- ABP Framework version: v4.0.0
- UI type: Angular
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): no
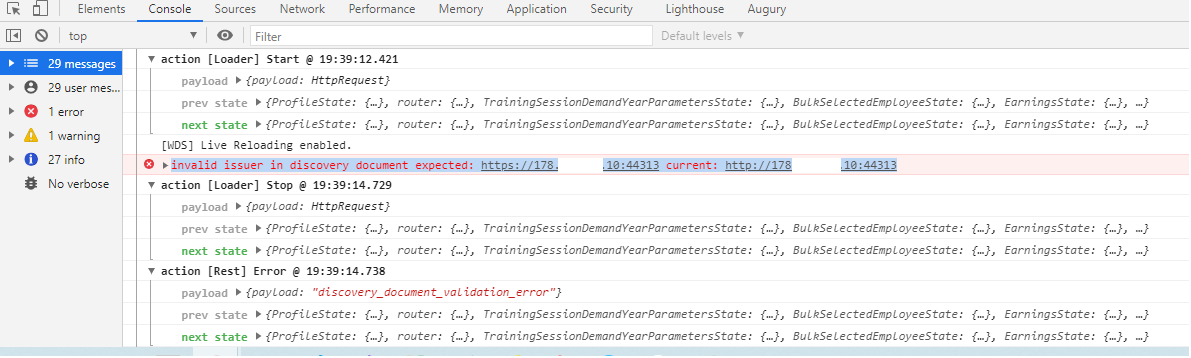
Having "invalid issuer in discovery document expected: https://remoteIp current: http://remoteIp" error when trying to access application over localhost:4200 or http://remoteIp:4200/(frontend on the remote machine)
Here is the app environment specifications
- Nginx reverse proxy
- with 2 active api nodes
- Ubuntu 20.04 instance with ports 80, 443, and 4200 allowed
- RDBMS database setup as postgreSQL 12.4
- dotnet service related to localhost:44313 (Nginx redirects public_ip:44313 to this)
We deploy our application by docker-compose on our pipe definition; frontend : docker-compose up -d --build
version: '3'
services:
web:
build:
context: .
# dockerfile: Dockerfile.dev
ports:
- "8080:443"
stdin_open: true
volumes:
- /app/node_modules
- .:/app
backend : docker-compose up -d --scale api=2 --build
version: '3'
services:
nginx:
image: nginx:alpine
hostname: 'nginx'
volumes:
- ./nginx/nginx.conf:/etc/nginx/nginx.conf:ro
- ./nginx/proxy.conf:/etc/nginx/proxy.conf:ro
- ./nginx/logs/:/var/log/nginx/
- ./nginx/certs:/etc/nginx/certs
ports:
- '80:80'
- '443:443'
depends_on:
- api
restart: always
api:
build: ./
stdin_open: true
ports:
- '44313'
restart: always
<br> Angular environment file;
import { Environment } from '@abp/ng.core';
const baseUrl = 'http://remoteIp:4200';
export const environment = {
production: false,
application: {
baseUrl,
name: 'AppName'
},
oAuthConfig: {
issuer: 'https://remoteIp',
redirectUri: baseUrl,
clientId: 'AppName_App',
responseType: 'code',
scope: 'offline_access moduleOne'
},
apis: {
default: {
url: 'https://remoteIp',
rootNamespace: 'ModuleOne'
},
ModuleTwo: {
rootNamespace: "ModuleTwo",
url: 'https://remoteIp'
}
},
localization: {
defaultResourceName: 'moduleOne'
}
} as Environment;
appsettings.json <br>
{
"App": {
"SelfUrl": "https://178.157.14.10",
"CorsOrigins": "https://*.appname.com,http://localhost:4200,http://remoteIp:4200," },
"ConnectionStrings": {
"Default": "connString1",
"Module2": "connString2"
},
"AuthServer": {
"Authority": "https://remoteIp"
}
}
Nginx conf file
user nginx;
worker_processes auto;
events { worker_connections 1024; }
http {
include /etc/nginx/proxy.conf;
include /etc/nginx/mime.types;
limit_req_zone $binary_remote_addr zone=one:10m rate=5r/s;
server_tokens off;
sendfile on;
keepalive_timeout 29;
client_body_timeout 10;
client_header_timeout 10;
send_timeout 10;
upstream webapi {
server api:44313;
}
server {
listen *:80 default_server;
add_header Strict-Transport-Security max-age=15768000;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name $hostname;
ssl_certificate /etc/nginx/certs/AppNameApi.crt;
ssl_certificate_key /etc/nginx/certs/AppNameApi.key;
ssl_protocols TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers "EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH";
ssl_ecdh_curve secp384r1;
ssl_session_cache shared:SSL:10m;
ssl_session_tickets off;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error_log crit;
location / {
proxy_pass https://webapi;
proxy_set_header Host $host:44313;
error_log /var/log/apierrors.log;
limit_req zone=one burst=10 nodelay;
}
}
}
And the result is as below, both from remote front end and the local are the same.
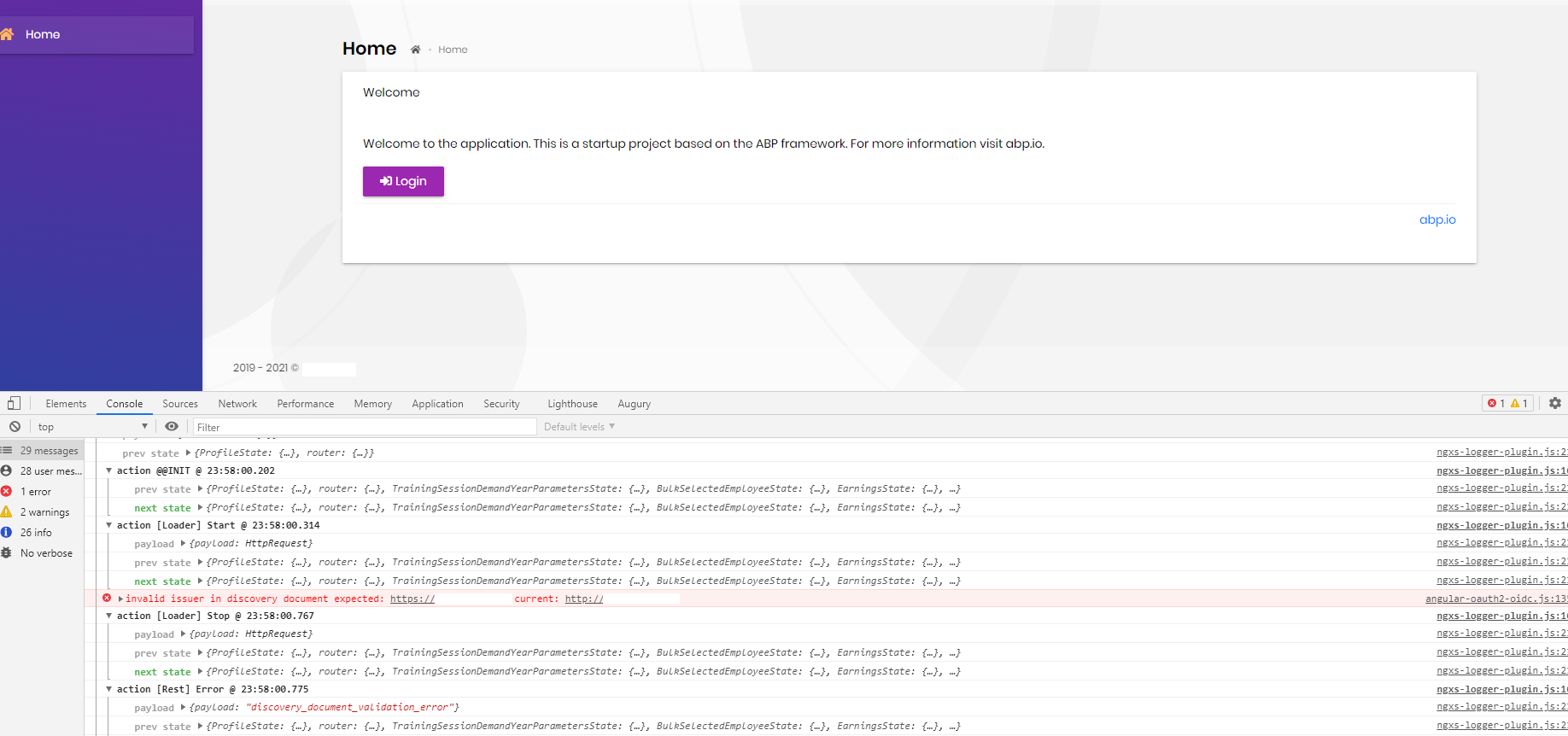 I couldn't see any errors others than "invalid issuer in discovery document expected: [https://remoteIp] current: [http://remoteIp]". After this exception as if everything is frozen. No action could be made.
I couldn't see any errors others than "invalid issuer in discovery document expected: [https://remoteIp] current: [http://remoteIp]". After this exception as if everything is frozen. No action could be made.
By the way I should mention that we don't get error when trying it on local without nginx. Why are we having this error, could you help us please? P.S. We reviewed the record with #465(which is relevant to the same error) and try everything mentioned. (I can give remote addresses if needed in advance.)
6 Answer(s)
-
0
check that your issuer is configured as:
issuer: 'https://localhost:44313',inenvironment.prod.tsalso be aware that these are local addresses. when you deploy it to prod, you need to set it to your real domain names.
-
0
-
0
check that your issuer is configured as:
issuer: 'https://localhost:44313',inenvironment.prod.tsalso be aware that these are local addresses. when you deploy it to prod, you need to set it to your real domain names.
Any comment?
-
0
you are working with public IP and you cannot bind an SSL certificate to an IP. Identity Server doesn't work when there's no HTTPS. This is not an ABP related issue.
-
0
-
0
This is the thread which I suffered with I think. https://github.com/dotnet/aspnetcore/issues/7246 You are right, it's not about abp. We have to check our certificate file. Thanks for your support anyway.