- ABP Framework version: v7.4.2
- UI Type: MVC(SQL)
Hi,
After we upgraded from IdentityServer to OpenIdDict there were some issues
We have an Admin application (which is working fine) and Clinic application which has an issue while redirecting to the application dashboard after signing in using OpenId
Please advise ASAP.
46 Answer(s)
-
0
Please share the related logs of your
- Application
- AuthServer
-
0
kindly check.
-
0
hi
The authserver says:
The specified access token is bound to an account that no longer exists.Does your account belong to a tenant?
Can you share the code of
AuthServermodule? -
0
yes, the account is related to a tenant.
-
0
hi
Please adjust the order of your middleware based on https://github.com/abpframework/abp/blob/dev/templates/module/aspnet-core/host/MyCompanyName.MyProjectName.AuthServer/MyProjectNameAuthServerModule.cs#L211-L233
-
0
-
0
hi
Please adjust the order of your middleware based on https://github.com/abpframework/abp/blob/dev/templates/module/aspnet-core/host/MyCompanyName.MyProjectName.AuthServer/MyProjectNameAuthServerModule.cs#L211-L233
is this correct?
public override void OnApplicationInitialization(ApplicationInitializationContext context) { var app = context.GetApplicationBuilder(); var env = context.GetEnvironment(); if (env.IsDevelopment()) { app.UseDeveloperExceptionPage(); } if (!env.IsDevelopment()) { app.UseErrorPage(); } app.UseHttpsRedirection(); app.UseCorrelationId(); app.UseStaticFiles(); app.UseRouting(); app.UseCors(); app.UseAuthentication(); app.UseAbpOpenIddictValidation(); if (MultiTenancyConsts.IsEnabled) { app.UseMultiTenancy(); } //app.UseJwtTokenMiddleware(); app.UseAbpRequestLocalization(options => { options.RequestCultureProviders.RemoveAll(x => x.GetType() == typeof(AcceptLanguageHeaderRequestCultureProvider)); options.SetDefaultCulture("en-US"); }); app.UseAuditing(); app.UseAbpSerilogEnrichers(); app.UseConfiguredEndpoints(); app.UseUnitOfWork(); //app.UseIdentityServer(); app.UseAuthorization(); app.UseMiddleware<RedirectClientMiddleware>(); } -
0
same issue
-
0
hi
What are the logs of the AuthServer project?
-
0
hi
What are the logs of the AuthServer project?
with the tenant issue
-
0
hi
** If there are calls to app.UseRouting() and app.UseEndpoints(...), the call to app.UseAuthorization() must go between them.**
is this correct?
No. Please check https://github.com/abpframework/abp/blob/dev/templates/module/aspnet-core/host/MyCompanyName.MyProjectName.AuthServer/MyProjectNameAuthServerModule.cs#L211-L233
-
0
public override void OnApplicationInitialization(ApplicationInitializationContext context) { var app = context.GetApplicationBuilder(); var env = context.GetEnvironment(); if (env.IsDevelopment()) { app.UseDeveloperExceptionPage(); } if (!env.IsDevelopment()) { app.UseErrorPage(); } app.UseHttpsRedirection(); app.UseCorrelationId(); app.UseStaticFiles(); app.UseRouting(); app.UseCors(); app.UseAuthentication(); app.UseAbpOpenIddictValidation(); if (MultiTenancyConsts.IsEnabled) { app.UseMultiTenancy(); } //app.UseJwtTokenMiddleware(); app.UseAbpRequestLocalization(options => { options.RequestCultureProviders.RemoveAll(x => x.GetType() == typeof(AcceptLanguageHeaderRequestCultureProvider)); options.SetDefaultCulture("en-US"); }); app.UseAuthorization(); app.UseAuditing(); app.UseAbpSerilogEnrichers(); app.UseConfiguredEndpoints(); app.UseUnitOfWork(); //app.UseIdentityServer(); app.UseMiddleware<RedirectClientMiddleware>(); } -
0
hi
Your code is different from our template.
https://github.com/abpframework/abp/blob/dev/templates/module/aspnet-core/host/MyCompanyName.MyProjectName.AuthServer/MyProjectNameAuthServerModule.cs#L211-L233
https://github.com/abpframework/abp/blob/dev/templates/app/aspnet-core/src/MyCompanyName.MyProjectName.AuthServer/MyProjectNameAuthServerModule.cs#L191-L226
The UseConfiguredEndpoints have to be the last middleware.
-
0
and what about this line order?
app.UseMiddleware<RedirectClientMiddleware>(); -
0
What is the code of
RedirectClientMiddleware?If it will control the
HTTP requestit must be beforeUseConfiguredEndpoints -
0
i have reordered them
but issue still exists
2024-01-17 15:33:34.395 +02:00 [INF] CORS policy execution failed. 2024-01-17 15:33:34.411 +02:00 [INF] Request origin https://localhost:44394 does not have permission to access the resource. 2024-01-17 15:33:34.436 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. -
0
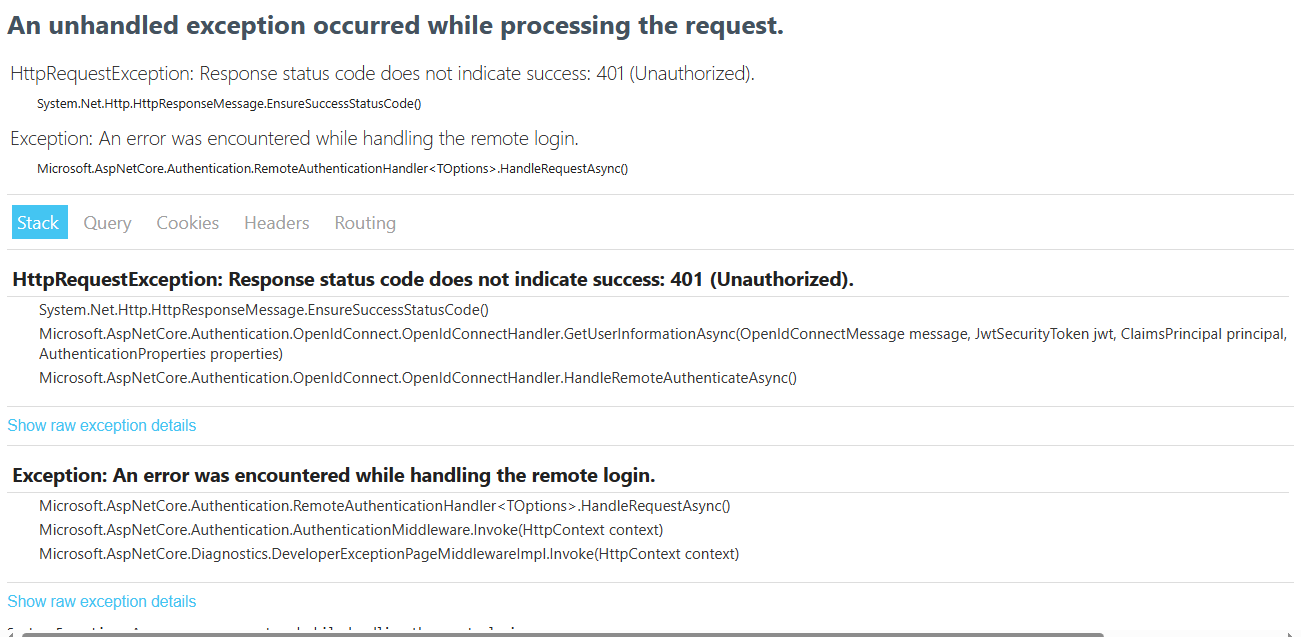
2024-01-17 15:35:34.908 +02:00 [ERR] Exception occurred while processing message. System.Net.Http.HttpRequestException: Response status code does not indicate success: 401 (Unauthorized). at System.Net.Http.HttpResponseMessage.EnsureSuccessStatusCode() at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.GetUserInformationAsync(OpenIdConnectMessage message, JwtSecurityToken jwt, ClaimsPrincipal principal, AuthenticationProperties properties) at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.HandleRemoteAuthenticateAsync() 2024-01-17 15:35:34.941 +02:00 [INF] Error from RemoteAuthentication: Response status code does not indicate success: 401 (Unauthorized).. 2024-01-17 15:35:34.961 +02:00 [ERR] An unhandled exception has occurred while executing the request. System.Exception: An error was encountered while handling the remote login. ---> System.Net.Http.HttpRequestException: Response status code does not indicate success: 401 (Unauthorized). at System.Net.Http.HttpResponseMessage.EnsureSuccessStatusCode() at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.GetUserInformationAsync(OpenIdConnectMessage message, JwtSecurityToken jwt, ClaimsPrincipal principal, AuthenticationProperties properties) at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.HandleRemoteAuthenticateAsync() --- End of inner exception stack trace --- at Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler`1.HandleRequestAsync() at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context) at Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddlewareImpl.Invoke(HttpContext context)
-
0
hi
Please try a host user. I think your multi-tenant middleware is not working correctly.
What is the content of your authserver module code now?
-
0
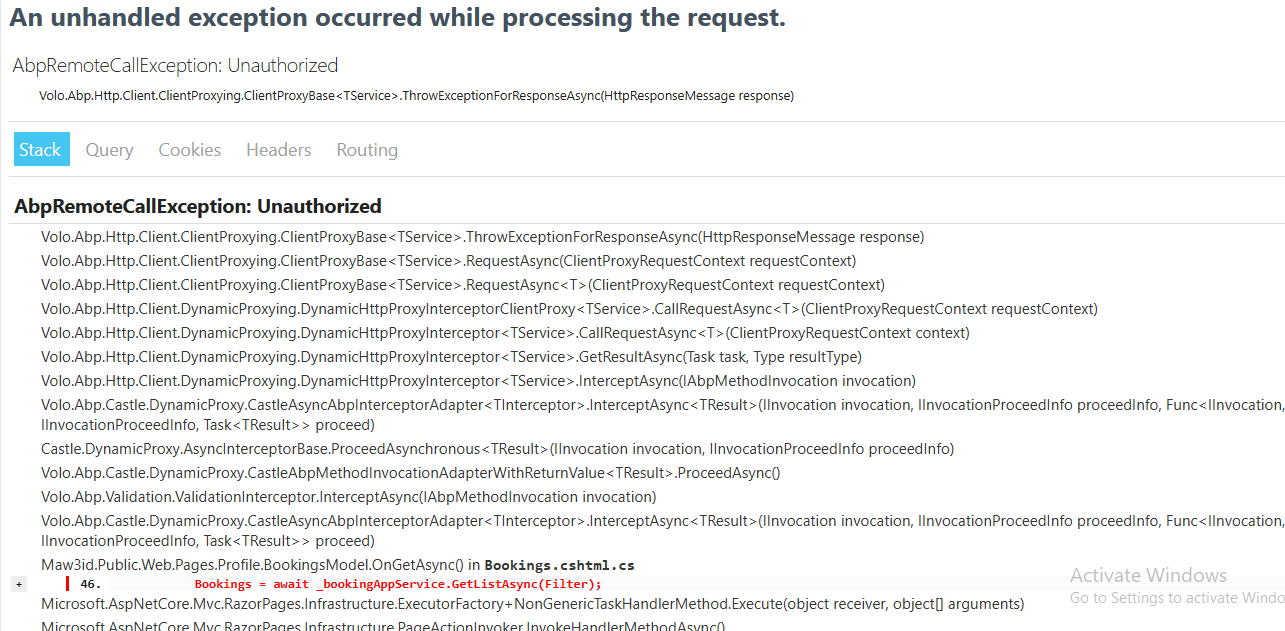
the host user does not have permission for the tenant, the tenant user login normally, but the issue is while redirecting to tenant dashboard
-
0
hi
Please share a simple project to reproduce liming.ma@volosoft.com
Thanks
-
0
and this this for tenant
-
0
https://support.abp.io/QA/Questions/6511/Upgrading-from-IdentityServer-to-OpenIdDict-issues#answer-3a102d5b-cd53-0e52-33f1-dc93f1ca8c88
-
0
https://support.abp.io/QA/Questions/6511/Upgrading-from-IdentityServer-to-OpenIdDict-issues#answer-3a102d5b-cd53-0e52-33f1-dc93f1ca8c88
it is difficult for me to create another simple one as the project is big and has a lot of modules, projects and configurations!!
Please let me know what classes or configurations should i check due to the sent logs.
-
0
-
0
hi
Please share full code of
Maw3idIdentityServerModuleto liming.ma@volosoft.com