Activities of "jason.smith"
- ABP Framework version: v3.1.2
- UI type: Angular
- Tiered (MVC) or Identity Server Seperated (Angular): no (single host)
- Exception message and stack trace: None
- Steps to reproduce the issue:
The setup works find on the developers machine using localhost, and local database. Looking to now deploy using the following:
- Nginx reverse proxy
- host angular front end
- host API redirect
- AWS ec2 instance with ports 80, 443, and 5000 allowed
- RDS database setup as postgreSQL 12.4 (version used in development)
- dotnet kestrel service bound to localhost:5000 (Nginx redirects public_ip:5000 to this)
Angular environment file - replace <public_ip> with actual public address <br>
import { Config } from '@abp/ng.core';
const baseUrl = 'http://<public_ip>:80';
export const environment = {
production: false,
application: {
baseUrl,
name: 'Repros',
logoUrl: '',
},
oAuthConfig: {
issuer: 'http://<public_ip>:5000',
redirectUri: baseUrl,
clientId: 'Repros_App',
responseType: 'code',
scope: 'offline_access Repros',
},
apis: {
default: {
url: 'http://<public_ip>:5000',
rootNamespace: 'eWater.Repros'
},
},
} as Config.Environment;
<br> Http.Host environment file - again replace <public_ip> with actual public address, same for connection string <br>
{
"Urls": "[http://localhost:5000](http://localhost:5000)",
"App": {
"SelfUrl": "[http://localhost:5000](http://localhost:5000)",
"CorsOrigins": "http://<public_ip>,[http://localhost:80,http://localhost:4200](http://localhost:80,http://localhost:4200)"
},
"ConnectionStrings": {
"Default": "<connection_string>"
},
"AuthServer": {
"Authority": "[http://localhost:5000](http://localhost:5000)"
}
}
<br> Ngnix configuraiton file <br>
worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 0;
server {
listen 80;
index index.html;
root scenario-datastore-debug/dist;
ignore_invalid_headers off;
underscores_in_headers on;
location / {
try_files $uri %uri/ /index.html;
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
}
server {
listen 5000;
location / {
proxy_pass [http://127.0.0.1:5000](http://127.0.0.1:5000);
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}
<br> The resulting behaviour is the following:
- The front end starts up and the Angular front end loads into the index page with user logged out.
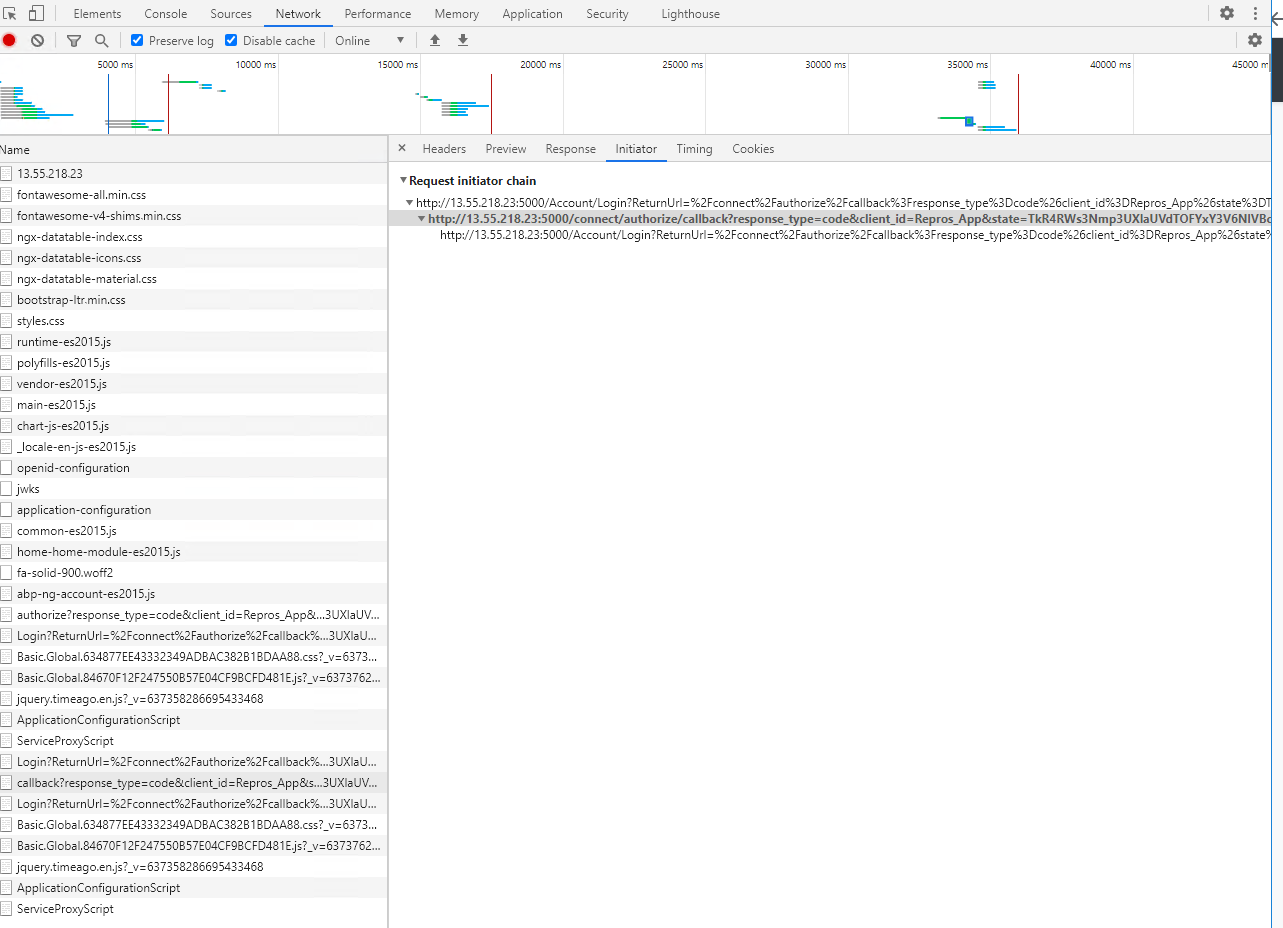
- Clicking login results in the progress bar across the top, and only one endpoint being hit. Nothing is logged in the Host service log file.
<br>
Lastly I know the http host is working as expected as I can see it being called in the initial home page load.
I don't see any errors or activity in the dev console, host log, or nginx log. The script just seems to stop.
I am uncertain as to where to even start with an error like this. The dev environment works correctly, even having parts of it (i.e. not ng serve) go through nginx.
I found that the requireHttps for oAuth was set to the default of everything but localhost requires. So I turned this off and started getting the following error in the chrome dev console:
invalid issuer in discovery document expected: http://<public_ip>:5000 current: http://<public_ip>
My nginx configuration should be allowing this through, so confused as to what is occurring here.
Hi,
The environment.prod.ts oAuthConfig has the following:
oAuthConfig: {
issuer: 'http://<public_ip>:5000',
redirectUri: baseUrl,
requireHttps: false,
clientId: 'Repros_App',
responseType: 'code',
scope: 'offline_access Repros',
},
Cheers
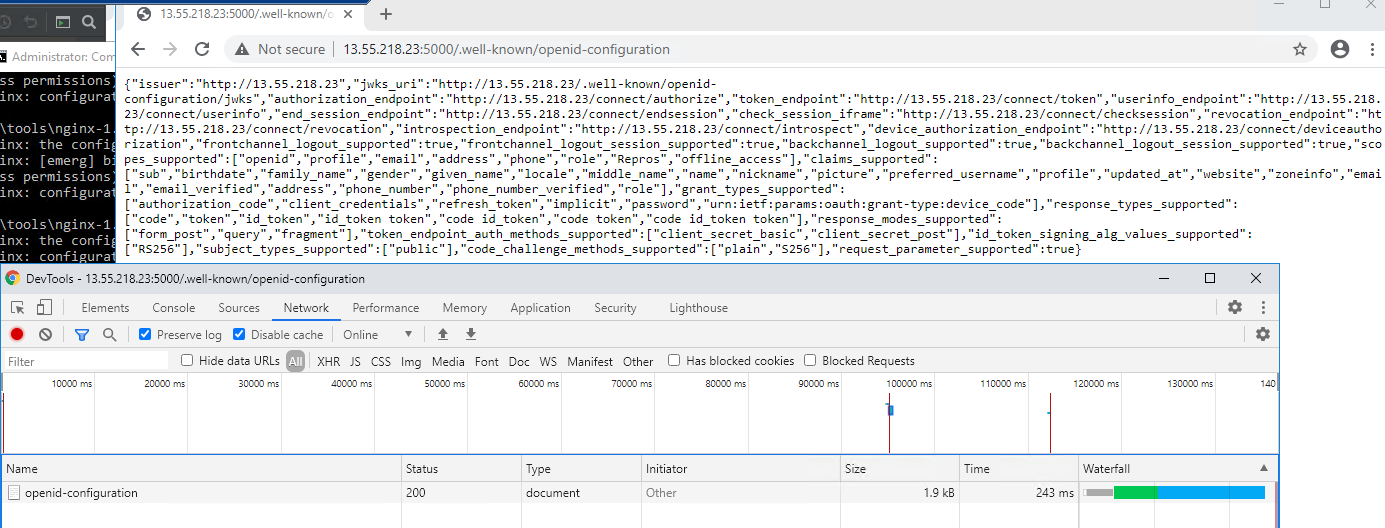
So it appears with the above setup I get the following from http://<public_ip>:5000/.well-known/openid-configuration.
{"issuer":"http://<public_ip>","jwks_uri":"http://<public_ip>/.well-known/openid-configuration/jwks","authorization_endpoint":"http://<public_ip>/connect/authorize","token_endpoint":"http://<public_ip>/connect/token","userinfo_endpoint":"http://<public_ip>/connect/userinfo","end_session_endpoint":"http://<public_ip>/connect/endsession","check_session_iframe":"http://<public_ip>/connect/checksession","revocation_endpoint":"http://<public_ip>/connect/revocation","introspection_endpoint":"http://<public_ip>/connect/introspect","device_authorization_endpoint":"http://<public_ip>/connect/deviceauthorization","frontchannel_logout_supported":true,"frontchannel_logout_session_supported":true,"backchannel_logout_supported":true,"backchannel_logout_session_supported":true,"scopes_supported":["openid","profile","email","address","phone","role","Repros","offline_access"],"claims_supported":["sub","birthdate","family_name","gender","given_name","locale","middle_name","name","nickname","picture","preferred_username","profile","updated_at","website","zoneinfo","email","email_verified","address","phone_number","phone_number_verified","role"],"grant_types_supported":["authorization_code","client_credentials","refresh_token","implicit","password","urn:ietf:params:oauth:grant-type:device_code"],"response_types_supported":["code","token","id_token","id_token token","code id_token","code token","code id_token token"],"response_modes_supported":["form_post","query","fragment"],"token_endpoint_auth_methods_supported":["client_secret_basic","client_secret_post"],"id_token_signing_alg_values_supported":["RS256"],"subject_types_supported":["public"],"code_challenge_methods_supported":["plain","S256"],"request_parameter_supported":true}
I am unsure as to what has made the service incorrrectly return the base address without port as the issuer. It also incorrectly sets the jwks url which makes subsequent requests fail even if validation of the configuration is turned off.
How do I get the authserver to return issue = http://<public_ip>:5000 instead of what its currrently doing?
Hi,
Thanks for the suggestion. I will try it.
This however does not address the issue that http://<public_ip>:5000/.well-known/openid-configuration is returning the wrong issuer (as its not hitting the Angular page, its the identity server). Do you have a template or suggested based Nginx configuration I could try?
Angular is configured correctly to specify the issuers as http://<public_ip>:5000 so that calls are directed to the service. The first call to the identity server is correct, however as the identity server returns the incorrect issuer and other url's subsequent calls are incorrect.
Cheers, Jason
Hi,
Sure. Caching is off, I get the same result.
Request on localhost correctly reports the port number for auth endpoints
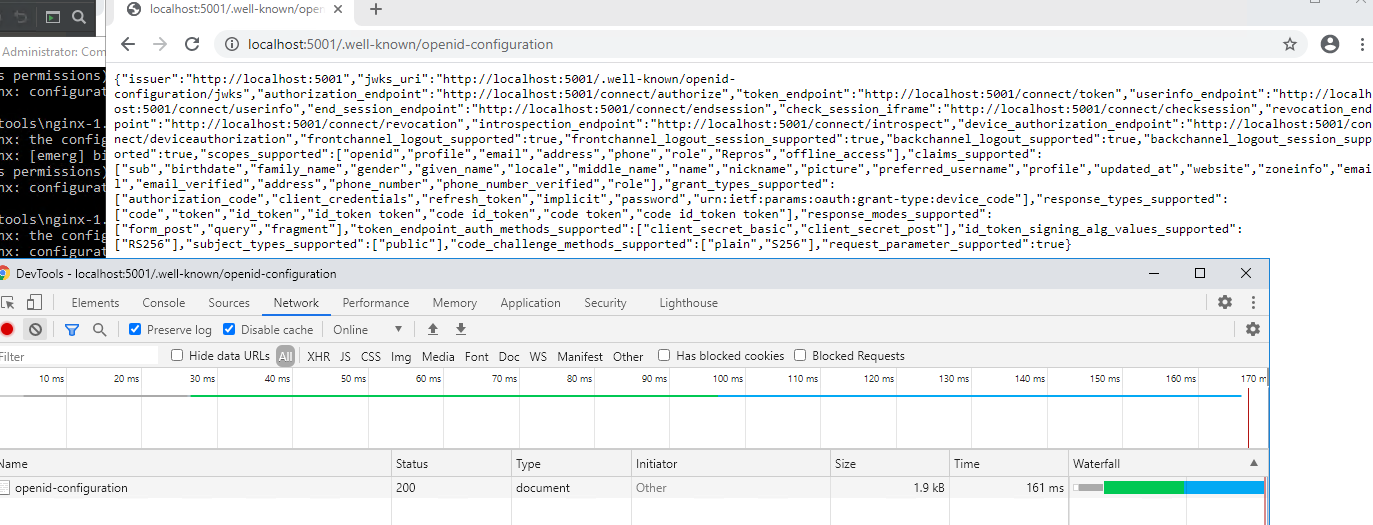
I must be missing something on the proxying inside Nginx and I am unsure as to what it is. At this point I am no longer concerned with the Angular frontend, it can't even get the indentity server to report its configuration correctly.
I have now changed ngnix config proxying for 5000 to have the line:
proxy_set_header Host $host:5000;
This has addressed the incorrect /.well-known/openid-configuration and I am able to get the login page now. The next issue is that login is not working. A valid user is simply returned to the same login screen.
So figured out what was going on. Turns out I am getting the samesite cookie issue on chrome.
https://community.abp.io/articles/patch-for-chrome-login-issue-identityserver4-samesite-cookie-problem-weypwp3n
I implemented the fix above and now the cookie correctly gets set.
Now we are onto the next issue. The user logs in, however is immediately redirected to the logout screen.
OK. Found what is occurring next. The fetchAndProcessToken from angular_oauth2-oidc.js is getting an invalid_grant response from tokenEndpoint. Turns out the token has timed out already. Looking at the auth service logs as to why.
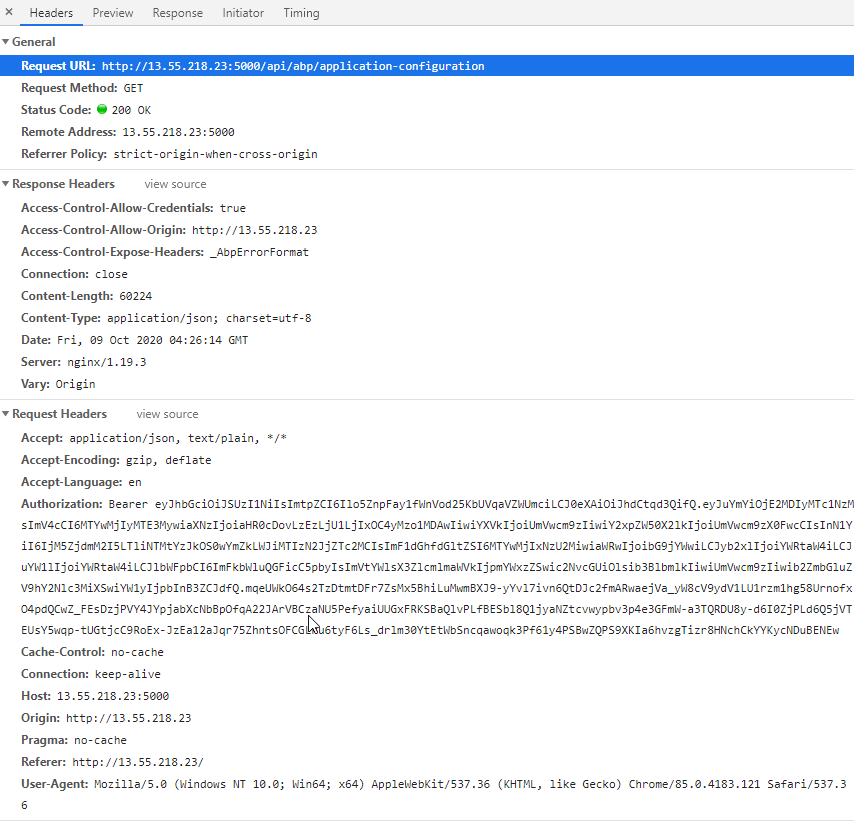
The next thing that we have diagnosed things down to is that the endpoint api/abp/application-configuration comes back with a currentUser object with nulls for each property. This means the current user id is not set causing a auto logout when the auth token is checked. The cookie looks to be correctly sent as well as the token. We are unsure why the response is coming back as it is.
Using Insomina on the same endpoint after logging in returns a valid currentUser object. Could this be another issue with the same-site cookie and not having https turned on for the service on port 5000?