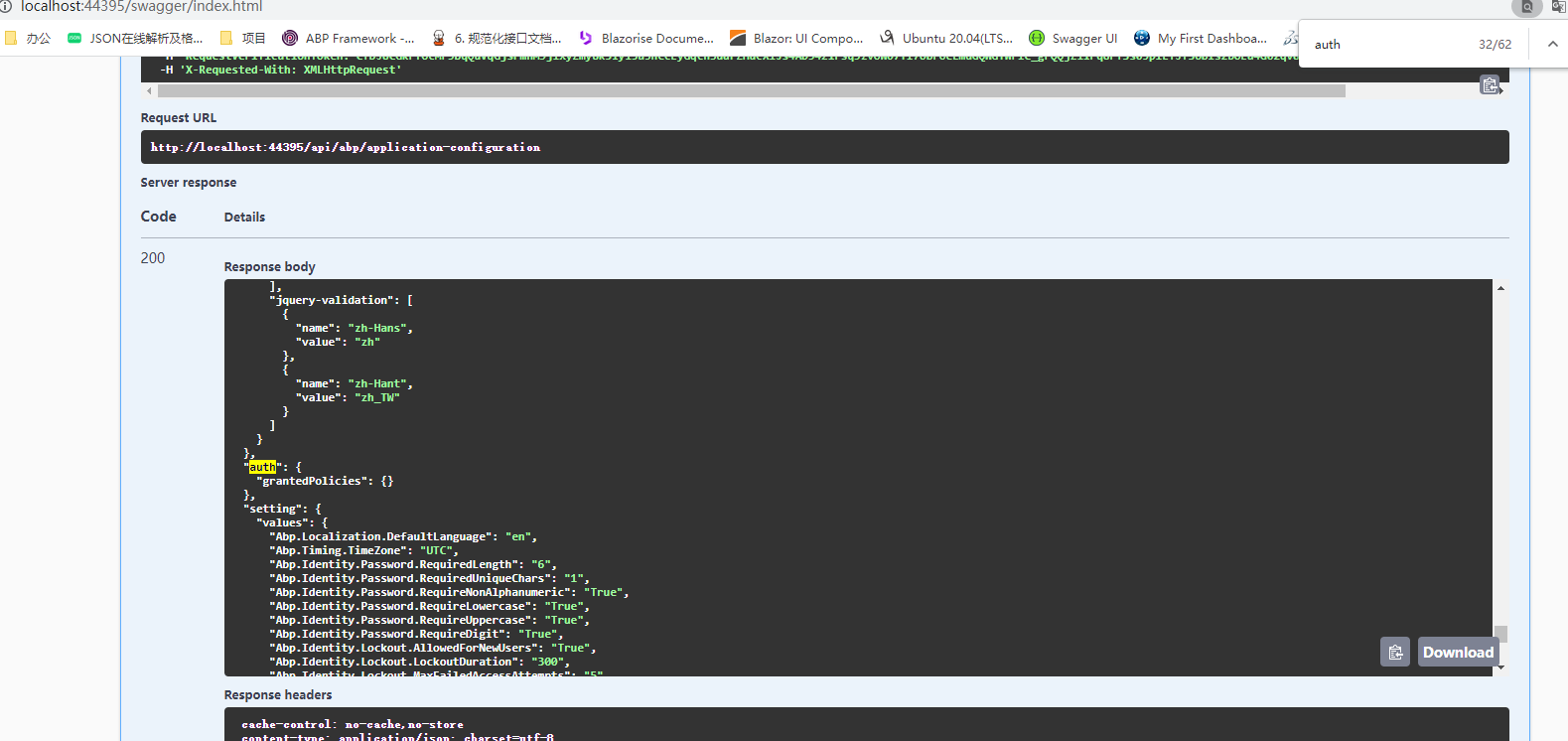
hi Why is the permission policy empty after authorized login?
"auth": { "grantedPolicies": {} }, "setting": { "values": { "Abp.Localization.DefaultLanguage": "en", "Abp.Timing.TimeZone": "UTC", "Abp.Identity.Password.RequiredLength": "6", "Abp.Identity.Password.RequiredUniqueChars": "1", "Abp.Identity.Password.RequireNonAlphanumeric": "True", "Abp.Identity.Password.RequireLowercase": "True", "Abp.Identity.Password.RequireUppercase": "True", "Abp.Identity.Password.RequireDigit": "True", "Abp.Identity.Lockout.AllowedForNewUsers": "True", "Abp.Identity.Lockout.LockoutDuration": "300", "Abp.Identity.Lockout.MaxFailedAccessAttempts": "5", "Abp.Identity.SignIn.RequireConfirmedEmail": "False", "Abp.Identity.SignIn.EnablePhoneNumberConfirmation": "True", "Abp.Identity.SignIn.RequireConfirmedPhoneNumber": "False", "Abp.Identity.User.IsUserNameUpdateEnabled": "True", "Abp.Identity.User.IsEmailUpdateEnabled": "True", "Abp.Identity.OrganizationUnit.MaxUserMembershipCount": "2147483647", "Abp.Identity.TwoFactor.Behaviour": "Optional", "Abp.Identity.TwoFactor.UsersCanChange": "True", "Abp.Account.EnableLdapLogin": "false", "Abp.Identity.EnableOAuthLogin": "false", "Abp.Identity.OAuthLogin.Authority": null, "Abp.Identity.OAuthLogin.ClientId": null, "Abp.Identity.OAuthLogin.ClientSecret": null, "Abp.Identity.OAuthLogin.Scope": null, "Abp.Identity.OAuthLogin.RequireHttpsMetadata": "false", "Abp.Identity.OAuthLogin.ValidateEndpoints": "false", "Abp.Identity.OAuthLogin.ValidateIssuerName": "false", "Abp.Account.IsSelfRegistrationEnabled": "False", "Abp.Account.EnableLocalLogin": "False", "Abp.Account.TwoFactorLogin.IsRememberBrowserEnabled": "true", "Abp.Account.Captcha.UseCaptchaOnLogin": "false", "Abp.Account.Captcha.UseCaptchaOnRegistration": "false", "Abp.Account.Captcha.VerifyBaseUrl": "https://www.google.com/", "Abp.Account.Captcha.SiteKey": null, "Abp.Account.Captcha.Version": "3", "Abp.Account.Captcha.Score": "0.5", "Abp.Account.ProfilePictureSource": "False", "Volo.Abp.LeptonTheme.Layout.Boxed": "False", "Volo.Abp.LeptonTheme.Layout.MenuPlacement": "Left", "Volo.Abp.LeptonTheme.Layout.MenuStatus": "AlwaysOpened", "Volo.Abp.LeptonTheme.Style": "Style6", "Volo.Abp.LeptonTheme.Style.PublicLayout": "Style1" } }, "currentUser": { "isAuthenticated": true, "id": "0d08f47e-23b7-b89c-45bd-3a0ab4f41e11", "tenantId": null, "impersonatorUserId": null, "impersonatorTenantId": null, "impersonatorUserName": null, "impersonatorTenantName": null, "userName": "test@qq.com", "name": "test", "surName": "test", "email": "test@qq.com", "emailVerified": false, "phoneNumber": null, "phoneNumberVerified": false, "roles": [] }, -
0
Hi,
I think there is a new account without any roles, you can add some roles to the account
-
0
Hi,
After authorized login, a new user was indeed created again
Now the subsystem wants to retrieve user permissions, roles, and other information directly from the authorization center
Rebuilding seems to violate single sign on
Is there any way
-
0
Hi,
You can check this: https://support.abp.io/QA/Questions/2289/Problemin-assign-a-new-role-to-the-user#answer-3a84594d-c1aa-e342-7885-3a010d738f2e
It immediately refreshes the current user's roles