Activities of "Dina"
- ABP Framework version: v7.4
- UI Type: MVC
- Database System: EF Core (SQL Server)
- Steps to reproduce the issue:
Hi,
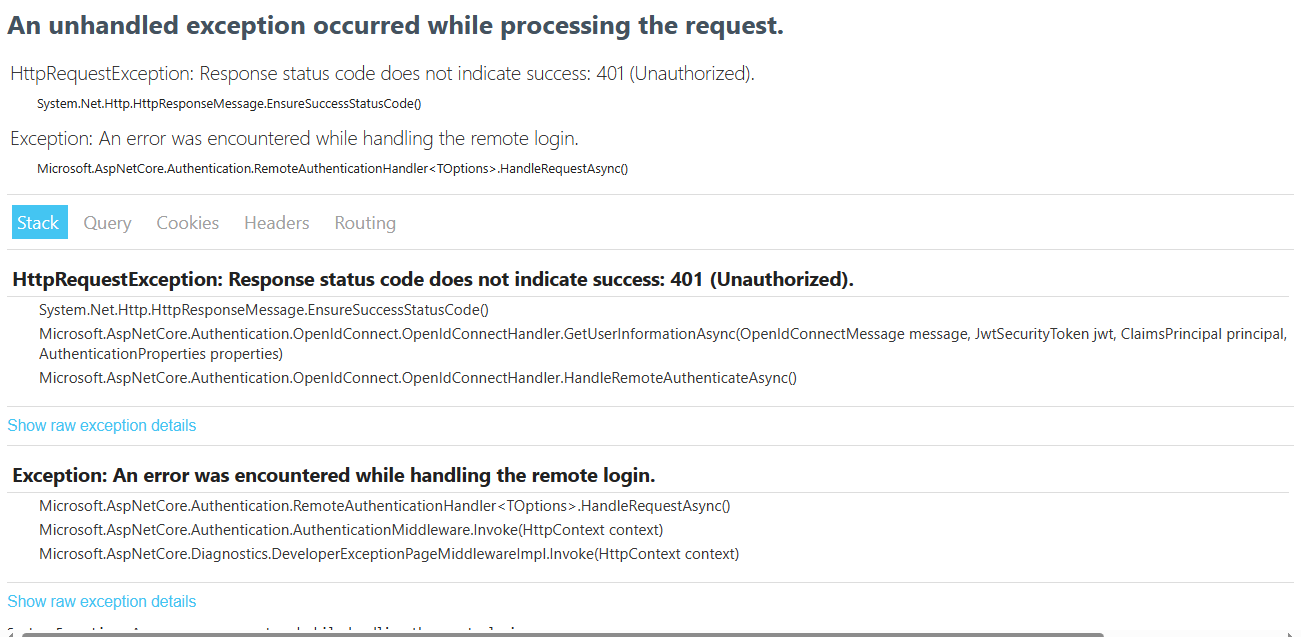
We recently upgraded our authentication system from IdentityServer to OpenIdDict. However, we're currently facing an issue with internal login. After the upgrade, when we request a token and successfully validate it, the "Current User" in our web application shows as authenticated. However, when we try to retrieve data from the application project, the "Current User" is not authenticated.
Here's the code snippet we're using for authentication:
public async Task<AuthenticateResult> Authenticate(string phoneNumber, string code)
{
var disc = await httpClient.GetDiscoveryDocumentAsync(_options.CurrentValue.Authority);
var request = new TokenRequest
{
Address = _options.CurrentValue.Authority + _options.CurrentValue.TokenEndPoint,
GrantType = Re3aytak.Identity.PhoneNumberLoginConsts.GrantType,
ClientId = _options.CurrentValue.ClientId,
ClientSecret = _options.CurrentValue.ClientSecret,
Parameters =
{
{"phone_number", phoneNumber},
{"code", code}
}
};
var configManager = new ConfigurationManager<OpenIdConnectConfiguration>($"{_options.CurrentValue.Authority}/.well-known/openid-configuration", new OpenIdConnectConfigurationRetriever());
var openidconfig = await configManager.GetConfigurationAsync();
var result = await httpClient.RequestTokenAsync(request);
// success branch
// generate authTicket
// authenticate the request
if (!result.IsError)
{
var TokenValidationParameters = new TokenValidationParameters()
{
ValidateAudience = false,
ValidateIssuer = true,
ValidIssuers = new[] { $"{_options.CurrentValue.Authority}/" },
ValidIssuer= $"{_options.CurrentValue.Authority}/",
ValidateIssuerSigningKey = true,
IssuerSigningKeys = openidconfig.SigningKeys,
RequireExpirationTime = true,
ValidateLifetime = true,
RequireSignedTokens = true,
};
JwtSecurityTokenHandler jwtSecurityTokenHandler = new JwtSecurityTokenHandler();
var claimsPrinciples = jwtSecurityTokenHandler.ValidateToken(result.AccessToken,
TokenValidationParameters,
out SecurityToken validatedToken);
var AuthenticationProperties = new AuthenticationProperties();
if (_options.CurrentValue.SaveTokens)
{
var authTokens = new List<AuthenticationToken>();
authTokens.Add(new AuthenticationToken { Name = "access_token", Value = result.AccessToken });
if (!string.IsNullOrEmpty(result.RefreshToken))
{
authTokens.Add(new AuthenticationToken { Name = "refresh_token", Value = result.RefreshToken });
}
if (!string.IsNullOrEmpty(result.TokenType))
{
authTokens.Add(new AuthenticationToken { Name = "token_type", Value = result.TokenType });
}
if (result.ExpiresIn != 0)
{
var expiresAt = (DateTime.UtcNow + TimeSpan.FromSeconds(result.ExpiresIn)).AddDays(1);
authTokens.Add(new AuthenticationToken
{
Name = "expires_at",
Value = expiresAt.ToString("o", CultureInfo.InvariantCulture)
});
AuthenticationProperties.ExpiresUtc = expiresAt;
}
AuthenticationProperties.StoreTokens(authTokens);
}
// generate AuthenticationTicket from the Identity
// and current authentication scheme
var ticket = new AuthenticationTicket(claimsPrinciples,AuthenticationProperties, "Cookies");
// pass on the ticket to the middleware
return AuthenticateResult.Success(ticket);
}
return AuthenticateResult.Fail(result.Error);
}
Here's a code from web project
var result = await _passwordlessAuthenticator.Authenticate(phonenumber, code);
if (result.Succeeded)
{
await HttpContext.SignInAsync("Cookies", result.Principal, result.Properties);
HttpContext.User = result.Principal;
}
- ABP Framework version: v7.4.2
- UI Type: MVC(SQL)
Hi,
After we upgraded from IdentityServer to OpenIdDict there were some issues
We have an Admin application (which is working fine) and Clinic application which has an issue while redirecting to the application dashboard after signing in using OpenId
Please advise ASAP.
- ABP Framework version: v7.4
- UI Type: MVC
- Database System: EF Core (SQL Server)
Hi,
How can we add extra setting in general settings area in toolbar in LeptonX version 2.4 please?
ABP Framework version: v7.4 UI Type: MVC Database System: EF Core (SQL Server)
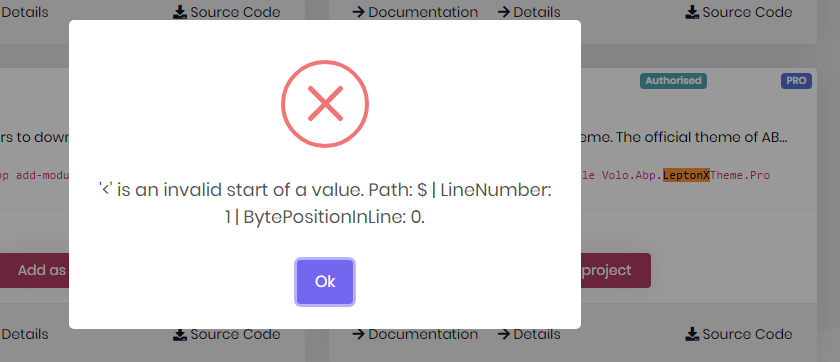
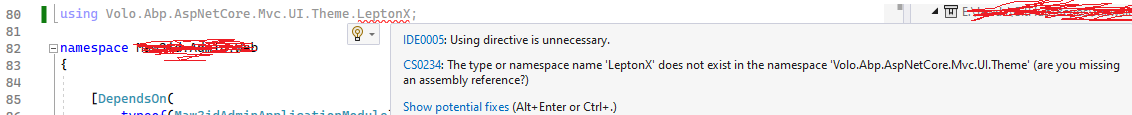
Hi, We have an issue while upgrading a project from abp version 5 to 7.4.2, we want to use LeptonX instead of the Lepton theme.
So when we run the command "dotnet add package Volo.Abp.AspNetCore.Mvc.UI.Theme.LeptonX --prerelease"
using Volo.Abp.AspNetCore.Mvc.UI.Theme.LeptonX;
is added to the ProjectWebModule.cs , but the package is not installed !!
- ABP Framework version: v7.4
- UI Type: MVC
- Database System: EF Core (SQL Server)
Hi, We are upgrading an abp project from 5 to 7.4 We have done the abp update command and fixed about 2000 errors related to used packages. And now we have some syntax errors related to the identityServer module.
We want a documentation or steps in which we can fix the upgrading errors between these 2 versions directly.
Regards, Dina
- ABP Framework version: v7.2.2
- UI type: MVC
- DB provider: EF Core
- Exception message and stack trace:
- Steps to reproduce the issue:"
Hi,
We have upgraded from abp version 7 to 7.2.2, then we got an exception while calling profileAppService.GetAsync() at the production only
System.InvalidOperationException: The exception handler configured on ExceptionHandlerOptions produced a 404 status response. This InvalidOperationException containing the original exception was thrown since this is often due to a misconfigured ExceptionHandlingPath. If the exception handler is expected to return 404 status responses then set AllowStatusCode404Response to true.
---> Volo.Abp.Http.Client.AbpRemoteCallException: Service Unavailable
at Volo.Abp.Http.Client.ClientProxying.ClientProxyBase1.ThrowExceptionForResponseAsync(HttpResponseMessage response) at Volo.Abp.Http.Client.ClientProxying.ClientProxyBase1.RequestAsync(ClientProxyRequestContext requestContext)
at Volo.Abp.Http.Client.ClientProxying.ClientProxyBase1.RequestAsync[T](ClientProxyRequestContext requestContext) at Volo.Abp.Http.Client.ClientProxying.ClientProxyBase1.RequestAsync[T](String methodName, ClientProxyRequestTypeValue arguments)
at Volo.Abp.Account.ProfileClientProxy.GetAsync()
Note: we have 2 production servers, only one has this issue and the other is working fine!
Waiting for your reply Thanks.
- ABP Framework version: v7.0.0-rc3
- UI type: MVC
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes
- Exception message and stack trace:
- Steps to reproduce the issue:"
Hi,
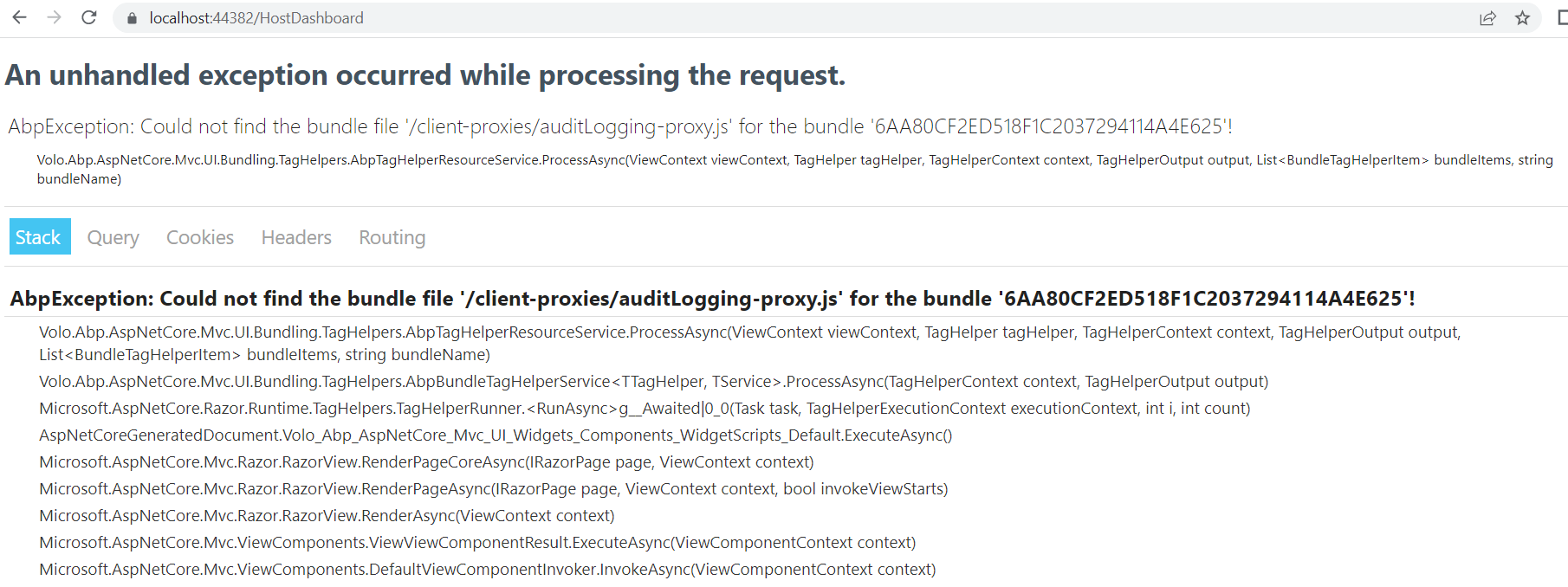
We have some issues with our abp project One of them is when overriding the Account module localization with a new localization json files
The localized texts values are shown correctly ONLY at development mode, but when we deploy the version to the server, the localization is not working
the used code at openIdDict authentication project
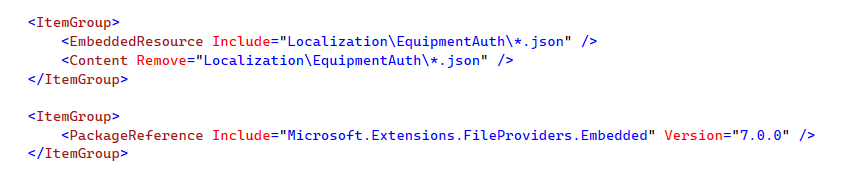
`Configure(options => { options.FileSets.AddEmbedded();
if (hostingEnvironment.IsDevelopment())
{
options.FileSets.ReplaceEmbeddedByPhysical<EquipmentSharingAuthServerModule>(hostingEnvironment.ContentRootPath);
}
});`
Configure<AbpLocalizationOptions>(options => { options.Resources .Add<EquipmentAuthResource>("en-US") .AddVirtualJson("/Localization/EquipmentAuth") .AddBaseTypes(typeof(AccountResource)); //Inherit from an existing resource });
Is there anything missing to make the localization works properly on the server?
Waiting for your response
- ABP Framework version: v"7.0.0-rc.3"
- UI type MVC
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes
- Exception message and stack trace:
- Steps to reproduce the issue:"
Hi,
We are working on a new abp project (version 7) and we have some issues 1- When we updated the abp today from "7.0.0-rc.2" to "7.0.0-rc.3", we faced issue
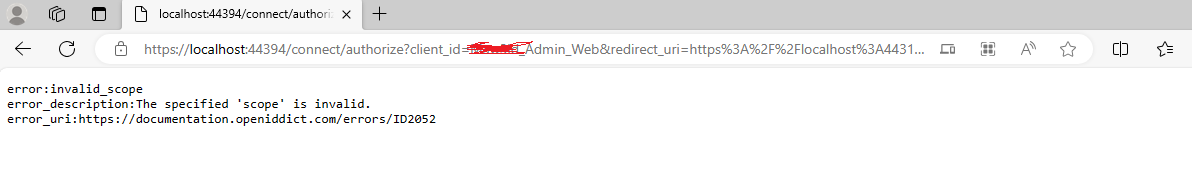
2- we have 3 projects and each one should have different logic and UI for login process, so we created a middleware at the openiddict auth to handle each project request but we faced 2 issues
- First, the “context.Request.HttpContext.GetOpenIddictServerRequest()” is always null, so we can not get the application and check on it
var request = context.Request.HttpContext.GetOpenIddictServerRequest(); if (request.IsClientCredentialsGrantType()) { var application = await _applicationManager.FindByClientIdAsync(request.ClientId); if (application == null) { throw new InvalidOperationException("The application details cannot be found in the database."); } var app = await _applicationManager.GetClientIdAsync(application);
- And second, when injecting (OpenIddictServerAspNetCoreHandler, IAuthenticationRequestHandler or OpenIddictServerHandlerDescriptor) we face error "ABP-LIC-0013 - License exception: ABP-LIC-0023: An error occured while calling the license server! The input is not a valid Base-64 string as it contains a non-base 64 character, more than two padding characters, or an illegal character among the padding characters."
So, please we want an openiddict middleware sample in which we get the ClientId and check on its value
Waiting for you reply Thanks