Activities of "heshengli"
ABP Framework version: v7.2.2
UI Type: / Blazor Server
Database System: EF Core ( PostgreSQL)
Tiered (for MVC) or Auth Server Separated (for Angular): yes
Exception message and full stack trace:
Steps to reproduce the issue:
Database: AbpPermissions table has 1200 rows AbpPermissionGroups table has 112 rows
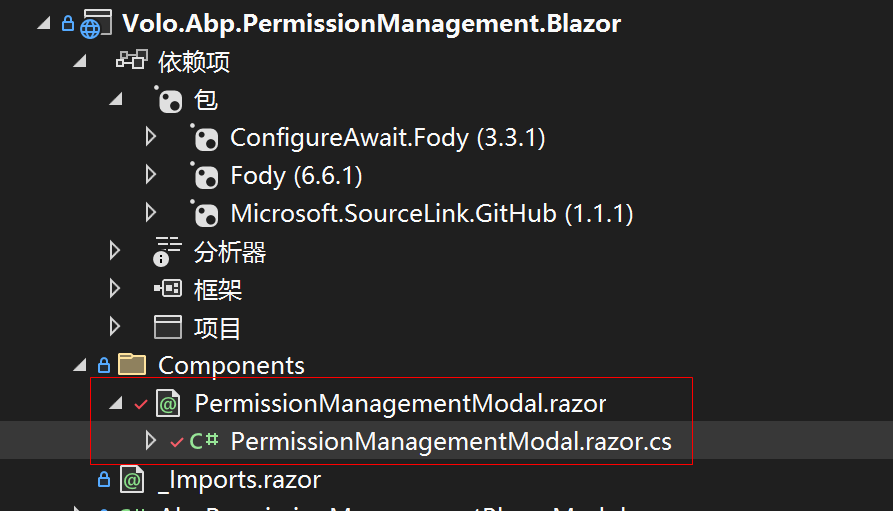
Abp Code: Volo.Abp.PermissionManagement
var result = await PermissionAppService.GetAsync(_providerName, _providerKey);
- logs:
2023-12-15 02:52:50.633 +00:00 [INF] Request finished HTTP/1.1 GET /api/permission-management/permissions?providerName=R&providerKey=user&api-version=1.0 - 0 - 200 - application/json;+charset=utf-8 12973.1867ms
When the server performance is better, it's a little faster, but it's still 5 seconds. Click the permissions pop-up window, the reaction time is still too long, no task prompt.
nginx proxy, the port will not be available
no use nginx proxy , not error
all configurations come form applications template project,but authsever、app、api is nginx proxy , the domain is nginx proxy address
i known,but the also is abpframework send request
Clear the redis cache without resolving the error
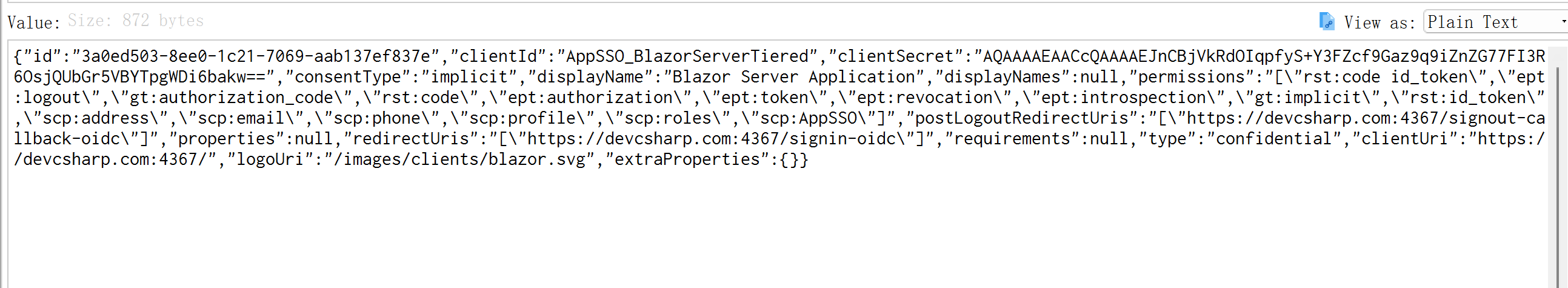
{"id":"3a0ed503-8ee0-1c21-7069-aab137ef837e","clientId":"AppSSO_BlazorServerTiered","clientSecret":"AQAAAAEAACcQAAAAEJnCBjVkRdOIqpfyS+Y3FZcf9Gaz9q9iZnZG77FI3R6OsjQUbGr5VBYTpgWDi6bakw==","consentType":"implicit","displayName":"Blazor Server Application","displayNames":null,"permissions":"[\"rst:code id_token\",\"ept:logout\",\"gt:authorization_code\",\"rst:code\",\"ept:authorization\",\"ept:token\",\"ept:revocation\",\"ept:introspection\",\"gt:implicit\",\"rst:id_token\",\"scp:address\",\"scp:email\",\"scp:phone\",\"scp:profile\",\"scp:roles\",\"scp:AppSSO\"]","postLogoutRedirectUris":"[\"https://devcsharp.com:4367/signout-callback-oidc\"]","properties":null,"redirectUris":"[\"https://devcsharp.com:4367/signin-oidc\"]","requirements":null,"type":"confidential","clientUri":"https://devcsharp.com:4367/","logoUri":"/images/clients/blazor.svg","extraProperties":{}}
- ABP Framework version: v7.4.1
- UI Type: Blazor Server
- Database System: EF Core (PostgreSQL)
- Tiered (for MVC) or Auth Server Separated (for Angular): yes
- Exception message and full stack trace:
- Steps to reproduce the issue:
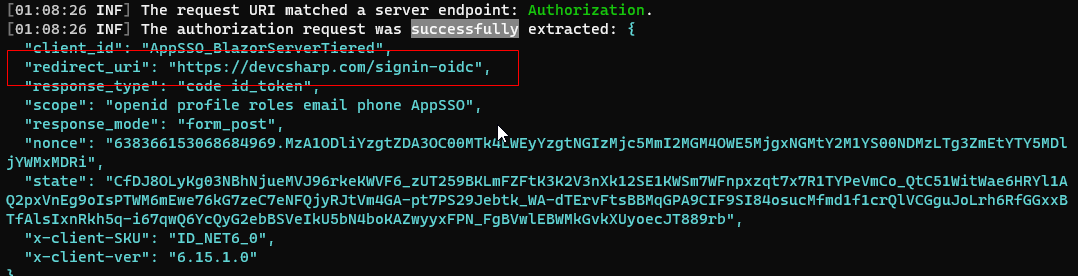
the doman is https://devcsharp:4367 .
and show https://devcsharp in log ,lead to redirect failed
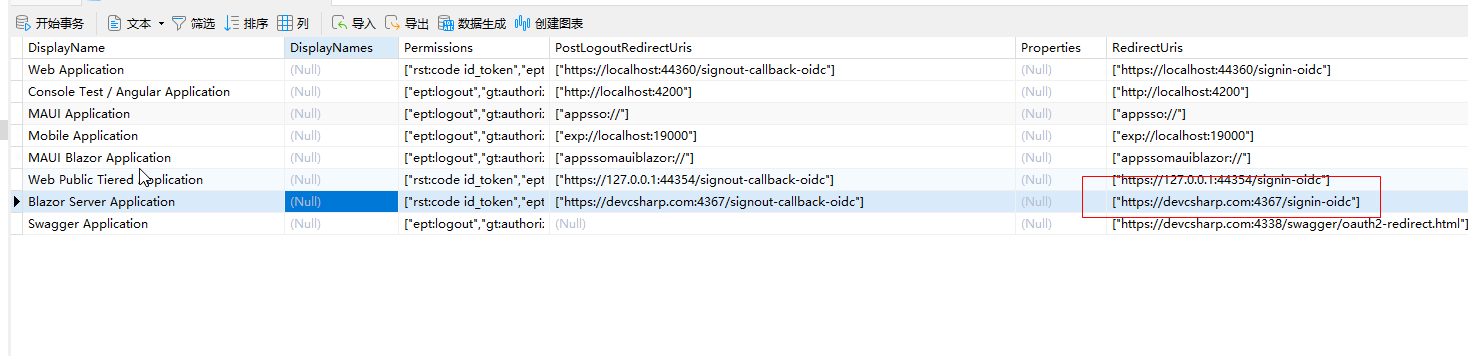
- ABP Framework version: v7.4.1
- UI Type: Blazor Server
- Database System: PostgreSQL,
- Tiered (for MVC) or Auth Server Separated (for Angular): yes
- Exception message and full stack trace:
- Steps to reproduce the issue: AuthServer publish http address http://10.10.22.18:44880/
nginx ssl https://dimain:9900 proxy_pass http://10.10.22.18:44880/;
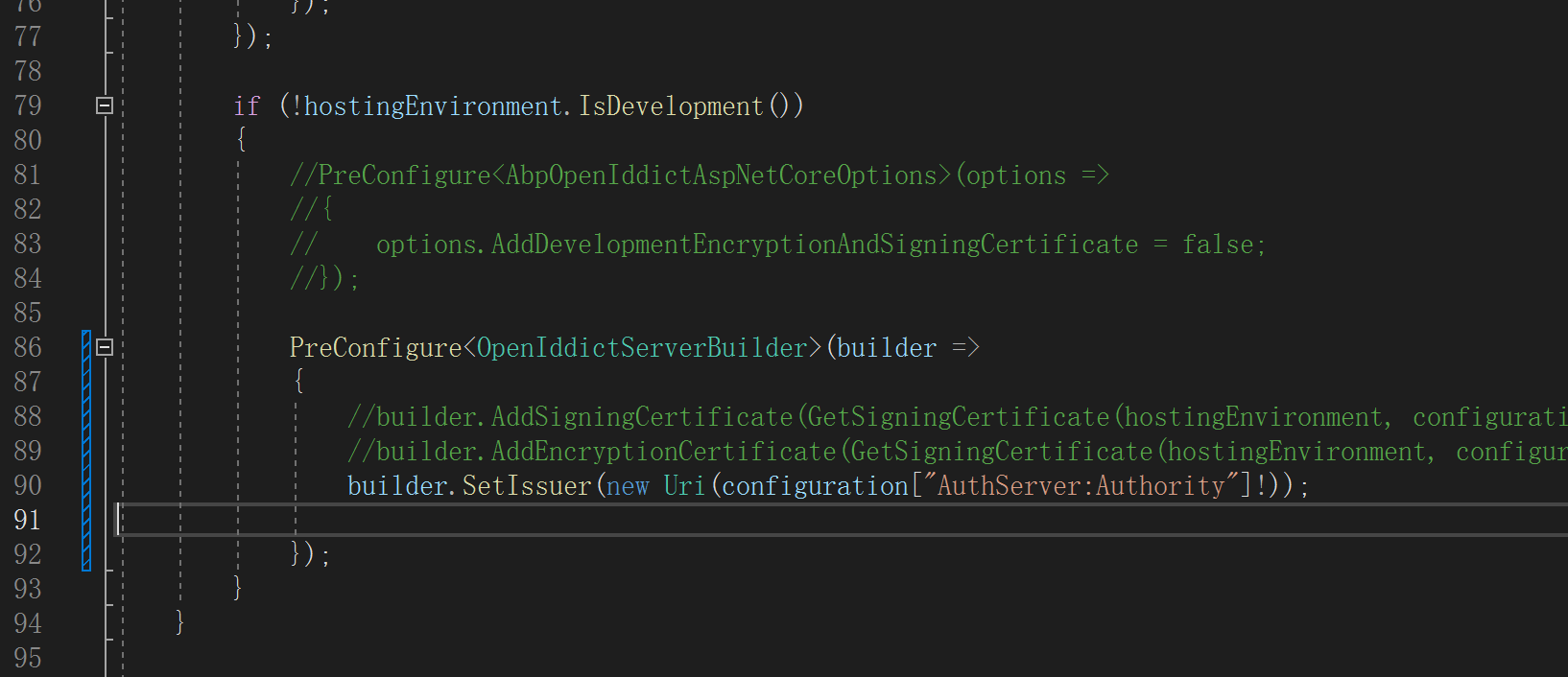
**AuthServerModule Config Code
authserverHost
/.well-known/openid-configuration
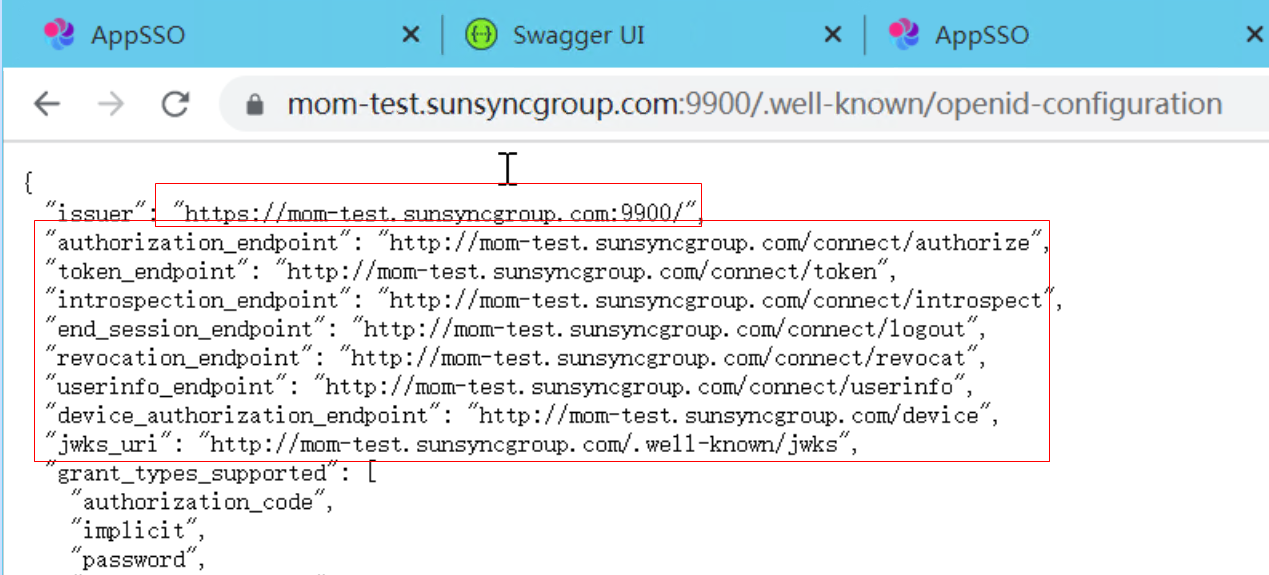
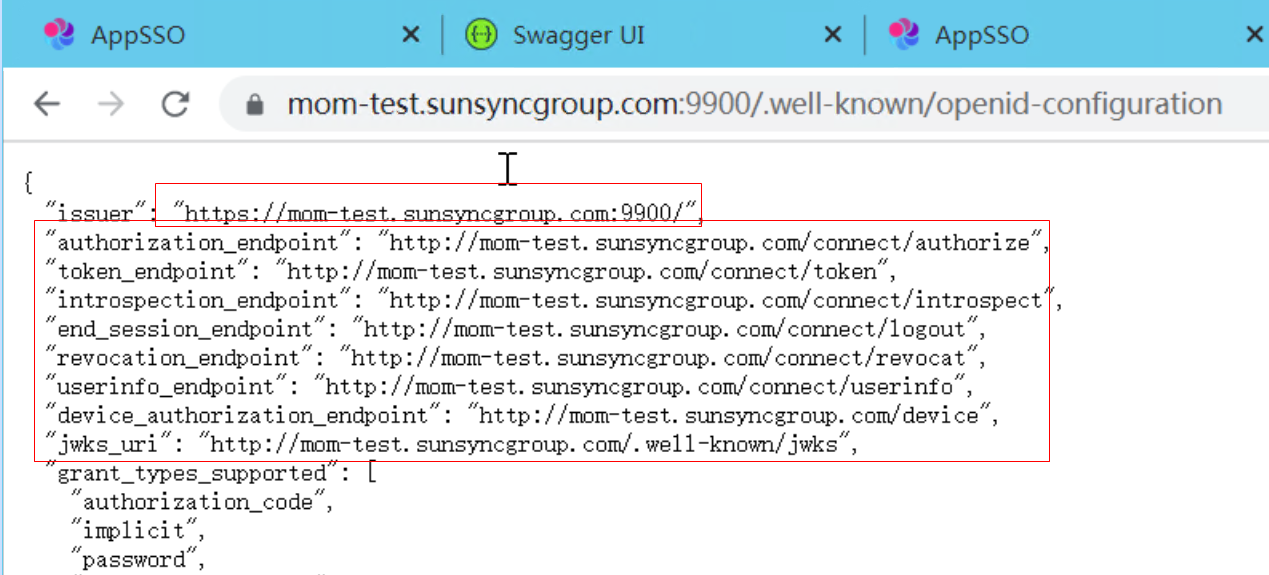
why issuer ip address and authorization_endpoint ip address not same
https://support.abp.io/QA/Questions/2644/OpenIdConnectAuthenticationHandler-messageState-is-null-or-empty--Where-do-I-need-to-configure-this-error same error, how solve
Check the docs before asking a question: https://docs.abp.io/en/commercial/latest/ Check the samples to see the basic tasks: https://docs.abp.io/en/commercial/latest/samples/index The exact solution to your question may have been answered before, and please first use the search on the homepage. Provide us with the following info:
- ABP Framework version: v7.2.2
- UI Type: Angular / MVC / Blazor WASM / Blazor Server
- Database System: EF Core (SQL Server, Oracle, MySQL, PostgreSQL, etc..) / MongoDB
- Tiered (for MVC) or Auth Server Separated (for Angular): yes/no
- Exception message and full stack trace:
- Steps to reproduce the issue: -5. create abp commercial Microservice template project -6. 2 ceate abp commercial Application template mvc project integration sso Microservice project
public override void ConfigureServices(ServiceConfigurationContext context)
{
var hostingEnvironment = context.Services.GetHostingEnvironment();
var configuration = context.Services.GetConfiguration();
if (!Convert.ToBoolean(configuration["App:DisablePII"]))
{
Microsoft.IdentityModel.Logging.IdentityModelEventSource.ShowPII = true;
}
ConfigureSameSiteCookiePolicy(context);//Cookies
ConfigureBundles();
//ConfigurePages(configuration);
ConfigureCache(configuration);
ConfigureDataProtection(context, configuration, hostingEnvironment);
ConfigureDistributedLocking(context, configuration);
ConfigureUrls(configuration);
//=====================
ConfigureAuthentication(context, configuration);
ConfigureImpersonation(context, configuration);
ConfigureAutoMapper();
ConfigureVirtualFileSystem(hostingEnvironment);
ConfigureNavigationServices(configuration);
ConfigureSwaggerServices(context.Services);
ConfigureMultiTenancy();
ConfigureBackgroundJobs();
ConfigureCookieConsent(context);//Cookies
ConfigureTheme();
}
private void ConfigureSameSiteCookiePolicy(ServiceConfigurationContext context)
{
context.Services.AddSameSiteCookiePolicy();
}
private void ConfigureCookieConsent(ServiceConfigurationContext context)
{
context.Services.AddAbpCookieConsent(options =>
{
options.IsEnabled = true;
options.CookiePolicyUrl = "/CookiePolicy";
options.PrivacyPolicyUrl = "/PrivacyPolicy";
});
}
private void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration)
{
context.Services.AddAuthentication(options =>
{
options.DefaultScheme = "Cookies";
options.DefaultChallengeScheme = "oidc";
})
.AddCookie("Cookies", options =>
{
options.ExpireTimeSpan = TimeSpan.FromDays(365);
})
.AddAbpOpenIdConnect("oidc", options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]);
options.ResponseType = OpenIdConnectResponseType.CodeIdToken;
options.ClientId = configuration["AuthServer:ClientId"];
options.ClientSecret = configuration["AuthServer:ClientSecret"];
//options.UsePkce = true;
options.SaveTokens = true;
options.GetClaimsFromUserInfoEndpoint = true;
options.Scope.Add("roles");
options.Scope.Add("email");
options.Scope.Add("phone");
options.Scope.Add("AccountService");
options.Scope.Add("IdentityService");
options.Scope.Add("AdministrationService");
options.Scope.Add("WorkflowEngine");
});
/*
* This configuration is used when the AuthServer is running on docker containers at localhost.
* Configuring the redirectin URLs for internal network and the web
*/
if (Convert.ToBoolean(configuration["AuthServer:IsContainerizedOnLocalhost"]))
{
context.Services.Configure<OpenIdConnectOptions>("oidc", options =>
{
options.TokenValidationParameters.ValidIssuers = new[]
{
configuration["AuthServer:MetaAddress"].EnsureEndsWith('/'),
configuration["AuthServer:Authority"].EnsureEndsWith('/')
};
options.MetadataAddress = configuration["AuthServer:MetaAddress"].EnsureEndsWith('/') +
".well-known/openid-configuration";
var previousOnRedirectToIdentityProvider = options.Events.OnRedirectToIdentityProvider;
options.Events.OnRedirectToIdentityProvider = async ctx =>
{
// Intercept the redirection so the browser navigates to the right URL in your host
ctx.ProtocolMessage.IssuerAddress = configuration["AuthServer:Authority"].EnsureEndsWith('/') + "connect/authorize";
if (previousOnRedirectToIdentityProvider != null)
{
await previousOnRedirectToIdentityProvider(ctx);
}
};
var previousOnRedirectToIdentityProviderForSignOut = options.Events.OnRedirectToIdentityProviderForSignOut;
options.Events.OnRedirectToIdentityProviderForSignOut = async ctx =>
{
// Intercept the redirection for signout so the browser navigates to the right URL in your host
ctx.ProtocolMessage.IssuerAddress = configuration["AuthServer:Authority"].EnsureEndsWith('/') + "connect/logout";
if (previousOnRedirectToIdentityProviderForSignOut != null)
{
await previousOnRedirectToIdentityProviderForSignOut(ctx);
}
};
});
}
}
public override void OnApplicationInitialization(ApplicationInitializationContext context)
{
var app = context.GetApplicationBuilder();
var env = context.GetEnvironment();
if (env.IsDevelopment())
{
app.UseDeveloperExceptionPage();
}
app.UseAbpRequestLocalization();
if (!env.IsDevelopment())
{
app.UseErrorPage();
}
app.UseCookiePolicy();//Cookies
//app.UseAbpCookieConsent();
app.UseAbpSecurityHeaders();
app.UseStaticFiles();
app.UseRouting();
app.UseAuthentication();
if (MultiTenancyConsts.IsEnabled)
{
app.UseMultiTenancy();
}
app.UseAuthorization();
app.UseSwagger();
app.UseAbpSwaggerUI(options =>
{
options.SwaggerEndpoint("/swagger/v1/swagger.json", "WorkflowEngine API");
});
app.UseHttpActivities();//ELSA http activities
app.UseAbpSerilogEnrichers();
app.UseConfiguredEndpoints();
}
public static class SameSiteCookiesServiceCollectionExtensions
{
public static IServiceCollection AddSameSiteCookiePolicy(this IServiceCollection services)
{
services.Configure<CookiePolicyOptions>(options =>
{
options.MinimumSameSitePolicy = SameSiteMode.Unspecified;
options.OnAppendCookie = cookieContext =>
CheckSameSite(cookieContext.Context, cookieContext.CookieOptions);
options.OnDeleteCookie = cookieContext =>
CheckSameSite(cookieContext.Context, cookieContext.CookieOptions);
});
return services;
}
private static void CheckSameSite(HttpContext httpContext, CookieOptions options)
{
if (options.SameSite == SameSiteMode.None)
{
var userAgent = httpContext.Request.Headers["User-Agent"].ToString();
if (!httpContext.Request.IsHttps || DisallowsSameSiteNone(userAgent))
{
// For .NET Core < 3.1 set SameSite = (SameSiteMode)(-1)
options.SameSite = SameSiteMode.Unspecified;
}
}
}
private static bool DisallowsSameSiteNone(string userAgent)
{
// Cover all iOS based browsers here. This includes:
// - Safari on iOS 12 for iPhone, iPod Touch, iPad
// - WkWebview on iOS 12 for iPhone, iPod Touch, iPad
// - Chrome on iOS 12 for iPhone, iPod Touch, iPad
// All of which are broken by SameSite=None, because they use the iOS networking stack
if (userAgent.Contains("CPU iPhone OS 12") || userAgent.Contains("iPad; CPU OS 12"))
{
return true;
}
// Cover Mac OS X based browsers that use the Mac OS networking stack. This includes:
// - Safari on Mac OS X.
// This does not include:
// - Chrome on Mac OS X
// Because they do not use the Mac OS networking stack.
if (userAgent.Contains("Macintosh; Intel Mac OS X 10_14") &&
userAgent.Contains("Version/") && userAgent.Contains("Safari"))
{
return true;
}
// Cover Chrome 50-69, because some versions are broken by SameSite=None,
// and none in this range require it.
// Note: this covers some pre-Chromium Edge versions,
// but pre-Chromium Edge does not require SameSite=None.
if (userAgent.Contains("Chrome/5") || userAgent.Contains("Chrome/6"))
{
return true;
}
return false;
}
}
Cookies was not authenticated. Failure message: Unprotect ticket failed
SSO Login MVC Login Success,but not Perssions PortalApp F5 twice jump,login success,but mvc app F5 login failed