Activities of "raif"
hi
error NU1101: Unable to find package Siemens.PSSX.Users.EntityFrameworkCore. N
o packages exist with this id in source(s): ABP Commercial NuGet Source,How can I restore this package?
Sorry my bad, I forgot this one.. I replaced this one with Volo's Users package and shared it again
hi
Request did not specify a service API version, but multiple candidate actions were found.
Can you share a simple project to reproduce?
liming.ma@volosoft.com
Sent
hi
siemens.pSSX.odms.models.v130.model;
This sample also uses the ajax to get the different results
https://github.com/abpframework/abp-samples/blob/master/Api-Versioning/host/BookStore.WebApp/Pages/Index.cshtml#L9-L35
https://github.com/abpframework/abp-samples/pull/126
As far as I see, my question is not understood clearly,
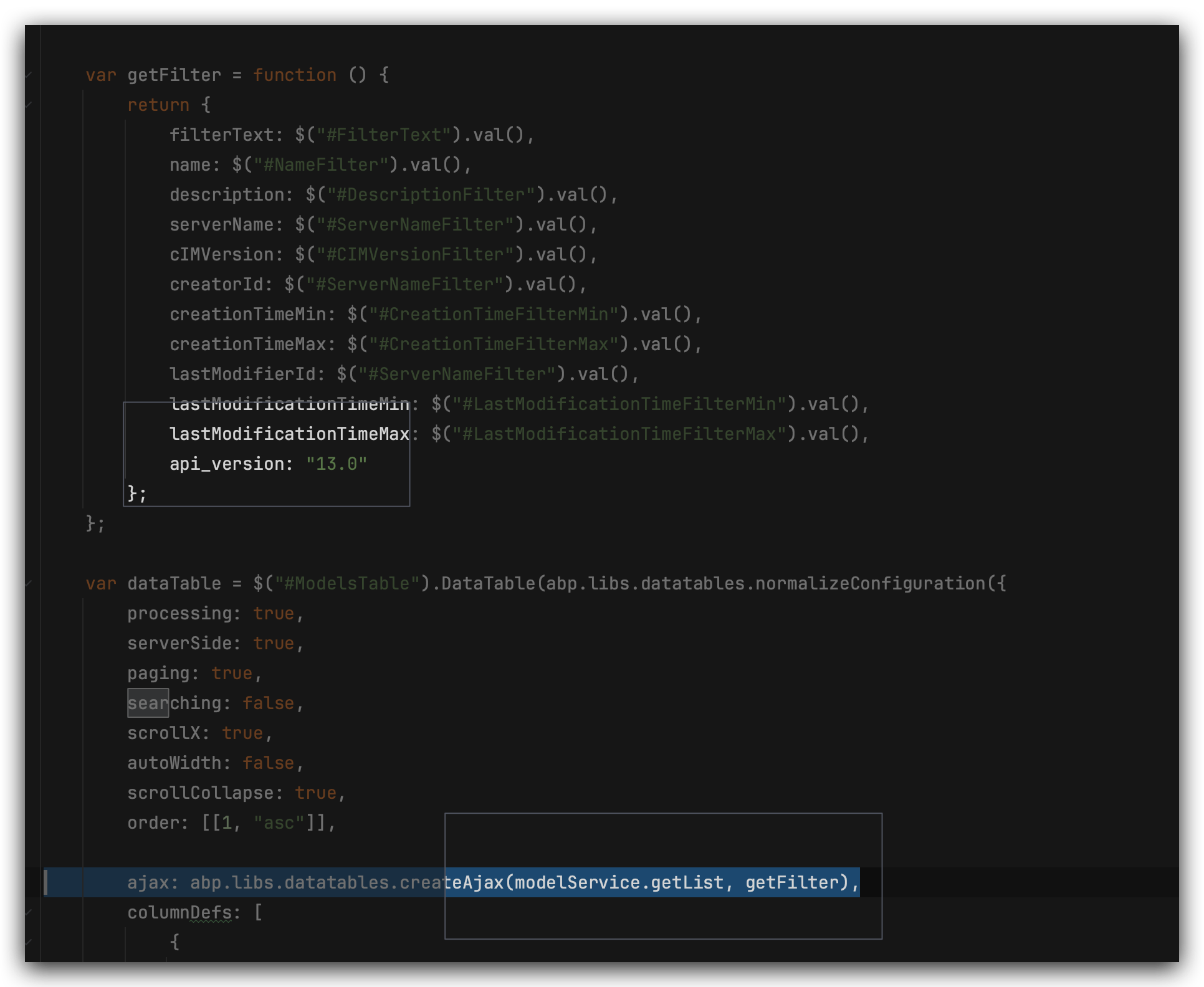
The examples above are not related to https://docs.abp.io/en/abp/latest/UI/AspNetCore/Data-Tables#ajax-adapter or I cannot make connection
ajax: abp.libs.datatables.createAjax(acme.bookStore.books.book.getList, inputAction, responseCallback)
If there is more than one version of acme.bookStore.books.book.getList, I encounter the following error.
Request did not specify a service API version, but multiple candidate actions were found.
acme.bookStore.books.book.getList('2.0') or similar approach doesn't help here
So what should we do here ?
Also sent entire log via e-mail;
AuthServer;
2023-03-16 12:53:09.035 +01:00 [INF] Executing endpoint 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc)' 2023-03-16 12:53:09.036 +01:00 [INF] Route matched with {area = "abp", action = "Get", controller = "AbpApplicationConfiguration", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto] GetAsync(Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationRequestOptions) on controller Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController (Volo.Abp.AspNetCore.Mvc). 2023-03-16 12:53:09.063 +01:00 [INF] Executing action method Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc) - Validation state: "Valid" 2023-03-16 12:53:09.065 +01:00 [DBG] Executing AbpApplicationConfigurationAppService.GetAsync()... 2023-03-16 12:53:09.096 +01:00 [DBG] Executed AbpApplicationConfigurationAppService.GetAsync(). 2023-03-16 12:53:09.097 +01:00 [INF] Executed action method Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc), returned result Microsoft.AspNetCore.Mvc.ObjectResult in 33.3081ms. 2023-03-16 12:53:09.097 +01:00 [DBG] Added 0 entity changes to the current audit log 2023-03-16 12:53:09.098 +01:00 [DBG] Added 0 entity changes to the current audit log 2023-03-16 12:53:09.099 +01:00 [INF] Executing ObjectResult, writing value of type 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto'. 2023-03-16 12:53:09.101 +01:00 [INF] Executed action Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc) in 65.0083ms 2023-03-16 12:53:09.101 +01:00 [INF] Executed endpoint 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc)' 2023-03-16 12:53:09.101 +01:00 [INF] Request finished HTTP/1.1 GET https://localhost:44374/api/abp/application-configuration?IncludeLocalizationResources=False&api-version=1.0 - - - 200 - application/json;+charset=utf-8 68.7130ms 2023-03-16 12:53:09.168 +01:00 [INF] Request starting HTTP/1.1 GET https://localhost:44374/api/abp/application-localization?CultureName=en&OnlyDynamics=True&api-version=1.0 - - 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ResolveServerConfiguration. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2023-03-16 12:53:09.169 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+Protection+ResolveTokenValidationParameters. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+Protection+ValidateIdentityModelToken. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+Protection+NormalizeScopeClaims. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+Protection+MapInternalClaims. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+Protection+ValidatePrincipal. 2023-03-16 12:53:09.170 +01:00 [INF] The authentication demand was rejected because the token was expired. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+Protection+ValidateExpirationDate. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was marked as rejected by OpenIddict.Validation.OpenIddictValidationHandlers+Protection+ValidateExpirationDate. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateAccessToken. 2023-03-16 12:53:09.170 +01:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was marked as rejected by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateAccessToken. 2023-03-16 12:53:09.170 +01:00 [INF] OpenIddict.Validation.AspNetCore was not authenticated. Failure message: An error occurred while authenticating the current request. 2023-03-16 12:53:09.170 +01:00 [INF] OpenIddict.Validation.AspNetCore was not authenticated. Failure message: An error occurred while authenticating the current request. 2023-03-16 12:53:09.171 +01:00 [INF] Executing endpoint 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationLocalizationController.GetAsync (Volo.Abp.AspNetCore.Mvc)'
Api Host;
2023-03-16 12:53:06.141 +01:00 [DBG] Batch acquisition of 0 triggers
2023-03-16 12:53:09.691 +01:00 [INF] Request starting HTTP/1.1 GET https://localhost:44319/api/project-planning/base-models/properties?Sorting=baseModel.name+asc&SkipCount=0&MaxResultCount=10&api-version=1.0 - -
2023-03-16 12:53:09.712 +01:00 [DBG] Acquiring a lock on 3b2efba2d4d943c6be4c79e83d238a72
2023-03-16 12:53:09.713 +01:00 [DBG] Lock acquired on 3b2efba2d4d943c6be4c79e83d238a72
2023-03-16 12:53:09.811 +01:00 [DBG] Found 0 workflows with correlation ID 3b2efba2d4d943c6be4c79e83d238a72
2023-03-16 12:53:09.811 +01:00 [DBG] Triggering workflows using HttpEndpoint
2023-03-16 12:53:09.860 +01:00 [INF] Failed to validate the token.
Microsoft.IdentityModel.Tokens.SecurityTokenExpiredException: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '3/16/2023 10:33:46 AM', Current time: '3/16/2023 11:53:09 AM'.
at Microsoft.IdentityModel.Tokens.Validators.ValidateLifetime(Nullable1 notBefore, Nullable1 expires, SecurityToken securityToken, TokenValidationParameters validationParameters)
at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateLifetime(Nullable1 notBefore, Nullable1 expires, JwtSecurityToken jwtToken, TokenValidationParameters validationParameters)
at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateTokenPayload(JwtSecurityToken jwtToken, TokenValidationParameters validationParameters, BaseConfiguration configuration)
at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateJWS(String token, TokenValidationParameters validationParameters, BaseConfiguration currentConfiguration, SecurityToken& signatureValidatedToken, ExceptionDispatchInfo& exceptionThrown)
--- End of stack trace from previous location ---
at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateToken(String token, JwtSecurityToken outerToken, TokenValidationParameters validationParameters, SecurityToken& signatureValidatedToken)
at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateToken(String token, TokenValidationParameters validationParameters, SecurityToken& validatedToken)
at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.HandleAuthenticateAsync()
2023-03-16 12:53:09.864 +01:00 [INF] Bearer was not authenticated. Failure message: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '3/16/2023 10:33:46 AM', Current time: '3/16/2023 11:53:09 AM'.
2023-03-16 12:53:09.919 +01:00 [INF] Executing endpoint 'Siemens.PSSX.ProjectPlanning.BaseModels.v1.BaseModelController.GetListWithNavigationPropertiesAsync (Siemens.PSSX.ProjectPlanning.HttpApi)'
2023-03-16 12:53:09.922 +01:00 [INF] Route matched with {controller = "Base Models", action = "GetListWithNavigationProperties", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task1[Volo.Abp.Application.Dtos.PagedResultDto1[Siemens.PSSX.ProjectPlanning.BaseModels.v1.Dtos.BaseModelWithNavigationPropertiesDto]] GetListWithNavigationPropertiesAsync(Siemens.PSSX.ProjectPlanning.BaseModels.v1.Dtos.GetBaseModelWithNavigationPropertiesInput) on controller Siemens.PSSX.ProjectPlanning.BaseModels.v1.BaseModelController (Siemens.PSSX.ProjectPlanning.HttpApi).
2023-03-16 12:53:10.006 +01:00 [INF] Executing action method Siemens.PSSX.ProjectPlanning.BaseModels.v1.BaseModelController.GetListWithNavigationPropertiesAsync (Siemens.PSSX.ProjectPlanning.HttpApi) - Validation state: "Valid"
2023-03-16 12:53:10.027 +01:00 [INF] Authorization failed. These requirements were not met:
PermissionRequirement: ProjectPlanning.BaseModel
2023-03-16 12:53:10.166 +01:00 [WRN] ---------- RemoteServiceErrorInfo ----------
{
"code": "Volo.Authorization:010001",
"message": "Authorization failed! Given policy has not granted.",
"details": null,
"data": {},
"validationErrors": null
}
Create extension for CurrentUser in order to get OrganizationIds from token.
public static class CurrentUserExtensions
{
public static string[] GetOrganizationUnits(this ICurrentUser currentUser)
{
Claim[] claims = currentUser.FindClaims("organization_unit");
return claims.Select(c => c.Value).ToArray();
}
}
Add query filters for EF Core
protected override bool ShouldFilterEntity< TEntity >(IMutableEntityType entityType)
{
if (typeof(IHasAccessControl).IsAssignableFrom(typeof(TEntity)))
{
return true;
}
return base.ShouldFilterEntity< TEntity >(entityType);
}
protected override Expression< Func< TEntity, bool > > CreateFilterExpression< TEntity >()
{
var expression = base.CreateFilterExpression< TEntity >();
if (typeof(IHasAccessControl).IsAssignableFrom(typeof(TEntity)))
{
Expression< Func < TEntity, bool > > hasAccessControlFilter = e => CurrentUser.GetOrganizationUnits().Contains(EF.Property< string >(e, "OrganizationId")) || CurrentUser.Id == (EF.Property< string >(e, "OwnerId"));
expression = expression == null ? hasAccessControlFilter : CombineExpressions(expression, hasAccessControlFilter);
}
return expression;
}
Let suppose we have microservices A and B. A for identity, auditing, saas etc, basic IT needs Where B is business microservice.
After creating a new "project" object in microservice B, I want to assign it to a specific person or a specific organizational unit. (see global filter implementation)
So we needed lookup values for organization units (it can be logins, tokens, roles, claims for another use cases)
Information exchange between A and B can be
- Synchronous
- Asynchronous (in this specific case data can flow one way)
Again let assume that we would like keep asynchronous communication where we were using UserEtos
So, every time the user is updated in microservice A, I want to update the user information in microservice B via distributed events.
However UserEto's doesn't carry information about
- Claims
- Roles
- Logins
- Tokens
- Organization Units
So how can we access asynchronously the above information about the user ?
UserLookupService from Volo.Abp.Users package only forces IUser interface which is doesn't force claims, roles, tokens, ou etc..
public abstract class UserLookupService<TUser, TUserRepository> : IUserLookupService<TUser>, ITransientDependency where TUser : class, IUser where TUserRepository : IUserRepository<TUser>
OU and roles are mainly used to organize permissions and your module should only need to the permission system dependency (it already has). These details are internals of the Identity module.
I think permission system dependency looks enough if you are building "policy based" authorization but not "row level" authorization.
Let's assume use case where we are adding query filters according users organization unit detail. We may want to the user access more or less data according to their hierarchy in the organizational unit. Policy authorized one end point should return all organizational units lookup values for assignment.
Let's define interface for this;
public interface IHasAccessControl
{
public string OwnerId { get; }
public string OrganizationId { get; }
}
Implement interface to the Aggregate Root
public class Project : AuditedAggregateRoot<Guid>, IMultiTenant, IHasAccessControl
{
public virtual string Name { get; protected set; }
// ...
public virtual Guid? TenantId { get; protected set; }
public virtual string OwnerId { get; protected set; }
public virtual string OrganizationId { get; protected set; }
public virtual void SetOwnerId([NotNull] string ownerId)
{
}
public virtual void SetOrganizationId([NotNull] string organizationId)
{
}
}
Let's add organization id information to the token.
public class OrganizationUnitPrincipalContributor : IAbpClaimsPrincipalContributor, ITransientDependency
{
public async Task ContributeAsync(AbpClaimsPrincipalContributorContext context)
{
var identity = context.ClaimsPrincipal.Identities.FirstOrDefault();
var userId = identity?.FindUserId();
if (userId.HasValue)
{
var userService = context.ServiceProvider.GetRequiredService< IdentityUserManager >();
var user = await userService.FindByIdAsync(userId.ToString());
if (user != null)
{
user.OrganizationUnits
.Select(u => u.OrganizationUnitId).ToList()
.ForEach(unit => identity.AddClaim(new Claim(type: "organization_unit", value: unit.ToString())));
}
}
}
}
Add short cut for identityServer (https://github.com/abpframework/abp/pull/7998)
Configure<AbpClaimsServiceOptions>(options =>
{
options.RequestedClaims.AddRange(new[] { "organization_unit" });
});
Ok thx after login it is working again, but I didn't perform any "log out" operation ? Do we need to refresh our login time to time ? Is there any kind of necessity ?